June 20, 2006
New Antispam Product Reviews
We've just completed a two week test of several antispam products and the hands down winner in our test was Spam Bully. This category of software has not been as popular over the past couple of years, so there has been little in the way of product improvement. Spam Bully seems to be the exception. Read our review here.
June 12, 2006
How to disable Microsoft's Windows Genuine Advantage From Spying On You
1. End the process wgtray.exe from the "Processes" tab on the Task Manager Manager (press ctrl-alt-delete to bring it up.)
2. Restart Windows XP in safe mode by rebooting and pressing F8 while it's starting.
3. Delete the following files:
c:\windows\system32\wgatray.exe
c:\windows\system32\dllcache\wgatray.exe
4. Start Windows Regsitry Editor and delete the following entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ Windows NT\CurrentVersion\WinlogonNotify\WGALOGON
At this point, your private data will no longer be sent to Microsoft every time you start your PC.
June 09, 2006
Windows Genuine Advantage: Safety Switch or Spyware?
Editor's Note: Few in the anti-spyware industry would disagree that software which surreptitiously calls home qualifies as "spyware". However Microsoft, makers of Windows Defender, has has just been caught red-handed distributing software which does exactly this.
One of the major objections raised about Microsoft's foray into PC security is that competing interests within the company will compromise the level of security they are willing to provide. This is a particularly good example of how the company continues to trample over itself, simultaneously acting as anti-spyware provider as well as a spyware company.
It is because of this conflict-of-interest that I no longer run Microsoft's security products. No matter how good their products may seem, it is just a matter of time before some internal directive results in a massive security hole on my PC. My data is just too important to expose to the corporate whims of a company too big to act in a coordinated manner.
Rumors have been flowing around the Internet for quite a while and Microsoft was finally forced to admit on Wednesday that they were true: the latest update to Windows Genuine Advantage (WGA) phones home to the Redmond company on a daily basis.
Windows Genuine Advantage is an anti-piracy program implemented to detect illegal copies of Windows XP.
According to privacy advocate Lauren Weinstein, the WGA made a connection to Microsoft's servers even after it had validated a Windows system as genuine.
"We can argue about whether or not the tool's behavior is really spyware -- there are various definitions for spyware, and the question of whether or not you feel that the notice provided at upgrade installation time was sufficient is also directly relevant I believe that the MS officials I spoke to agree with my assertion that additional clarity and a more "in your face" aspect to these notifications in such cases would be highly desirable."
In response, Microsoft said that the feature was a "safety switch", designed to enable the company to shut down the program in case of a problem. The company added that it would provide an update for the WGA so the computers would only call home every 90 days.
Up till now the anti-piracy tool has been a success form Microsoft's point of view, as the company claims that 60% of users promoted to install WGA did so.
However, users have become concerned, as the situation brought up the an uneasy question: What else is Microsoft not telling us?
Lauren Weinstein wrote on his blog:
"I do not know what data is being sent to MS or is being received during these connections. I cannot locate any information in the MS descriptions to indicate that the tool would notify MS each time I booted a valid system. I fail to see where Microsoft has a "need to know" for this data after a system's validity has already been established, and there may clearly be organizations with security concerns regarding the communication of boot-time information."
Many fear Microsoft's idea would be embraced by other software vendors, leading to more and more restrictions the customers would have to accept in order to be able to use the product. Also, the matter of invasion of privacy arose, as such tools would eventually be allowed to send all kind of info to the developer of the software.
June 08, 2006
Man pays US$2,000 after charges of Google AdWord misuse
Editor's Note: We reviewed Spyware Cleaner nearly a year ago and warned users about this ineffective product.
Robert McMillan, IDG News Service
A New Hampshire man has agreed to pay US$2,000 to settle charges that he misused Microsoft's name to trick consumers into buying ineffective antispyware products, using Google's AdWords program.
Seth Traub, of Portsmouth, New Hampshire, is the third person to settle a lawsuit filed in January by Microsoft and the Washington State Attorney General's office. The suit alleges that software vendor Secure Computer sold an antispyware product that not only fails to remove spyware as advertised, but actually makes users' computers less secure.
Traub and two others, Zhijian Chen of Portland, Oregon, and Manoj Kumar of Maharashtra, India, were charged with using inappropriate techniques to advertise Secure Computer's Spyware Cleaner software. Last April, Chen paid US$84,000 in fines after pleading guilty to violating Washington's Computer Spyware Act.
A fourth man, Gary Preston, of New York state, has paid US$7,200 after allegedly allowing his name to be used as an alias by Secure Computer.
Traub ran ads, using Google's AdWords program to create an advertising link reading "Microsoft AntiSpyware." It was displayed when users searched for terms like "Microsoft spyware cleaner," or "Microsoft antispyware," the Attorney General said in a statement Tuesday.
Traub's ads earned him 75 percent of the US$49.95 unsuspecting users would spend to purchase a copy of Spyware Cleaner.
Traub has not admitted any wrongdoing in the settlement, which was finalized Monday, but will pay US$2,000 in legal costs and attorney's fees, the Attorney General's office said.
The lawsuit against Secure Computer and its president, Paul Burke, is ongoing. It is the first to be filed under Washington's 2005 Computer Spyware Act.
May 30, 2006
Tougher days looming for anti-spyware leader Webroot
Sunday, May 28, 2006
By Catherine Tsai, The Associated Press
BOULDER, Colorado -- For millions of PC users, the privacy-snatching programs known as spyware have been nothing but a headache as they swipe personal information, slow systems to a crawl and crash computers.
For Webroot Software Inc., the annoying programs have been the foundation of success. Thanks to its market-leading anti-spyware software, Spy Sweeper, sales have soared 20-fold since 2002, and last year the privately held company raised an eye-popping $108 million in venture capital.
Though there's little chance of spyware ever going away, Webroot is facing a significant challenge in the coming years: Microsoft Corp.'s upcoming Windows Vista operating system will include its own spyware-squashing tools.
Vista could put Webroot in the same shoes as RealNetworks Inc., Netscape Communications Corp. and others whose businesses have suffered after Microsoft bundled more features into its ubiquitous operating system.
Still, Webroot CEO David Moll seems unfazed.
"The taking of a second-best product in this space is akin to locking half the doors in your house," he said. "Vista will not solve the spyware problem. It may change the vector of attack, but it will not solve this problem. And I'll bet the company on it."
Some analysts say the company should broaden its focus -- and Moll, without divulging details, said that's in the plans.
"Ultimately they need to offer more than just an anti-spyware package," Yankee Group senior analyst Andrew Jaquith said. "To do that, they need access to more money, or be part of a bigger company."
Moll said he expects 20 percent revenue growth this year, while Jaquith estimates current overall annual revenue at $75 million to $110 million. Mr. Jaquith said an initial public offering is more likely than a buyout because, he estimates, it could take $500 million to acquire the company -- a sum he figured few rivals would be willing to pay.
Although an initial public offering isn't imminent, Mr. Moll said, Webroot is implementing some of the financial controls required for public companies.
Even before Vista ships to businesses later this year and to consumers in early 2007, Webroot faces formidable competition.
Anti-spyware programs from companies like Tenebril Inc., Lavasoft AB, McAfee Inc. and others all target the software that gets downloaded and installed onto PCs -- often without users' knowledge -- to monitor keystrokes or capture personal data and send it back to a third party.
Some of the rival programs are free, while others are included with broader security programs. Webroot charges $29.95 for the software and a year of updates and customer support.
Spy Sweeper, which was first released in 2003, has received strong reviews and it had 75 percent of the U.S. retail market last year for anti-spyware, besting both McAfee and Computer Associates International Inc., according to the NPD Group Inc., a market research firm.
For its part, Microsoft said customers should choose spyware protection that works best for them. In fact, Vista users will be able to turn off Windows Defender, if they choose, said Mike Chan, senior product manager for the anti-spyware program.
Many anti-spyware vendors set traps, or "honey pots," with algorithms that do the screening. Webroot's differentiator is Phileas, a computer system that actively hunts down spyware with the aim of catching new threats the day they are released.
To spark further innovation, Webroot employees who think of ideas that earn patents get bonuses of up to $2,000. Every so often, the company holds the "Spyware Smackdown," a game in which researchers act as spyware writers trying to avoid Spy Sweeper.
The company also invested $500,000 on a usability lab, in which cameras monitor volunteers as they use Webroot's software. That research then goes into improving the software's interface.
Webroot's efforts have paid off. Besides huge revenue growth helped by the release of Spy Sweeper in 2003, the company has grown from about a dozen employees to 300 in a purple-walled headquarters that look out on the Rocky Mountains. Its conference rooms are named for dead rock stars such as Jerry Garcia.
Though Vista raises a cloud around Webroot's continued success, the company is no stranger to escaping threats.
The company was launched in 1997 by Steve Thomas and then-girlfriend Kristen Talley. Thomas was a state chess champion at age 10 who landed on an FBI watch list at age 14 after he hacked into a supercomputer at the National Center for Atmospheric Research, Moll said.
After the couple's relationship soured and sales plateaued at a few million dollars, Thomas and Talley in April 2002 hired Mr. Moll, a Duke University dropout who once worked at a screw machine factory in Cleveland to pay his way through night school.
At the time, Webroot sold a program for cleaning up unnecessary files on PCs, and revenues came evenly from Internet sales, AOL's Shop Direct and retail.
Just months after Mr. Moll joined, AOL went through a management change and strategy shift and it shut down sales through Shop Direct. Moll, Thomas and Talley stopped taking paychecks, but by then Webroot was developing Spy Sweeper. The program came to market in February 2003.
May 10, 2006
The third time was not a charm...
Spyware soared in the first quarter this year - infecting an estimated 87 percent of consumers' PCs, according to security firm Webroot, which released its State of Spyware report Tuesday.
That's quiet a pop from the previous two quarters, when spyware had infected an estimated 72 percent of consumer PCs, according to Gerhard Eschelbeck, Webroot chief technology officer.
Webroot's CTO pointed to three things that drove the rapid rise of spyware in the first quarter. Topping the list was the flurry of IE flaws in the quarter that didn't have a patch available at the time they were disclosed. Greater sophistication of rootkits and a resurgence in building blocks to make phishing Trojan horses also added fuel to the fire for spyware.
And don't expect things to improve anytime soon. Eschelbeck estimates the infection rate for PCs will be in the 85 percent and 90 percent range for the rest of the year.
May 07, 2006
FTC Orders Spyware Operator To Pay $4 Million
Federal Trade Comission ordered Sanford Wallace to pay back more than $4 million that he made by selling a anti-spyware software that fixes imaginary problems. Wallace and his SmartBOT company were selling two purported anti-spyware programs Spy Wiper and Spy Deleter.
According to FTC, Sanford Wallace exploited an Internet Explorer vulnerability, making users to believe that their computers are infected. The real spyware included a small program that opened the CD-ROM tray and displayed the message "If your cd-rom drives open . . .You DESPERATELY NEED to rid your system of spyware pop-ups IMMEDIATELY! Spyware programmers can control your computer hardware if you failed to protect your computer right at this moment! Download Spy Wiper NOW!
The Spy Wiper and Spy Deleter were sold for $30. FTC accused Wallace for spyware operations in 2004.
The order, issued by the U.S. District Court in New Hampshire, also bars Wallace and his company from:
-- Downloading spyware and any software onto consumers computers without consent;
-- Redirecting consumers' computers to sites or servers other than those the consumers selected to visit;
-- Changing any Web browsers default home page. A settlement with defendants OptinTrade and Jared Lansky prohibits the same practices. Lansky, an ad broker who distributed ads containing Wallace's spyware, will give up $227,000 in spyware-related profits.
In the 1990s Wallace was known as "Spamford" or "Spam King" because he headed a company, Cyber Promotions, that sent as many as 30 million junk e-mails daily to consumers.
Warning! This fake cure for SpyAxe will infect your computer!
And the SpyAxe saga continues...
This time it appears that a number of individuals are recommending a "cure" for SpyAxe on various internet forums (Example #1, Example #2). This downloadable file, cmer_uninstallers.zip, does not remove SpyAxe. While it does disable the SpyAxe popup, it also installs a trojan horse (trojan.zlob) on your computer. This trojan can be used to install other software such as spyware or viruses in the future.
The source of this file is none other than the makers of SpyAxe. Adware Report readers were first alerted to this fake cure in January. If you've downloaded and have run this file on your computer, you should immediately download and run a reputable anti-spyware program.
Thanks to Jason Boudreau for this tip!
May 01, 2006
Most Web Users Unable to Spot Spyware
By Sophia Mayengbam
Asia Magazine
Most internet users are attracted with clean appealing graphics and advertisements, thus falling in the trap of spyware. According to the a Spyware Quiz conducted by McAfee SiteAdvisor a staggering 97 percent of Internet users are just one click away from infecting their PCs with spyware, adware.
Most internet users are attracted with clean appealing graphics and advertisements, thus falling in the trap of spyware. According to the a Spyware Quiz conducted by McAfee SiteAdvisor a staggering 97 percent of Internet users are just one click away from infecting their PCs with spyware, adware or some other kind of unwanted software. Even though the threat of spyware has received extensive media coverage, just 3 percent of the 14,000-plus consumers who took SiteAdvisor's spyware quiz received perfect scores.
The survey challenged Web surfers to test their ability to detect which sites in a number of popular categories were free of adware or spyware. The examples in the quiz are taken from more than three million Web sites which SiteAdvisor has independently tested and rated for Web safety issues like spyware and spam. The first part of the quiz presented users with pairs of sites and asked them to pick which one of the pair was safe. The second part presented a series of file sharing software sites and asked which ones were spyware and adware free.
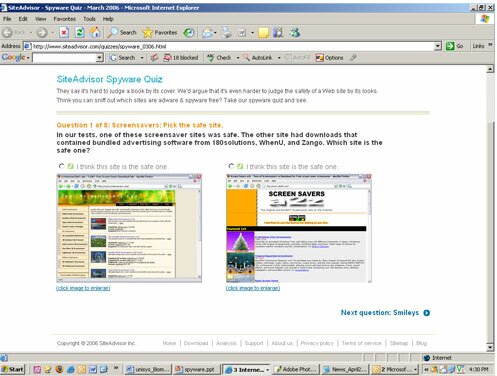
Fig. 1: SiteAdvisor Spyware Quiz Webpage 1

Fig. 2: SiteAdvisor Spyware Quiz Webpage 2
The ones in the survey were chosen from three million sites already tested and given a safety rating. Sites were selected from popular categories -- screensavers, smileys, free games, song lyrics, and file-sharing applications -- all of which are also notorious for distributing spyware, adware and other unwanted programs. The quiz was specifically designed to determine how adept users are at visually detecting the potential for intrusive downloads on a site.
Survey Results:
The survey found that based on their choices majority of the users (65 percent) chose would have been infected with adware or spyware many times over. Respondent easily fall in the prey of national advertisers and a clean and uncluttered design. Users often miss the fine print that allows a dangerous Web site to claim it installs unwanted software legally. Even users with high Spyware IQ have nerly 100 percent chance of visiting a dangerous site during 30 days of typical online searching and browsing activity.
The Percent of Consumers Able to Correctly Determine a Web Site's Safety is shown in the Pie Chart below:
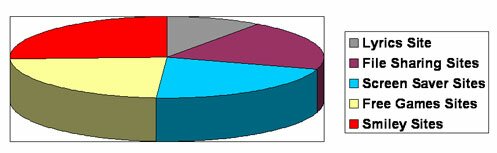
Respondent did particularly poorly on the pair of lyrics sites. One possible reason is the unsafe site had advertising from well-known brands like Circuit City and Monster.com that may have served to legitimise it.
"We know it's not easy to judge a site's safety just by looking at it, but that's the point: Bad sites are often very good at providing an aura of safety," said Chris Dixon, who heads McAfee's SiteAdvisor development. "No matter how knowledgeable or perceptive you are, you can't rely on your instincts alone. Another important take-away that people sometimes forget is that there ARE safe sites, even in these often abused categories."
April 26, 2006
Spyware evolving faster than viruses
Darwinism in action as malicious software proliferates
Iain Thomson at Infosec, vnunet.com 26 Apr 2006
Adware Report Editor's Note: We recently saw this in action with SpyAxe and its many variants. This is why it's more important than ever to use a spyware remover from a company that provides frequent updates.
The evolution of spyware is outpacing that of viruses, with some software resetting itself hourly to evade detection, security experts warned today at Infosec Europe.
Security firm Webroot recorded a dramatic rise in spyware in the past 12 months, almost all of it aimed at harvesting financial data that could be used by third parties.
Experts have also warned that the next target for such malware will be VoIP applications such as Skype.
"Voice is definitely the next attack vector. But this time the malware writers won't use it for financial gain but for stealing intellectual property, " said Gerhard Eschelbeck, chief technology officer at Webroot and founder of vulnerability testing firm Qualys.
Eschelbeck claims to have identified significant changes in the way spyware is being developed compared to viruses.
Viruses tend to be developed and distributed by individuals before being used by third parties. Spyware, on the other hand, is typically developed by teams working to order and learns the lessons of viruses.
Some code even resets sections of itself every hour in an effort to fool signature-based security software.
'Build your own spyware' kits are already commonplace on the internet in publicly available forums, leading to fears that 'script kiddies', technically unsophisticated users, could develop and distribute their own malware.
Eschelbeck added that his company had seen a 40 per cent rise in the amount of spyware in circulation over the past three months, and warned that the availability of spyware kits will fuel further rises.
Original post at VuNet.com
April 11, 2006
Registry Mechanic review now online
We occasionally receive requests to review software other than anti-spyware products. We've resisted this for awhile because sometimes these programs are difficult to test (and we like to have numbers to back our reviews up).
However, we tried a utility this weekend that we really liked and devised a test around it. The program is called Registry Mechanic and it worked wonders on a few computers around here.
Should we continue to review utilities other than antispyware? Let us know what you think! And be sure to let us know of any other utilities that you feel deserve a look. If they turn out to be effective, we'll share them with the world.
The Registry Mechanic review can be found here.
April 10, 2006
Webroot not 3x as effective as Counterspy
In a recent press release, Webroot claimed that independent testing showed their product was three times as effective as Counterspy and McAfee. While our testing results verified that this is true in regards to McAfee, the same test showed that Counterspy was slightly more effective than Webroot.
See our results for Webroot and Counterspy here.
April 05, 2006
Update on Webroot Effectiveness Claims
In a previous article, we cited independent testing conducted by VeriTest that claimed Webroot's Spy Sweeper was 3x as effective as McAfee AntiSpyware.
Our latest results have not only confirmed their results, we found that Webroot was 5x more effective than the latest version of McAfee.
April 02, 2006
Spyware becoming a riskier business for perpetrators...
Setting a precedent that will be welcomed by many, a criminal case has been filed against officers of Enternet Media, a California based spyware company:
It is the first criminal spyware case filed in the state of California. The charges include conspiracy, 24 violations of unauthorized access to computers and four counts of false advertising. If found guilty, the penalties could include up to 25 years in prison and fines of up to $170,000.The defendants, Lida Rohbani Hakimi, Nima Hakimi and Baback Hakimi, are charged with running companies that created spyware programs such as toolbars and fictitious "security programs," that would insinuate themselves into a computer during the download of seemingly innocuous software, like music files. The toolbars would then track users Internet activity and transmit data back to Enternet.
The FTC shut down Enterprise in November, 2005. Their statement:
An operation that uses the lure of free lyric files, browser upgrades, and ring tones to download spyware and adware on consumers computers has been ordered to halt its illegal downloads by a U.S. District Court at the request of the Federal Trade Commission. The court also halted the deceptive downloads of an affiliate who helped spread the malicious software by offering blogs free background music. The music code downloaded by the blogs was bundled with a program that flashed warnings to consumers who visited the blog sites about the security of their computer systems. Consumers who opted to upgrade by clicking, downloaded the spyware onto their computers. The court has frozen the organizations assets pending a further hearing. The FTC will seek to bar the deceptive and unfair practices permanently and require the operators to give up their ill-gotten gains.The FTC complaint alleges that the Web sites of the defendants and their affiliates cause installation boxes to pop up on consumers computer screens. In one variation of the scheme, the installation boxes offer a variety of freeware, including music files, cell phone ring tones, photographs, wallpaper, and song lyrics. In another, the boxes warn that consumers Internet browsers are defective, and claim to offer free browser upgrades or security patches. Consumers who download the supposed freeware or security upgrades do not receive what they are promised; instead, their computers are infected with spyware.
The agencys complaint alleges that the defendants software code tracks consumers Internet comings and goings; changes consumers preferred home page settings; inserts new toolbars onto consumers browsers; inserts a large side frameor window onto consumers browser windows that in turn displays ads; and displays pop-up ads on consumers computer screens, even when consumers Internet browsers are not activated. In addition, the agency alleges that once the spyware is loaded on consumers computers, it interferes with the functioning of the computer and is difficult for consumers to uninstall or remove.
The FTC alleges the practices are unfair and deceptive and violate the FTC Act. The agency will seek a permanent ban on the practices, and redress for consumers.
This case was brought with the invaluable assistance of the Microsoft Corporation, Webroot Software, Inc., and Google Incorporated.
Defendants named in the FTC complaint are Enternet Media, Inc.; Conspy & Co., Inc., Lida Rohbani, also known as Linda Rohhani and Lida Hakimi; Nima Hakimi; Baback (Babak) Hakimi, also known as Bobby Rohbani and Bobby Hakimi, individually and doing business as Networld One, all based in California which used exploitative code called: Search Miracle, Miracle Search, EM Toolbar, EliteBar, and Elite Toolbar. The defendants do business as Enternet Media, Inc., Enternet, www.searchmiracle.com, www.c4tdownload.com, and www.cash4toolbar.com. The affiliate, also charged in the complaint, is Nicholas C. Albert, doing business as Iwebtunes and www.iwebtunes.com, based in Ohio.
The FTC has set up two ways for consumers who have had experience with these defendants to contact the FTC with any information that may be relevant to the FTCs action. Consumers can send email to [email protected] or call 202-326-2992 to leave messages.
The Commission vote to file the complaint was 4-0. It was filed in U.S. District Court for the Central District of California, in Los Angeles.
Steps consumers can take to reduce their risk of spyware infection include:
* Update your operating system and Web browser software, and set your browser security high enough to detect unauthorized downloads.
* Use anti-virus software and a firewall, and keep them up-to-date.
* Download free software only from sites you know and trust. Enticing free software downloads frequently bundle other software, including spyware.
* Dont click on links inside pop-up windows.
* Dont click on links in spam that claim to offer anti-spyware software; you may unintentionally be installing spyware.
* Consider using anti-spyware software.
March 29, 2006
Latest testing results of Aluria Antispyware and Webroot Spy Sweeper Now Available
Aluria Antispyware and Webroot Spy Sweeper results are now available by accessing their individual review pages. We haven't completed our monthly tests of McAfee or Counterspy yet, so we don't know if there is any truth to Webroot's recent press release. But we'll know in a few days.
Overall, we're seeing a bit of a decline in performance this month due to the addition of a number of recent spyware threats to our test. One exception is PC Tools' Spyware Doctor, which has turned in a very impressive performance.
March 28, 2006
Webroot Claims Three Times As Effective as Sunbelt, McAfee
Webroot reported that its testing by VeriTest shows that its spyware cleaning tool is three times as effective as competition from Sunbelt, and twice as effective as tools from McAfee. Webroot said that its tool fully cleaned 94 percent of the test bed, versus only 53 percent for McAfee and 26 percent for Sunbelt. VeriTest is an independent test lab, which typically tests software for clients such as Webroot.
Independent tests from AdwareReport will be coming out in a few days...
March 26, 2006
New Reviews Have Been Posted
Updated reviews and testing results of the following products have been posted:
Spyware Doctor
Microsoft Windows Defender
StopZilla!
Ewido AntiMalware
More coming in the next few days...
March 25, 2006
IE Exploit Strikes, Installs Spyware
By Gregg Keizer, TechWeb News
The unpatched CreateTextRange vulnerability in Internet Explorer is already being used by at least one Web site to install spyware on users' machines, a security organization said Friday.
"We just received a report that a particular site uses the vulnerability to install a spybot variant," the SANS Institute's Internet Storm Center (ISC) warned Friday in an alert. "It is a minor site with insignificant visitor numbers according to Netcraft's 'Site rank.'"
Disclosed only Wednesday, the flaw in IE 5.01, 6.0, and the January version of IE 7 Beta 2 Preview has security vendors worried because a patch isn't available from Microsoft. Thursday, as news circulated that a working exploit had been publicly posted, Microsoft said it was working on a fix.
Even before the site exploiting the CreateTextRange bug was discovered, security companies had raised alarms. The ISC bumped up its InfoCON level to "yellow" for the first time since the Windows Metafile fiasco in late December, when another "zero-day" flaw hit Windows users.
"It's a relatively trivial mod[ification] to turn [the exploit] into something more destructive," the ISC warned. "For that reason, we're raising Infocon to yellow for the next 24 hours."
Symantec raised its ThreatCon status indicator to "2" and boosted its Internet Threat Meter's warning for Web activities to "medium" because of the bug.
Although it's unclear exactly whether the Spybot-distributing site is drawing users to its poison or simply waiting for the unwary to stumble across the URL, it's likely the former, Scott Carpenter, director of security at Secure Elements, said in an e-mail to TechWeb. "The most probable vector for this worm will be in the form of spam with malicious links that will tempt users into clicking on a link that takes them to a malicious site."
In December (and after), hundreds of sites used the Windows Metafile bug to load spyware, including keyloggers and backdoor Trojans, onto unsuspecting users' PCs.
Rumors that Microsoft would release a patch before April 11, the next regularly-scheduled patch day -- such releases are dubbed "out-of-cycle" -- was quashed by a Microsoft spokesman who refused to commit the company to a date.
"Upon completion of this investigation, Microsoft will take appropriate action to help protect our customers," he said in a verbatim repeat of Thursday's advisory. "This will either take the form of a security update through our monthly release process or providing an out-of-cycle security update, depending on customer needs."
So, what should users expect, say, over the weekend and early next week?
"It's hard to say at the moment, since this is just the beginning," said Alain Sergile, a technical product manager at Internet Security Systems' X-Force research. "But if SANS' report is accurate, I think we'll see additional targeted attacks where spam is sent to users at a specific organization in the hope that someone clicks on the link and downloads the malicious code so the attacker can infiltrate the network."
Because it remains an unpatched vulnerability, "everyone should consider this a zero-day kind of threat," added Sergile. "That means people will be caught flat footed."
Microsoft has recommended that users disable Active Scripting in IE until a patch is posted, but Sergile said that wasn't really a workable solution. "That will kill the capability of a large number of Web sites. The Web isn't much fun without those [scripting] capabilities." Instead, he recommended users visit only sites they know are safe.
Or turn to another browser. "The problem is in how Internet Explorer interprets the scripting call. Firefox doesn't have this problem."
March 18, 2006
New round of testing underway...
There haven't been many updates in awhile because the AdwareReport team has been working on a new round of testing.
One of the problems we've run against in the past is that we've been somewhat limited in the number of spyware programs we've been able to test against. After hitting a certain number of infections, our testing PCs crawl, sometimes taking as long as 5 minutes to even open up an Internet Explorer window.
For the upcoming April reviews, we've spent quite a bit of time building a new testing center with upgraded hardware. This hardware has allowed us to more than double the number of spyware infections we test against, resulting in more accurate test scores.
Expect updated reviews shortly for PC Tools Spyware Doctor, Aluria Antispyware, Microsoft Defender, Ewido, StopZilla, and perhaps a few new additions (if we can find the time - it takes the better part of a day to fully test a single product).
February 15, 2006
An email address connected to SpyAxe, SpywareStrike, SpyFalcon
A person at this email address () contacted one of our readers in regards to a payment for SpyFalcon, the latest variant of the illegal scamware program, SpyAxe.
If you know any other information about this address or the person behind it, .
February 11, 2006
Microsoft vs Lavasoft - one reader chimes in
The email below was received from one of our readers who was commenting on our article, "The Absolutely, Positively Best Way To Get Rid of Spyware".
What do you think? Should we all just give up on the internet? Chime in! Comments will be open for seven days. Spammers beware - comments are moderated and you will be added to a global blogging blacklist.
An evaluator at this site gives Microsoft Anti-Spyware high marks for its effectiveness as a spy fighter. I took his advice and tried it myself and found that it is pretty good at identifying CWS junk and even removes it--or so I am informed--but it does not keep the same parasites or others from coming right back moments later. I've also got LavaSoft Ad-Aware and get similar results, but without the complications I experience with Microsoft's product. I read a story on this site from a disabled vet who complained about Wal-Mart and how confusing and terrible LavaSoft's product is, but Microsoft's Anti-Spyware is enough to drive a person nuts by the endless stream of on-the-spot, impossible decisions it insists be made. During the 24 hours or so that I've had Microsoft's Anti-Spyware trial software, I have already been advised dozens of times, for example, that "A program is attempting to change file number 32axedratbcd42qx4.1 from 'this to that.' If you recognize the file in question you might want to decide what to do based on that. Now, what do you want to do, Allow it or Block it?" How on Earth is the typical person supposed to make an intelligent choice in such an instant? The evaluator also spoke of "good guys" and "bad guys" cooperating with and scratching each other's backs to enhance profits. I think it's an absolute waste of time to categorize the two groups because it doesn't do a thing to distinguish them one from another. Maybe the ultimate solution to this entire sleazy Internet industry is to just stay away from it altogether and let all the clever and "highly ethical" computer experts who prey on the public cut one another's throats in private while Internet commerce crumbles down around them.
New Trojan Horse Redirects You To Anti-Spyware Review Sites
Latest scumware program tricks computer users into visiting bogus anti-spyware review sites.
A potentially new variant of SpyAxe opens annoying popup alerts on your computer, but instead of redirecting you to a fake anti-spyware website, it redirects you to two new fake anti-spyware review sites. These URLS appear to have different owners, but the affiliate linking scheme and product recommendations are identical.
It should go without saying that any site which offers recommendations on PC security products should not stoop to installing spyware on people's computers. The people responsible for this new malware should be arrested.
These are the URLs which appear as a result of this trojan:
http://www.onlinesecurityguide.net/?adv=XXX [Affiliate ID removed]
http://www.topadwarereviews.com/?adv=XXX [Affiliate ID removed]
February 09, 2006
"Spyfalcon" is the latest SpywareStrike/SpyAxe variant
At least two new variants of SpywareStrike (SpyAxe) have been discovered, both making use of the same annoying popup alerts seen in previous versions.
In the first variant, when the user clicks on the alert they are redirected to one of two fake anti-spyware review sites. These sites predictably recommend SpywareStrike as the top choice.
The second program works in an almost identical fashion to SpywareStrike and SpyAxe, but redirects the user to a new website at www.SpyFalcon.com. Purchasing the software from this site will install various helper malware programs that the creators can use to continue infecting your computer in the future. Your credit card data will also be stolen as well.
Related Articles:
SpywareStrike
Third Variant of Spyware Strike Reported
New Version of Spyware Strike
A Letter from SpyAxe
SpyAxe
February 02, 2006
Kama Sutra Virus/Worm Will Begin Attacking Computers This Friday
AntiSpyware, Backup, and AntiVirus Software will Help
The Kama Sutra Virus, which had previously affected over 500,000 computers worldwide, is going to be activated on Friday. It has been spreading around the world via email, but wont begin destroying computer files until Friday, February 3rd.
This virus makes use of special social engineering techniques to spread itself, including sending itself to all of the contacts contained in the user's address book.
On the third day of the month, it will permanently corrupt a number of common document format files, including Microsoft Word, PDF, Excel, digital photos, and others.
Here is a short list of attachments you want to watch for: my photos, schoolgirl fantasies gone bad, the best video clip ever, a great video, give me a kiss,*Hot movie*, Fwd: Photo, Fw: Sexy, Fw: Pictures, Miss. Lebanon or please see the file. Never open attachments, unless you are expecting a certain file.
What To Do
Adware Report readers are advised to back up all important files, possibly even their entire hard drive. Next, make sure that you are running one or two antispyware programs with memory-resident shields by midnight tonight. Finally, activate your memory resident antivirus program.
January 30, 2006
Third variant of SpywareStrike Reported...
Two readers have written in to report a possible new variant of Spyware Strike that can not be removed by either PC Tools Spyware Doctor or Aluria Spyware Eliminator. This information should be confirmed by in the next 48 hours, so hold tight if these programs don't work for you.
Update (10pm): Make that two dozen people. There is definitely a new wave of Spyware Strike infections going around. Products we know that definitely DON'T work at this point at Aluria Antispyware, AdAware, Spyware Doctor, Spybot, and MS AntiSpyware. These programs will disable most components, but the annoying alert window and system tray icon remains.
Some symptoms others have reported:
* GBDialer installed (900# dialer)
* Trojan.small installed
* Internet Explorer .WMF exploit attempted
Update (10:20pm): A few readers have managed to disable the latest version. Their methods have been added to the main Spyware Strike page.
SpywareStrike
Thought you were safe because you've innoculated your computer against SpyAxe? Think again. A new program called SpywareStrike has been created with a similar nefarious purpose: to invade your PC and pester you into paying a $49.99 "removal fee".
Want even more bad news? If you were infected with SpyAxe and manually removed it, you now probably have SpywareStrike installed on your computer.
Just like SpyAxe, this program will invade your computer through the zlob trojan (and possibly others), popping up frequent alerts to "upgrade". If you take the bait, you'll pay $49.99 for a program that does nothing to protect you against spyware, and even opens up additional security holes on your PC.
SpywareStrike is located at the URL of the same name. The website was created on December 20th, 2005 and the marketing is identical to that of SpyAxe, down to the logo. SpywareStrike can be installed via trojan horse, direct download from the site, or is left behind after manually disabling SpyAxe. It has a different signature than SpyAxe, so SpyAxe removal tools are ineffective against it.
SpyAxe and SpywareStrike are just two of over 100 reported malware programs based on the latest Microsoft security flaw.
If you have any information about the makers of SpyAxe or SpywareStrike, please contact us. Click here to read what we've discovered so far.
Update: Jan 23, 2006
A new version of SpywareStrike has been identified. This version is more difficult to manually remove and is not currently being detected by any antispyware program. Aluria Antispyware has reported that they intend to push an update to remove this version by January 30th, 2006. We have not yet received word from other antispyware vendors about this threat.
Update: Jan 30th, 2006
The makers of this scourgeware are still at it. It appears that a third variant of Spyware Strike is now on the loose, more sophisticated than the previous versions. This version will create hidden WAN network connections (for tunnelling through firewalls, presumably), install a 900# dialer (beware if you have a modem), install a trojan horse, and includes very sophisticated routines that will completely regenerate the software should an incomplete manual removal be attempted.
Automated SpywareStrike Removal
Aluria Antispyware and Spyware Doctor are the only products that we know of which can automatically disable and remove the first two versions of SpywareStrike. Ewido and Microsoft Antispyware appear to remove parts of it, but many readers are reporting that the alert popups remain with these tools. No tool is yet available that will remove the latest version (Jan 30, 2006)
Manual SpywareStrike Removal Instructions
WARNING: The following fixes were recommended by readers and I have not tested them. This information is provided on an "as-is" basis only, and I make no guarantees. Anytime you manually alter system settings, you run the risk of damaging your operating system and rendering your computer inoperable.
Please note that SpywareStrike is closely related to SpyAxe, and when SpyAxe is manually deleted a new trojan is installed. It is quite possible that SpywareStrike does the same, so following this procedure may expose you to other malware.
Method #1
This was the first removal method we discovered, but it will probably not work with the latest version of Spyware Strike. Even with the first version, some readers report that the flashing red alerts remain running with this technique.
1. Search and delete all references to "SpywareStrike" in registry. Note that youll find a reference to a file called "C:\Documents and Settings\\Local Settings\Temp\~nsf.temp\Au__.exe" or something similar.
2. Delete the file referenced above
3. Go to c:\program files\spyware strike and run the uninstall utility
4. go to task manager and kill the process spywarestrike.exe
5. Delete c:\program files\spyware strike
6. edit c:\windows\system32\drivers\etc\hosts to add the line "127.0.0.1 spywarestrike.com" (this will prevent the piece that I could not get rid of from automatically downloading the software again and again)
Thanks to Jason Burroughs for this fix.
Method #2
A simpler solution, but more likely to leave behind hidden trojans, etc. This method is highly unlikely to work with the latest versions.
1. Boot computer into safe mode.
2. Uninstall SpywareStrike using the SpywareStrike uninstall utility.
3. Delete the file netwrap.dll from the \windows\system32 directory.
Method #3
If SpywareStrike reappears after trying the previous methods...
1. Boot computer into safe mode.
2. Delete the file mssearchnet.exe from the \windows\system32 directory.
Method #4
Another method that has worked for some readers but not others is to use a combination of tools:
1. Download SmitRem at www.downloads.subratam.org/smitRem.exe
2. Reboot into safe mode and run SmitRem. Check "Delete at Reboot".
3. Immediately run a full scan with your favorite spyware remover to remove incidental trojans and dialers that may have been installed.
Method #5: New Versions of Spyware Strike (updated Jan 30, 2006)
Two new versions of Spyware Strike are on the loose, and the above instructions aren't working for a lot of people. There are some other things to try, but I should warn you that these instructions are *not* for the faint-of-heart. If you don't know what you are doing, then you should definitely just wait for the next update of Aluria Antispyware or Spy Doctor, as both tools seem to be doing a decent job of keeping up with the new releases.
As you can probably tell from the instructions below, the latest version is infinitely more sophisticated than the prior ones. Spyware Strike may be the CoolWebSearch of 2006.
1. Look for new WAN network adapters named IIRC. These were installed by SpywareStrike and are probably how it manages to tunnel through any firewall software.
2. Backup and then remove the following files in the infected user's documents and settings folder:
\UserData\8R4F2NQZ with file oWindowsUpdate[1].xml
\UserData\AH0N2NIN with file oWindowsUpdate[1].xml
\UserData\O1UTE7EV no files
\UserData\OBY9QTQ1 no files
3. Delete registry entry: HKEY_USERS\S-1-5-21-175XXXXXXX-XXXXXX_Classes\Software\Windows\CurrentVersio
n\Deployment\SideBySide\2.0 (and sub-entries)
4. Rename the normal user account, reboot, and then rename it back to the original name.
This has been reported to successfully disable those stubborn alert windows.
January 27, 2006
Spyware suspect arrested in Japan
A Japanese man has been arrested for allegedly creating and distributing malicious code which was designed to steal internet banking passwords.
An investigation into the theft of 216,000 (1,000) from the bank account of a jewellery shop in Kawasaki, Japan, found that spyware had been installed on one of the company's computers and passwords liberated by stealth.
Atsushi Takekawa, 31, has been arrested in relation to the theft and police are also investigating a second man, 41-year-old Kiichi Hirayama.
It is alleged the two men conspired to infect the company by attaching the spyware to an email sent to the company, purporting to be from a dissatisfied customer.
Graham Cluley, senior technology consultant for Sophos, said Takekawa's arrest is encouraging, especially at a time when such malicious code is on the increase.
However, he cautioned that the arrest is "only the tip of the iceberg".
January 26, 2006
Aluria Antispyare First Program to Remove New SpywareStrike variants
Those of you who have written us letting us know that Aluria, PC Tools, and Webroot's products are not removing Spyware Strike will be relieved to learn that Aluria Software's newest update includes signatures for SpywareStrike's latest variants.
If you have a stubborn install of SpywareStrike and find other tools that succeed in removing it, please .
January 25, 2006
Attorney general sues under anti-spyware law
New York company is accused of deception
By TODD BISHOP AND JOHN COOK
SEATTLE POST-INTELLIGENCER REPORTERS
AdwareReport Editor's Note: Spyware Cleaner is the 2nd anti-spyware product that we've reviewed to get hit with a lawsuit alleging deceptive practices. Read our review of Spyware Cleaner here.
Washington's attorney general has filed his first lawsuit under the state's new anti-spyware law -- alleging that a New York company's software claiming to rid personal computers of spyware actually deposits a nefarious program instead.
The suit, which was filed Tuesday against Secure Computer LLC of White Plains, N.Y., alleges that the company's spyware-scanning software falsely labels ordinary Windows system keys as spyware to induce computer users to pay $49.95 for the company's Spyware Cleaner program. That program doesn't actually clean spyware from the PC but rather modifies the computer's security settings, the suit alleges.
Attorney General Rob McKenna is expected to announce the suit at a news conference today in Seattle along with Nancy Anderson, deputy general counsel from Microsoft Corp., which also has filed suit against Secure Computer.
"This lawsuit is intended to send a message to spyware perpetrators and to hucksters who market phony products that play on the public fear of spyware," McKenna said Tuesday night. He called the alleged tactics, especially the changing of security settings, "quite startling."
Microsoft's lawsuit was prompted in part by complaints from the company's customers, Anderson said. At the same time, online promotions for the Spyware Cleaner program allegedly capitalized on the company's name, with phrases such as "Microsoft spyware cleaner" and "Microsoft anti-spyware."
Anderson described the case as an "important milestone in making sure consumers understand that they will be protected if they are preyed upon by deceptive practices." Microsoft previously cited the state's anti-spyware law in a separate lawsuit against an unnamed defendant.
The law, which was enacted last year, made it illegal to illicitly install software on someone else's computer to modify settings, collect information or perform other deceptive acts.
Both suits also make claims under anti-spam laws, alleging deceptive practices in e-mails used to promote the product. McKenna's suit names defendants including Paul E. Burke, Secure Computer's president, who didn't return a message left on his phone in New York.
The suit alleges that Secure Computer, Burke and another defendant, Gary T. Preston of Jamaica, N.Y., made more than $100,000 by selling Spyware Cleaner through a network of affiliates. The suit, which also names some of those affiliates, asks the court to enjoin the defendants from deceptive practices and assess financial penalties.
Ben Edelman, an expert who has testified in anti-spyware suits, said he was familiar with Secure Computer and its tactics. He described it as "a deplorable practice" that "takes advantage of users in their moment of weakness." Edelman said there are other companies engaged in similar practices.
According to the attorney general's suit, the defendants marketed the Spyware Cleaner product to computer users through pop-up advertisements and e-mails that told them their machines had been infected with spyware. The pop-up messages, which mimicked the appearance of Microsoft security boxes and used the Redmond company's trademarked font, then asked users to perform a computer scan.
The messages were designed to alarm computer users, with one reading: "Warning -- Your computer may be infected with harmful spyware programs," the suit says. Those consumers who followed through with the scan were then told that they had spyware on their computers.
"Deceived into believing that dangerous spyware is on their computer and there is no time to waste, the user is induced to purchase Spyware Cleaner," the suit says.
January 24, 2006
Aluria Software to Speak at First-Ever Anti-Spyware Coalition Public Workshop
Workshop Will Address the Impact of Spyware on Consumers and the Enterprise
WASHINGTON --(Business Wire)-- Jan. 24, 2006 -- Aluria Software, an EarthLink company and a leading provider of anti-spyware and desktop internet protection solutions, today announced that Matt Cobb, EarthLink vice president and general manager of Aluria Software, will be a featured panelist at the first-ever Anti-Spyware Coalition (ASC) Public Workshop. The workshop, scheduled for February 9 at the Capitol Hyatt Regency in Washington, D.C., will examine the growing threat of spyware and new technologies and solutions geared toward stopping its spread.
Cobb joins other well-known speakers from the public and private sector such as Walter Mossberg, personal technology columnist for the Wall Street Journal, and Susannah Fox, associate director at the Pew Internet & American Life Project. Federal Trade Commission Chairwoman Deborah Platt Majoras will deliver the event's keynote address.
"Spyware threats have become more insidious than ever before and continue to flourish as spyware purveyors develop increasingly sophisticated methods to infect PCs and avoid detection," Cobb said. "The work of the Anti-Spyware Coalition is a critical front in the war on spyware. Informing consumers of the threats they face and arming them with the best tools possible remains the best way to fight the tactics of these cyber criminals. Aluria Software's partnership with the Anti-Spyware Coalition is a reflection of our commitment to deliver unparalleled, proactive protection for our customers."
The day-long event will include interactive discussions on the definition of spyware, legislative efforts to curb spyware proliferation, appropriate corporate security safeguards and suggested industry guidelines. Cobb will participate on a panel at 10:55 a.m. discussing how computer users can avoid, block and remove spyware.
Aluria Software offers unmatched protection for millions of consumers and businesses worldwide from spyware, virus, phishing and other insidious security threats. Aluria Software's proprietary Active Defense Shield works in concert with a desktop's operating system driver to instantly identify and repel spyware before it can be installed. The company's products are the first in the industry to identify spyware at the system kernel level, providing an unprecedented, proactive defense.
Aluria Software and parent company EarthLink are founding members of the Anti-Spyware Coalition and longtime corporate supporters of consumer protection organizations including the Center for Democracy & Technology.
About the Anti-Spyware Coalition
The ASC is a group dedicated to building a consensus about definitions and best practices in the debate surrounding spyware and other potentially unwanted technologies. Composed of anti-spyware software companies, academics and consumer groups, the ASC seeks to bring together a diverse array of perspective on the problem of controlling spyware and other potentially unwanted technologies.
About Aluria Software
Aluria Software, an EarthLink (NASDAQ: ELNK) company, offers comprehensive software security solutions utilized by millions of subscribers worldwide to protect their computers from spyware, virus, and other security threats. The Aluria Security Center protects consumer PC's against a deluge of online attacks by applications like spyware, spam, phishing, pharming, and a variety of other network intrusions. Paladin, Aluria's small business product, monitors, detects, blocks and cleans small businesses networks of spyware. Aluria's anti-spyware software development kits (SDK) are used by third-party software and hardware providers to complement their current offerings with advanced spyware detection and removal capabilities. For more information, visit www.aluriasoftware.com or call 888-627-4650.
Razespyware
Razespyware (also known as AZESearch) is a rogue antispyware application that installs itself on your desktop and then displays popups telling the user that they have spyware installed. The bright red flashing popups also nag the user to purchase RazeSpyware for $49.95.
The program also installs a fake keylogger (keylogger32.exe), which is detected by the "free scan". It also transmits information from your computer back to pills-catalog.net.
Razespyware is distributed via security exploits. To prevent infection, be sure to download the latest Windows security patches at windowsupdate.microsoft.com.
Automated Razespyware Removal
Aluria Antispyware, Spyware Doctor, and Spy Sweeper are all reported to remove this malware.
Another reader has reported a partial fix that is affected by installing fresh copies and running a full scan of AdAware, Spybot S&D, and Microsoft Antispyware (important: do not reboot when prompted). However, this method disables Alexa, Google, and other browser toolbars.
RazeSpyware Manual Removal
1. Search for the file warnhp.html on your hard drive and delete it.
2. Search the registry for razespyware.exe. Delete these entries.
Note: This method will disable the software, but the red alert will remain on the screen. For this reason, automated removal is strongly recommeded.
Similar Malware: SpyAxe, SpywareStrike, SpySheriff.
A New Way of Monitoring Malware
Editor's Note: The following commentary was found on TechDirt. We would like to add that we know of two more proactive approaches to detecting spyware that are currently being developed in the lab, but because we are under nondisclosure agreements, we can't write about them on the site. Suffice it to say, there are some very promising technologies on the horizon.
For years we've been discussing how traditional methods used by antivirus and antispyware products are often too reactive. The firms wait for someone to complain or send in an example of a problem. This often leads to calls for behavioral based solutions that look for certain behaviors that are likely to come from malicious files -- though that certainly risks lots of false positives if legitimate systems use similar behavior (already this can be seen with some firewall products, which constantly pop up warnings -- almost all of which users ignore, because so many are false positives). However, it appears that one firm is trying to take a different form of proactive approach. alarm:clock writes about SiteAdvisor that appears to try to proactively visit lots of sites and download all sorts of products while while putting together a large database of what those sites and products do, so that anyone can check to get a sense of how safe a site or software download really is. It's an interesting approach if they can really cover enough sites and downloads, while still getting people to actually look at their info (and, of course, not getting the data wrong).
Source: TechDirt
January 22, 2006
New version of Spyware Strike
The spyware research team at Aluria software has informed us that the Spyware Strike scamware is mutating. The latest version is not yet disabled by any known anti-spyware program. Aluria expects to push an update that will remove this version sometime this week.
January 20, 2006
Anti-Spyware Book List Launched!
Want to learn more about spyware? Check out our recommended anti-spyware book list that we launched today!
New version of Spyware Strike?
We just received word from one of our readers that a new version of Spyware Strike might be making the rounds. We're researching this right now to find out if it is true.
In the meantime, if you are currently using Aluria Spyware Eliminator or PC Tools Spyware Doctor and find that they are not removing Spyware Strike on your PC, please .
January 12, 2006
A Letter from SpyAxe
We received an email from one of our readers today who had finally received a response from SpyAxe support. At the end of this email is alleged contact information for their support department.
Given the bogus Spyaxe WHOIS information and the fact that an identical scam website was set up in late December by the same people, we aren't accepting their story. If you have thoughts on this, .
Please accept our sincere apologies about the fact that we did not answer you at once.The thing is - we received too many complaints on adware/popup/trojan activity on user's PC's related to our Anti-Spyware product - SpyAxe, and all this time the issue was under heavy investigation by our Staff and we could not answer each email because we waited for the results of investigation to make sure we discover the reason of this activity, find out who is the offender doing this and find out how to help You to fix it.
Finally, as a result of this investigation, with the help of our devoted users - we found out that one of our affiliates, under affid=10014-10018 was using the prohibited and illegal ways of advertising of our product - SpyAxe. These advertising methods are completely prohibited by our TOS, and affiliate's actions are a rude violation of our Terms of Service and Privacy Policy. Thus, by now his account is already terminated and according legal actions have been taken towards this person.
As a result of this investigation and great efforts of SpyAxe technicians we came out with this cure for the adware you have on your PC, which constantly generates continuous warning popup in your tray stating that your PC is infected.
The cure is an Uninstallation file which should delete popping-up SpyAxe-related advertisement on your PC.
Below you can find quick instructions on how to use attached uninstallation file:
=======================================
1) Save uninstallers.zip from http://www.spyaxe.net/uninstall/cmer_uninstallers.zip to your desktop or HDD.
2) Extract files "illegal_adv_uninstaller1.exe" and "illegal_adv_uninstaller2.exe" to your desktop or your HDD using WinZip (http://www.winzip.com).
3) Execute "illegal_adv_uninstaller1.exe" and "illegal_adv_uninstaller2.exe" files one by one by double-clicking with your left mouse-button. Don't wait for anything to happen. It worked.
4) Reboot your PC after you double clicked on the "illegal_adv_uninstaller1.exe" and "illegal_adv_uninstaller2.exe" files.
5) Your PC is now clean from the infection.=======================================
Again, please accept our deepest apologies from all the SpyAxe staff. We are doing our best to help you in this issue.
Please let me know if you have any other questions or issues related to SpyAxe product.
Thank you for your understanding and support.
------------------------------------
Kind Regards,
Joshua Veronimo
Support Department
SpyAxe Staff
Phone: 206-339-5073
FAX: 206-339-5073
January 11, 2006
Spy Sheriff
Spy Sheriff is a system hijacker that causes popups to appear on your computer telling you that you have spyware installed (which you do!). Clicking on the alert brings you to a website which attempts to sell you a bogus spyware program called "Spy Sheriff".
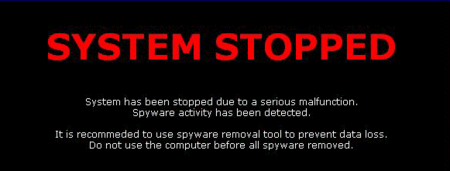
Automatted Spy Sheriff Removal Instructions
Spyware Eliminator, Spy Sweeper, and Spyware Doctor are all reported to remove this threat.
Manual Spy Sheriff Removal Instructions
Note: The following procedure is courtesy of BleepingComputer.com.
In order to remove this infection we will need to use HijackThis to manually remove the infection:1. Print out these instructions as we will need to shutdown every window that is open later in the fix.
2.Download and install CleanUp! but do not run it yet.
*NOTE* Cleanup deletes EVERYTHING out of temp/temporary folders and does not make backups.
3. Download, install, and update Ewido Security Suite
1. Install Ewido security suite
2. Launch Ewido, there should be a big E icon on your desktop, double-click it.
3. The program will prompt you to update click the OK button
4. The program will now go to the main screen
5. On the left hand side of the main screen click on Update
6. Click on Start. The update will start and a progress bar will show the updates being installed.
4. After the updates are installed, exit Ewido
5. Reboot into Safe Mode. You can do this by restarting your computer and continually tapping the F8 key until a menu appears. Use your up arrow key to highlight Safe Mode, then hit enter.
6. Once in Safe Mode, Open Cleanup! by double-clicking the icon on your desktop (or from the Start > All Programs menu). Set the program up as follows:
1. Click Options...
2. Move the arrow down to Custom CleanUp!
3. Put a check next to the following:
Empty Recycle Bins
Delete Cookies
Delete Prefetch files
Scan local drives for temporary files
Cleanup! All Users
4. Click the OK button
5. Press the CleanUp! button to start the program.
7. After Cleanup! is finished start Ewido Security Suite
1. Click on scanner
2. Make sure the following boxes are checked before scanning:
Binder
Crypter
Archives
3. Click on Start Scan
4. Let the program scan the machine
5. While the scan is in progress you will be prompted to clean the first infected file it finds. Choose clean, then put a check next to Perform action on all infections in the left corner of the box so you don't have to sit and watch Ewido the whole time. Click OK.
8. When the scan is complete, exit the program and reboot back to normal mode.
9. Click on Start, then Control Panel, and double-click on the Add/Remove Programs icon.
10. Uninstall the SpySheriff program and then exit Add/Remove Programs.
11. Delete the following, in bold, if found:C:\Documents and Settings\user account\Start Menu\Programs\SpySheriff C:\Documents and Settings\user account\Application Data\Install.dat
C:\Program Files\SpySheriff C:\Windows\Desktop.html
C:\winstall.exe
C:\Program Files\Daily Weather Forecast\*NOTE* user account is not the actual name of that folder. The name of that folder will be the name of your computer profile.
12. Download HijackThis and save it to your C:\ folder. Extract the hijackthis.zip file to c:\hijackthis. We will use this program later.
13. Make sure you are disconnected from the Internet and that all programs and windows are closed. Run HijackThis and press the Scan button. Place a check next to the following items, if found, and click FIX CHECKED:
O4 - HKCU\..\Run: [SpySheriff] C:\Program Files\SpySheriff\SpySheriff.exe
O4 - HKCU\..\Run: [Windows installer] C:\winstall.exe
O4 - HKLM\..\Run: [Daily Weather Forecast] C:\Program Files\Daily Weather Forecast\weather.exe
14. Close HiJackThis.
15. RIGHT-CLICK HERE and go to Save As (in IE it's Save Target As) in order to download the smitfraud reg to your desktop.
16. Double-click smitfraud.reg on your desktop. When asked if you want to merge with the registry click YES.
17. After the merged successfully prompt, using Windows Explorer, navigate to the following folder:
C:\Windows\Prefetch
18. If there are any files inside the Prefetch folder, delete ALL of them. (Do NOT delete the folder. Just delete the files inside.)
19. Reboot your computer.
20. You should be able to change your desktop back to normal now.Your computer should now be free of the SpySheriff infection.
January 08, 2006
New Version of SpywareStrike
A new version of SpywareStrike is apparently making the rounds now, just days after its initial release. If you've tried the SpywareStrike removal instructions only to have SpywareStrike return a few minutes later, then boot into Safe mode and delete the file, \windows\system32\mssearchnet.exe.
January 07, 2006
New Fake Anti-Spyware State Tries To Infect Your Computer and Take Your Money
Just discovered another hostile/scam website at securitycaution.com (WARNING: DON'T CLICK UNLESS YOU ARE PROTECTED AGAINST SPYWARE).
This website claims you are infected with the worm W32.Sinnaka.A@mm and points you in the direction of a couple of anti-spyware removal tools. We haven't tested these, but they are likely scams.
This website is allegedly infecting visitors' computers using the Microsoft WMF exploit.
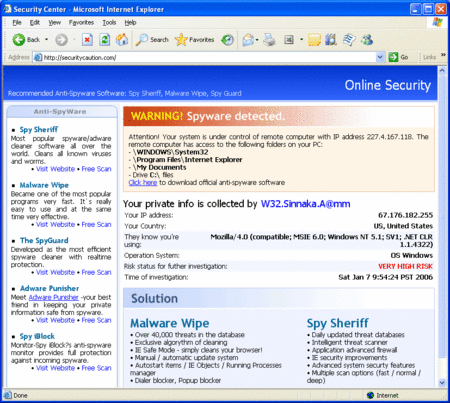
This screenshot is safe to click
SpywareStrike Removal Instructions
Untested manual removal instructions have been sent in by our readers and can be found at the end of the main SpywareStrike article.
January 04, 2006
99% of PCs worldwide are vulnerable to latest Windows flaw
Latest outbreak may be worst in computing history. Official Microsoft fix not available for at least a week
The latest Windows security hole has left most of the world's computers vulnerable to attack. Unlike most previous security flaws, this one is being actively exploited by Spyaxe and over 100 other malware programs.
The latest flaw in the Windows Meta File (WMF) means ordinary computer users can be infected with virus and spyware programs simply by viewing an image on an infected webpage.
Internet users are advised to download the latest antivirus and anti-spyware updates immediately, as an official patch from Microsoft will not be available until at least January 10th.
Chief Research Officer at F-Secure, Mikko Hypponen states: "Right now, the situation is bad but it could be much worse. The potential for problems is bigger than we have ever seen. We estimate 99 per cent of computers worldwide are vulnerable to this attack."
January 03, 2006
Hackers uncover 'biggest Microsoft vulnerability'
By Rhys Blakely
Editor's Note: SpyAxe is one of the programs that is using this vulnerability. The article below mentions that there are at around 100 others making use of similar techniques. Stay protected!
Computer hackers are targeting a flaw in Microsofts Windows operating system that has placed hundreds of millions of PCs at risk of infection from dangerous "spyware" programs used by criminal gangs to steal peoples identities.
The flaw in the software, which is used by 90 per cent of the worlds computers, allows PCs to be infected by programs maliciously embedded into seemingly harmless image files. It was first discovered last week, but Microsoft is yet to release a protective "patch" to guard against the danger.
"The vulnerability probably affects more computers than any other security vulnerability, ever," Mikko Hypponen, chief research officer at F-Secure, said on the web-security companys weblog.
Most attacks require a victim to download an infected file. But the newly discovered flaw, which dates back at least a decade, makes it possible for a PC to be hit simply by a user browsing a web page or opening an e-mail that contains an infected image.
Mark Herbert, the founder of intY, an internet security company, said: This is one of the first examples of a new generation of threats on the internet. Now people can run into serious problems just looking at web pages something we havent seen before.
"This should be a serious wake-up call to the web community."
Patrick Runald, a senior anti-virus consultant with F-Secure, told Times Online: "Unlike other threats, which tend to target specific versions of software, this affects all versions of Windows from the past 10 years or so - that means hundreds of millions of machines. We are now seeing lots of activity among virus writers looking to exploit this flaw."
According to Mr Runald, hackers exploiting the vulnerability have so far focused on using it to install secret "spyware" and "back doors" on victims' PCs. That suggests that criminal gangs are mainly responsible rather than trouble-makers who prefer mass e-mail campaigns to spread viruses as far as possible.
The underlying "source code", which maps out how to exploit the weakness, has now been published on the net by hackers.
Microsoft has confirmed that the flaw has been actively exploited and said it was working "with our anti-virus partners and aiding law enforcement" to tackle the problem.
The incident is especially embarrassing since it also affects the test - or "beta" -version of Vista - the latest version of Windows that is due to be released later this year. Bill Gates, Microsoft's founder, has heavily promoted Vista's improved security.
Donal Casey, a consultant for Morse, the internet security company, said: "Vista had been marketed as the secure version of Windows, but obviously it is not. Microsoft is covered because the final version hasn't been released, which will allow them to do a bit more thinking."
In the absence of a patch, Microsoft has urged PC users to follow its standard advice and "exercise caution when they open e-mail and links in e-mail from untrusted sources."
It added: "While we have not encountered any situation in which simply opening an e-mail can result in attack, clicking on a link in an e-mail could result in navigation to a malicious site."
Microsoft's statement can be found here.
According to F-Secure, more than 100 different versions of the malicious programs called WMF or Windows metafile programs targeting the flaw have emerged so far. This week WMF exploits have been spread in e-mails wishing people "Happy New Year" and by messages purporting to be from American security agencies.
According to the F-Secure website, Internet Explorer users are at the greatest risk of automatic infection "while Firefox and Opera browser users are prompted with a question whether theyd like to open the WMF image or not. They get infected too if they answer Yes."
The Home Office has estimated that identity theft accounts for 1.3 billion in stolen goods, services and cash a year. Meanwhile fraudsters have turned to online crime to sidestep new measures on the high street, such as chip-and-pin card technology. According to police figures, computer crime alone cost British businesses 2.4 billion last year.
December 30, 2005
The Hunt for SpyAxe
I've been having discussions for the past few days with a number of readers about SpyAxe. A couple of good points have come up.
First, the delivery mechanism SpyAxe uses, trojan horses, is probably illegal in most countries.
Second, the only place we know of to report them to is the Federal Trade Commission.
Third, it is doubtful if they can do anything about it. Why? Well, judging from the poorly written English on the SpyAxe website, they are likely based in some country where they can't be touched by the law. Their website claims they are based out of New Zealand, while their WHOIS entry indicates a Seattle, Washington address.
So where do these guys operate from? Hard to say ... a search of the US patent and trademark databases turns up nothing. But their website is hosted by a company called "NetCat Hosting" (www.netcasthost.com). The homepage is written in Russian, and a reverse IP lookup puts it in the Ukraine. However, WHOIS indicates that NetCat Hosting is based out of Sydney, Australia. The domain was registered at EstHost, a service provider known for hosting many CoolWebSearch sites.
So, the makers of SpyAxe may be based out of one of the following locations:
1. Seattle, Washington
2. New Zealand
3. Russia
4. Sydney, Australia
A search for Mr. David Alant out of Seattle turns up nothing. This is to be expected, as the 187th ave street address in WHOIS is not actually in Seattle. However, reverse directory on his phone number (206-954-3154) turns up David Ackerson, just a few zip codes away. Now we're getting somewhere! Mr. Ackerson is a coach for the Seattle Youth Soccer Association, and is/was an executive from a company that does have some kind of technical focus. It appears he was a donor to Shoreline Public Schools foundation in Seattle. Some more searching indicates possible (not confirmed) connections with WRQ, an IT security company, or NextLink (CEO of the same name). It is very unlikely that David Ackerson is the person behind SpyAxe.
Have any other leads? Email them to us at .
Updates:
1. The domain NOSPYWARESOFT.COM resolves to spyaxe.com. It is registered to:
Keramitsu LLC
David Alan Taylor (tailor.david - AT - gmail - DOT - com)
321th Melburn Street
Seattle
Washington,98107
US
Tel. +207.9545521
Note the two spellings of the last name, and also note "Melburn street", which may perhaps be a reference to the Australian city.
Keramitsu, LLC does not appear to be an existing LLC, or at the very least, does not have a web presence. "Keramitsu" literally means "three bugs" in Japanese. We can speculate that this may refer to three security holes being exploited by the software (Thanks to Jim Canter for the translation).
The phone # is not in service.
2. David Taylor is the name of a senior information security specialist at the University of Pennsylvania. David was investigating a worm that had infected the University's computers. This worm would log into an IRC channel, where it could download spyware to infect the host computer. Mr. Taylor logged in and found Diabl0 aka Farid Essebar, the author of the worm. He proceeded to have a discussion in which Diabl0 indicated that the worm (Mytob) installed toolbars and lowered the security settings of Internet Explorer, thus allowing more ads to be delivered to end users. Diabl0 was anonymously collecting money on the other side for these advertisements.
This strikes up an interesting possibility - Diabl0 is at it again, this time with new trojans (Zlob and ZToolbar).
Other searches indicate that Diabl0 may be based out of Morocco. Further speculation (without any verifaible facts behind it, but interesting nonetheless) states that this scam may be funding Al Qaeda or other terrorist groups.
Diabl0 was arrested in February, so he's not behind it. However, he did sell the source code to others and new variants of Zotob have been discovered since his arrest. Most likely, the creators are associated with his hacking group, 0x90-Team.
3. Other domain names related to SpyAxe include: nospywaresoft.com, almanah.biz, spyaxe.net, and spyaxesupport.com.
SpyAxe
SpyAxe is a new malware program which started making the rounds in December, 2005. According to F-Secure, over 2,500 PCs per hour are being hijacked by this malware. SpyAxe is a reputed anti-spyware program that makes use of a known trojan horse to display annoying popup windows. These alerts warn the user that their computer is infected with spyware. If the user clicks on the popup, a browser window is opened and the program SpyAxe is downloaded from www.spyaxe.com.
Despite SpyAxe.com's slick marketing, please be warned that this is not a legitimate company. SpyAxe is not based out of New Zealand, and in fact the program was created by a group of hackers as a scam.
After SpyAxe is installed, it will conduct scans but will not disable any spyware until the program is purchased. SpyAxe can not be uninstalled from the Windows Add/Remove Programs list.
SpyAxe makes extensive use of false positives, even detecting a registry key that belongs to the operating system. It is installed by the trojan horse, Trojan-Downloader.Win32.Zlob. Other trojans that install this software include ZToolbar and Trojan.Puper.
Update (12/30/2005): I have been informed that SpyAxe is rapidly expanding the number of ways by which it is infecting PCs. As of right now, no tool is guaranteed to remove this product. However, I have had reports that Webroot and Spyware Doctor have been able to detect and remove certain variants of SpyAxe.
Read more about the hunt for the creators of SpyAxe here.

Read about the Hunt for SpyAxe
December 27, 2005
This week's reviews
New reviews going up this week, including the latest review of NoAdware 4.0, Spyware Begone, and Spyware Cleaner.
December 16, 2005
Beginner's Guide to Securing Your Computer
|
So you've probably heard about spyware and all the problems it can cause with your computer, but did you know that even with an anti-spyware tool installed, your computer is still exposed to hackers, trojans, and viruses that can steal your financial information, hijack your email, or even destroy your hard drive?
Anti-spyware tools protect you against only a few types of malicious software programs and privacy attacks. For complete security, you'll want a complete set of antivirus, firewall, and antispam programs. Learn more about these different types of internet security programs and how they protect you below. Antivirus The most obvious threat to your computer's health is a computer virus. Viruses are usually delivered through email attachments or corrupted downloads, such as are typically found on file sharing networks. Once on your PC, a virus can destroy your operating system, corrupt your hard drive, use your email client to send spam, delete your personal files, or in rare cases, even physically destroy your hard drive. Once a virus runs on your computer, it can quickly spread to infect others. Antivirus software is designed to protect you against the harmful effects of viruses. This software runs in the background and continually checks for virus activity. It will also scan your hard drive on a regular basis to detect and repair infected files. Antispam Anyone with an email address today has probably received spam emails, and lots of it. For the most part, spam emails are annoying and a waste of time, but they can sometimes be a threat to your computer. If you happen to open an email with an infected attachment, you can inadvertently install a virus on your computer. While a good antivirus program will protect you against this possibility, it won't necessarily protect you against attachments that install trojan horses or activity monitoring software on your computer. These types of invaders allow outsiders to copy data, activate webcams and microphones, capture keystrokes, log IM and browsing sessions, and access personal files. While a random hacker would have little use for much of this data (other than perhaps credit card information), there are commercial programs available that jealous spouses or paranoid employers can use to monitor your activities. For the most part, antivirus programs do little to protect you against these programs. Anti-spam software can stop an email attack, but unfortunately, they can be installed in a variety of other ways. This is where firewall software comes in. (Note: we've performed some testing of anti-spam software which you can access via the menus on the left.) Firewalls Ultimately, for an invader to gain access to your PC they must be able to communicate with it. Firewall software closes the doors by which outside invaders may enter your PC, keeping you a bit safer. Of course, not all malicious software is installed anonymously. It can also be installed unknowingly through bundled software or knowingly through activity monitoring software. This is why good firewall software also polices outgoing activity and stops unknown software from communicating with the outside world. While this will most likely cripple an invading software program, there are no guarantees. Spyware makers are getting smarter all the time, and some spyware programs can contact the outside world by hijacking the communication channels of known programs such as browsers. In any case, a firewall program won't stop a spyware program from running and slowing down your computer. So here's where the final piece of the puzzle comes in: Antispyware. For more information on firewalls, read our article "Firewalls: What They Are and Why You Need One" or navigate here for firewall product reviews. Antispyware Antispyware products help to secure your computer and make it run faster by finding and disabling malicious spyware programs and trojan horses. Once these programs are removed, they no longer consume system resources. A lighter load on your computer means all your other programs will run faster. It's important to know that antispyware programs won't protect you against viruses, guard your email, or prevent unauthorized access to your PC. This is why you need all four programs for a complete solution. For more information on antispyware programs, check out the articles on the left or click here for spyware product reviews. |
December 10, 2005
Something Far More Important Than Spyware...

About a month ago, a little boy named Brendan went in for outpatient surgery. The procedure resulted in grave complications and on Tuesday, his mother was told that he has perhaps two weeks to get a heart transplant. The average wait time is 30 days.
A new website has been put on the net at http://www.SaveBrendan.com. At the website you can read his story, see photos, and learn different ways you can help. And if you would like to help, even two minutes of your time will make a big difference. A rally is planned for Tuesday at the John Hancock building in Chicago and we have to generate as much exposure as possible in the next 24 hours. The event will be televised, and local politicians and celebrities will be volunteering. At the end of the day, those who present a completed organ donation card will receive a dozen of the 6,703 roses on display (one for every person who died last year waiting for a transplant).
Could you email or tell others about the website and ask them to do the same?
Not only will this publicity campaign potentially help Brendan, it will help many others. Those who make the decision for themselves spare their families the responsibility of having to decide for them, especially in a situation where shock and grief makes decisions difficult to make. Because of this, past campaigns like this one have resulted in many additional organ donations, saving countless lives.
Thank you for your support. We will be back to covering spyware soon.

November 26, 2005
New product review - Secure Computer Spyware Cleaner
We've just uploaded our review of "Spyware Cleaner" by Secure Computer, LLC. This one looks like a scam...
November 21, 2005
The Absolutely, Positively Best Way To Get Rid of Spyware
An Entertaining and Insightful Peek Into The Anti-Spyware Industry
So youve found this site (and most likely a few others) and after all the reading, you may still be left wondering what is the best anti-spyware program? What exactly should I be running on my computer to get it (and keep it) running like new?
After over 18 months of continuous testing of different anti-spyware programs, I feel compelled to deliver some bad news: There is no such thing as a perfect spyware remover. There is no magic bullet.
With that out of the way, heres the good news: You can get your computer running well again with just a modest amount of effort. Im going to show you how while I spare you of product pitches and other marketing BS. And maybe youll be modestly entertained along the way. Lets get started.
The Reality of the Anti-Spyware Industry
Before you make any decisions and buy any software, there are a couple of things you need to know.
First, there are different camps in the anti-spyware business. First, there are the people who write spyware programs (the bad guys). Then, of course, there are the people who write anti-spyware programs (the good guys).
Second, the good guys arent always so good. In the beginning of the spyware wars, there was just AdAware and Spybot, the two best programs at the time. Both of them were volunteer efforts led by people who took offense at the invasive software that spied on peoples surfing habits and slowed their computers down. But they were soon joined by other companies who saw the profit potential in this market. Some of these companies (like Webroot, Aluria, and PC Tools) produced great products and invested their profits in R&D. Other companies (who will remain unnamed) sold software that ran the range from doesnt work to actively lies about what you have installed so youll buy it. Sadly, there are dozens and dozens of these companies still operating (despite the FTC shutting some of them down). And some of them have really, really great marketing.
Third, the bad guys are getting smart. Really smart. Spyware is their livelihood, and they have every intent of making every dime they can from this business. They pay programmers to write sneakier software. They hire the best marketers to put a new face on their companies. And they hire the best lawyers to shut people (like me) who name names.
(Speaking of, Ive been on the receiving end of legal action more from the good guys than the bad guys. Ive learned that everyone will use every means at their disposal to prevent the truth from getting out, if it isnt in their best interest.)
Finally, and heres where it gets really tricky, you need to know that there is a lot of behind-closed-doors discussions between the good guys and the bad guys. Sometimes they actively work together. Sometimes they just conveniently look the other way. But believe me, the bottom line is that both camps have a lot to gain and a lot to lose.
What Does This Mean?
It means three things:
1. You may pay good money for a slick looking product that does nothing.
2. You have to be careful who you give your money to. You might not get it back.
3. You cant rely on a single program to protect your computer.
The first two should be obvious by now. But the third is worth some more discussion.
Why You Cant Rely on a Single Spyware Remover
Ive run hundreds of tests and one thing Ive learned: no program removes 100% of spyware.
A simple solution would be to run multiple anti-spyware programs. But realistically, you cant run too many. First, you may end up paying for those programs, which is kind of a waste. Second, the cure might leave you worse off than the illness.
Why? Well, one reason why spyware is so bad is because it slows down your PC. All of those programs each consume a little bit of memory, a little bit of CPU, a little bit of bandwidth. Running spyware programs does exactly the same thing. The difference is that an anti-spyware program will consume far more CPU, bandwidth, and memory than just about any spyware invader. The technical term for this is resource contention. You can actually slow your computer down to a crawl by running just a few spyware removers at once.
Ive found the magic number is two. Two good programs are all you need. I recommend you pick one commercial product, and one free product.
Why Choose a Commercial Product?
For-profit companies generally do a much better job of writing spyware removal programs. There are many reasons (chief among them being that for-profit companies can afford to hire armies of spyware researchers) but some people will argue with me until theyre blue in the face, so I will just leave it as an empirical statement: after running hundreds of tests, commercial products do a lot better than free ones.
Another indisputable point in favor of commercial companies however, is that they can provide you with real customer support. Not just a forum manned with rude (and sometimes clueless) developers. A real phone # with a real person on the other end. Some of us really like having that option available.
The Down Side of Commercial Products
For-profit companies are legally obligated to maximize shareholder return (ie: make money). This can lead to some interesting conflicts of interest. I have first-hand knowledge that back room agreements take place all the time between the spyware makers and the spyware removers. The problem is that these agreements are difficult to prove and not usually discussed. For example, if a software program youre running suddenly stops detecting a certain spyware program, will you really notice? Probably not. And it could end up putting thousands of dollars a month in the pockets of the vendor. Ethics aside, it does happen and its probably happening at ___(insert favorite anti-spyware company name here) ___.
Why Choose a Non-Commercial Product
For the very opposite reason, you might find yourself in the freeware camp. Now I know you arent one of those who naively claim that corporate software companies are all evil and that the free software products are hands-down better than commercial versions. But those people are all over the net, and from the hours they must spend posting, you might think that there are more of them than there really are. But in reality, theres a few bad apples out there in the freeware camp, just like there are in the commercial camp.
So heres the real deal: Non-commercial companies are generally free from the commercial ties to spyware companies.
"Generally" is the operative word here. Case in point, earlier this year (2005) it was announced that Aluria (an anti-spyware company) and WhenU (a spyware company) had forged a partnership and that Aluria would no longer remove WhenU. This was cited as the worst sort of evil by the fundamentalist freeware camp. Yet when it later came out that Lavasoft (makers of AdAware, the symbol of all that is good and holy among the anti-corporate netheads) had come to a similar agreement, there wasnt quite the same uproar.
Despite this, I more or less agree that its not a bad idea to run an freeware anti-spyware program on your computer.
What Stinks About Non-Commercial Software
Two things detract from non-commercial products:
1. They just dont work as well companies that give their software away for free depend on volunteer work, which generally isnt available in the same quantity as paid development.
2. Poor Support If you run into a problem, youre on your own. Support costs money.
So What Should I Do Already?
If youve read this far, then my recommendations will make a lot of sense to you:
First, use two spyware removers. Using just one will probably leave you with gaps in coverage, while running three provides little extra protection and will just slow your computer down.
Second, make one of those programs a commercial product. Not only will you get better (although not perfect) protection, youll get customer support in case anything goes wrong. Good products are sold by Aluria, PC Tools, and Webroot click here for our latest testing results.
Third, make one of those programs a non-commercial product. Youll have some reassurance that commercial ties arent compromising your protection and perhaps the satisfaction of putting a smile on a developers face somewhere. There are three primary options: Microsoft Antispyware, Lavasoft AdAware, and Spybot S&D. Hands down, you should use Microsoft Antispyware its a much better product that the other two. And even though Microsoft isnt a non-profit, the program is free and its very good.
November 17, 2005
Major download sites get tough on spyware
Some of the largest names on the Internet have come together to crack down on the spread of adware and spyware through piggybacking hidden software along with legitimate downloads.
The companies, which include Yahoo!, AOL, Verizon and CNet Networks - which operates the large downloads.com software library - have agreed to establish industry standards for monitoring and enforcing good behaviour on sites which offer downloadable software.
A new code of practice maintained by the Truste independent online trust body will mean that sites that offer downloads will have to state clearly if the download contains adware or trackware. In addition, the site must inform the user of the types of advertising that will be displayed, any personal information that will be tracked and collected. The site should also warn of any change in the user settings. Finally, the user must have to opt in with their permission before the download can begin.
Once the software is installed, the publisher must offer an easy uninstall procedure with clear instructions. Any ads have to be labelled with the name of the adware program. Any publisher who wants to take part in the programme will have to maintain separate advertising inventory for users of certified applications.
It is thought unlikely that the spyware companies are going to be leaping for joy at these new guidelines. To enforce compliance, the major portals involved in the Trusted Download Program will publish a 'whitelist' of certified applications. Any application that is not on the whitelist risks being ..errr..blacklisted by the portals that will severely restrict their reach.
However, many spyware applications will not go through legitimate high profile sources as they propagate p2p networks, warez and pornography sites. The portals can claim they have banished spyware from their own servers even if it continues to flourish elsewhere.
Truste says the programme is expected to launch in beta form early in the New Year.
November 16, 2005
New Reviews Underway...
We just took a trip to CompUSA and came back with a ton of new products, including Cosmi's Spyware Killer Pro and a stack of DVD Copying utilities. Look for more reviews in the next two weeks!
October 28, 2005
Anti-Spyware Group Pushes Guidelines
by Wendy Davis, Friday, Oct 28, 2005 6:01 AM EST
MORE THAN SIX MONTHS AFTER it formed, an anti-spyware group headed by the Center for Democracy and Technology, the Anti-Spyware Coalition, released guidelines Thursday designed to assess how to evaluate spyware and other potentially unwanted software programs. The group's guidelines carry no legal weight, but might be influential with some members--like Aluria and Lavasoft--that manufacture anti-spyware removal software.
The proposed standards don't spell out whether any particular product should be classified as harmful, but instead provide various risk factors--a laundry list of traits of software programs, with each trait assessed for its degree of risk.
"The risk factors have general weights (high, medium, and low) that help show the relative impact to the user," states the document. "Although all behaviors can be problematic if unauthorized, certain ones tend to have a greater impact and are treated with more severity than others."
When programs serve pop-up ads, one of the key indicators of potential harm is whether the pop-ups "are clearly attributed to the source program," according to the guidelines.
The guidelines also look at factors that could indicate whether consumers have consented to the programs. For instance, in the case of bundled programs, one factor is whether consumers have opted-in to receive the bundled software (considered a high indication of consent) or whether consumers' only notification about bundled software came in an end-user license agreement (considered a low indication of consumer consent).
Similarly, the easier a program is to remove, the more likely it is that the consumer has consented to the program, according to the guidelines.
The organization is accepting comments on the guidelines through Nov. 27.
October 26, 2005
New Site Launch In Progress
The new site launch is now underway and we'd like to get your feedback. We're now pointing all of our firewall reviews to the new site located at GoorooReviews.com. The content is the same, but the design is a lot cleaner and everything is now organized by subject matter.
Why a new site? Because we're finding it hard to fit everything on this one. If you look at the left navbar, you can see how crowded it's getting with the different categories (anti-spyware, firewalls, anti-spam). We have a ton more categories that we'd like to cover (including anti-virus and system utilities), but there's just too much for a single page.
Anyway, let us know what you think. You can email us at or simply fill out the comment form. Thanks!
October 10, 2005
Spybot S&D v1.4
| Product: Spybot S&D 1.4 Price: Free Editor Rating: 2 stars |
 Click for more info |
Pros
+ Free
+ Instability problems from v1.3 cleared up
Cons
- Ineffective against most spyware
- Infrequent updates
- No customer support
- Scheduler doesnt work
Review
Spybot S&D 1.4, a freeware spyware removal tool, provides poor protection against spyware. While it is incrementally better than the previous version, it detected only 41% of our test spyware and disabled only 27% of it. While the serious instability problems of v1.3 seem to have gone away, the bottom line is this program isn't very effective at removing spyware.
Usability
After installing Spybot S&D, you are presented with a 7 step wizard. You should probably agree with most of these steps, as they are generally conducive to the proper functioning of the program (definitely scan for new updates, for instance).
The v1.4 interface is basically identical to the previous version, although the graphics have been cleaned up somewhat (Click here to see screenshots from 1.3). Although the interface isn't as flashy as some other products', Spybot correctly assumes that most people are interested in doing just one thing: removing spyware. They hide all the clutter in the advanced mode. We would have liked to see the scheduler added to the basic mode interface, and this remains a serious ommission in the program.
The first time we ran Spybot S&D 1.4, it failed to find anything on our heavily infested test computer. We had to reboot before the program would work properly.
If spyware could laugh, it would've laughed here. Spybot S&D failed to find anything the first time we ran it, despite the many obvious problems on this computer.
Removal
As of October 2005, Spybot S&D detects 30,143 spyware signatures. Spybot experts usually recommend that the program should be run in conjunction with another spyware removal program (typically Adaware) in order to provide reasonable protection, although our tests indicate that Spybot is probably no longer capable of removing anything that AdAware (or other good products) can't.
Spybot v1.4 is still pretty fast (although not as quick as v1.3) - it completed a full scan in about 14 minutes. Unfortunately, it doesnt appear to do a complete scan on your system. Instead, it looks in the most common areas only. While the end result is faster, we would prefer to have a more thorough scan along with the ability to schedule it during off hours.
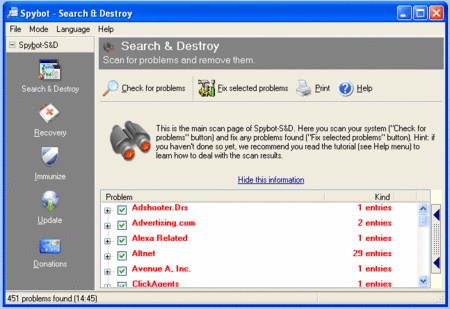
Spybot S&D Results Screen
Spybot S&D v1.4 didn't do a very good job of removing spyware. It detected 41% of the known spyware on our test PC, but disabled only about 27% of it. After three scans and a reboot, there were plenty of toolbars and other nasties still lingering on this computer, as you can see in the screenshot below.
After three scans and a reboot, most of the spyware remained functional on this computer.
Immunization
Spybot S&D provides limited immunization functionality. It does not monitor your RAM or stop browser hijackings in progress. It does purportedly block against about 1,800 browser helper objects that could embed themselves into Internet Explorer, and has an interesting feature to block known bad addresses in the browser, although we question the usefulness of this feature.
Rollback
Spybot S&D does provide rollback capabilities within the program, but in our tests it didnt save all of the tracking cookies that it deleted. However, Spybot S&D does create a checkpoint using Windows XPs system restore functionality, so in a bad situation, you should be able to restore your PC to a previous state.
Other Options
It took us awhile to find the options area (hint: "Mode" menu, then "advanced mode"). This is a nice feature if you want to exercise serious control over the most minute aspects of the program. Our complaint here is that many are trivial or poorly implemented (such as the "skins" functionality). However, one critical feature, the scheduler, didn't work at all on either of our test PCs. We would prefer that the Spybot writers focus their effort on improving the effectiveness of the product rather than including so many bells-and-whistles.
Support
The program was well laid out so a lot of documentation isnt necessary. In addition, Spybot seems to support more languages than any other product we tested.
However, there is the usual complaint with freeware products: non-existent support. If you run into issues with the product, you will have to go online and wade through a developers forum and hope someone there can (and is nice enough to) solve your problem. Support emails to the company went unanswered.
Summary
Spybot S&D v1.4 seems to be little more than a cosmetic upgrade of v1.3. It's effectiveness leaves a lot to be desired and other programs do a much better job of restoring an infected PC. Spybot provides only average protection, infrequent updates, and non-existent support. Lacking so much as a scheduler, this barebones program is hardly worth the download.
Sadly, Spybot S&Ds source code has been appropriated by a number of other vendors who continue to shamelessly market it as their own. Don't fall for this. Check out our list of rogue vendors, and if you were considering purchasing any of the products on that list, don't - either purchase one of our recommended commercial products or at a minimum, download Spybot's offering.
Price: Free
October 09, 2005
Adaware SE Review
|
Product: Adaware SE 1.06 Price: $39.95 Vendor: Lavasoft Editor Rating: 2 1/2 stars Download adaware SE |
 Click for more info |
Pros
+ Improved user interface over previous versions.
Cons
- Average protection against spyware
- Confusing user interface. Most of adawares useful functionality is hidden from the average user.
- Doesn't support scheduled scans - you have to wait to use your computer until the program is done scanning.
- Poor customer support
- High price compared to most products
Adaware Review
Adaware SE, the latest update to adaware's flagship product, is a good product that provides decent protection against many spyware programs, but lacks some important functionality such as the ability to schedule scans. The user interface is difficult to use and might appeal more to people comfortable with computers.
It can detect spyware programs running in memory, examine startup settings, block browser hijackings, remove tracking cookies, and fix registry changes made by intruding programs. It can also remove stubborn spyware by flagging it for deletion (before it loads) during the next bootup cycle.
Our October, 2005 test results indicated that adaware protects against many common spyware programs and offers above average effectiveness against spyware infestation.
Adawares real-time monitoring (immunization) is not as effective as other products and was difficult to locate and configure. It does block browser hijackings, protect important registry settings, and block suspicious processes, and it even has functionality to scan for spyware in memory (but this is very limited). During our tests, it did successfully detect in-process spyware, but it was often unable to stop them from running.
Usability
Lavasoft has made significant improvements in the user interface with the latest version (1.06) of adaware. Many of the cryptic and non-working buttons (such as "ProcWatch") are gone, although some remain (such as the "Add-ons" button). Nevertheless, the program retains the same "techie" feel that reflects its roots as one of the original anti-spyware programs.
Because it offers too many options, AdAware's interface might be confusing to some.
Removal
Scanning was extremely fast completing in about 6 minutes on our Windows 2000 test PC.
While Adaware claims to detect more spyware programs than other vendors, in our tests it failed to find a number of unwanted browser plug-ins (such as the "Websearch toolbar") that other products correctly detected. In our formal Spyware Effectiveness Test, adaware detected 68% of common spyware and disabled 50% of it. Although this was an improvement over our June results, it leaves a lot to be desired. This gap in effectiveness is the reason many spyware experts recommend that you run adaware in conjunction with another product.
Other applications responded very sluggishly while scanning was being performed. This would not be as much of a problem if scans could be scheduled, but the current version supports only on-demand and startup scans. If you are running a laptop or a slow desktop, this is probably not the product for you because you will have to manually start adaware (or have it auto-start when you boot up) and wait to use your computer until it finishes.
After two scans and a reboot, there were still plenty of toolbars left installed. Popups remained a problem as well.
Certain common applications (such as the free Real Player) will not function properly without their embedded spyware. If you run adaware (or any other spyware remover), you may find that these applications will no longer run. Fortunately, adaware quarantines all spyware so that you can restore it later if necessary.
Other Options
As stated above, adaware has made signficant improvements with the user interface. The options settings which were so hard to find in the previous version of adaware, have now been clearly relocated to their own icon at the top of the form. They've even replaced many of the confusing nested options screens with simple interfaces that are much easier to understand.
However, as with previous versions, the options offered are more suited to people who are very comfortable working with computers. For instance, because spyware scanning is time consuming, the most basic and important feature any spyware program could have is the ability to schedule scans when you are not around. Adaware lacks this basic and necessary functionality.
Instead, it offers a variety of infrequently used options. Do you want to place your log files in specific locations? Would you prefer to scan your registry, or deep scan it? How about your hosts file? None of these features offers any real value, and it feels like Lavasoft has missed the boat in terms of usability.
Adaware offers a lot of advanced options, but nothing really useful - not even a scheduler.
Summary
Lavasoft's adaware SE is a huge improvement over previous versions in terms of usability, but still lags behind the top products in terms of sheer effectiveness. It is a better product than most others on the market, but its lack of scheduling ability, average real-time monitoring, and complex user interface detract from its sheer power. It's an ok backup program, but for a better free product, try Microsoft AntiSpyware.
Purchase Price: $39.95
Download adaware
SpyZooka 2.4 Review
|
Product: SpyZooka 2.4 Price: $29.95 Company Info: Blue Penguin Editor Rating: 0 stars Download Now! |
 Click for more info |
+ Fast scan
+ 100% removal guarantee
Cons
- We couldn't get it to remove a single spyware program
SpyZooka 2.4 Product Review
SpyZooka is one of the latest anti-spyware programs to hit the market. The company offers a money-back guarantee if they can't remove 100% of all spyware from your PC within 24 hours, however we couldn't get it to remove a thing from our spyware infested test computer.
Usability
SpyZooka installed without a hitch on our test computer.
A full system scan took less than 2 minutes on our PC. This was extremely quick, and we remain skeptical when an anti-spyware product completes a scan this quickly as it usually means that many files were skipped.
We found some major usability problems with this program. The "scan" buttons are text only and difficult to find. After completing a scan, we minimized the program and it disappeared completely from our desktop (solution: restore it from the system tray). And perhaps worst of all, after a complete scan and removal, there was no status update. The program just returned to the scan results screen. Overall, we found this product to be not nearly as well designed as other anti-spyware programs.
SpyZooka's user interface left a lot to be desired.
Removal
Unfortunately, SpyZooka did very poorly with our Spyware Effectiveness Test. Although it did detect a good number of the spyware programs on our text computer (68%), it failed to remove a single one of them!
SpyZooka failed to remove even a single toolbar from our seriously screwed up browser.
Rollback
SpyZooka doesn't offer any rollback functionality whatsoever.
Other Options
SpyZooka lacks the most basic functionality, such as a scheduler. It does include a few other system tools, but the average person probably won't make use of these.
Summary
SpyZooka is extremely lightweight. lacking both a scheduler and rollback functionality, and bears the marks of being a brand new product. Although it detected nearly 70% of the spyware on our test platform, it failed to remove any of it. Despite the company's money-back guarantee, we recommend that you shop elsewhere.
Purchase Price: $29.95
Download Now!
Security Suites are Rife With Problems
Editor's Comment: We have long noticed that the integrated security suites simply don't work that well. Almost everyone of them consists of a single good program cobbled together with a number of sub-standard software packages. This is why we recommend that you purchase your anti-spyware, anti-virus, anti-spam, and firewall programs separately.
To see our top recommendations, click on the following links: anti-spyware, firewall, anti-spam.
Note: Due to the effort needed to test anti-virus programs, we don't have a good recommendation in that category yet. Is this something you'd like to see? Let us know at
Security Suites Are Rife With Problems
By Rob Pegoraro
WashingtonPost.com
Sunday, October 9, 2005
If security software is so necessary in Windows -- as it is -- why are we supposed to pay extra for it?
For years, that's been a paradox Windows users have been able to mull over as they sat through installations of other companies' security software on their computers.
Symantec's and McAfee's security software programs have long benefited from Microsoft's oversights. Both firms supply the antivirus programs offered in trial form on most new PCs-- and which help advertise their full-fledged security suites.
But the 2006 editions of these suites --McAfee Internet Security Suite 2006, $50 as a download or $70 as a box for Win 98 or newer; Symantec's Norton Internet Security 2006, $70 for Win 2000 and XP -- look unworthy of that success.
For one thing, they face competition from Microsoft, which last year added effective firewall protection to Windows XP with its Service Pack 2 update and has since released a surprisingly good (though still in beta test) anti-spyware tool.
For another, the complexity of the Symantec and McAfee suites seems to cause them to fail in ugly and destructive ways, according to readers who have written in to complain about these problems week after month after year.
Most important, the latest McAfee and Symantec suites just don't work all that well.
Both excel only in their antivirus utilities-- which you can buy separately from these all-purpose bundles. Each program correctly blocked viruses received via e-mail in two different e-mail applications and via AOL's AIM instant-messenger software. Each also automatically fetched updates to its virus database every day.
Symantec's Norton AntiVirus, however, was quicker about its business, cleanly killing viruses with just brief notifications afterwards. Symantec's installer, unlike McAfee's, also scanned the computer for viruses before setting up the program, a sensible precaution.
McAfee VirusScan, meanwhile, asked what it should do every time it found a virus-- as if the choice should ever not be "delete." Downloading antivirus updates manually required setting Internet Explorer as the default browser, turning off pop-up blocking and accepting the installation of an ActiveX program from McAfee's site -- everything you shouldn't be in the habit of doing if you want to stay safe online.
Things get worse in the rest of the McAfee and Symantec suites.
Their firewalls, intended to stop worms from crawling onto your computers, offer no more protection against intrusions than the one in Win XP Service Pack 2. Their advantage comes if a program has already moved in, when they can stop it from communicating with its creators. But these firewalls first need to learn which ones are safe so as not to nag you about the harmless activity of legitimate software.
Symantec's firewall tries to educate itself with a one-week "learning mode," when the firewall watches your use and stops only known offenders. After that, it will flag unknown programs that attempt to contact anything online -- but its default recommendation will be to give them free rein.
McAfee's firewall comes with a whitelist of known-good applications, but this database was laughably incomplete -- among others, it failed to recognize the Mozilla Thunderbird e-mail program, the Spybot Search & Destroy spyware scanner and the WeatherBug forecast look-up tool.
These two suites attempt to police spyware -- programs activated without your consent when you install allegedly free software downloaded from some Internet sites -- but did so no better than free alternatives.
Neither dislodged an infection by one of the most tenacious spyware offenders, Aurora/A Better Internet, but McAfee was particularly woeful. It allowed this parasite to launch repeated pop-up ads -- including one, apparently bought by a third-party retailer, for McAfee's security utilities! -- and was conned by Aurora into blocking access to the download page for Microsoft AntiSpyware.
McAfee and Symantec's filters against phishing (in which thieves set up pages impersonating the Web sites of financial institutions to get you to cough up personal data) seem even less effective. Neither flagged obviously fake PayPal-look-alike scams.
Symantec and McAfee also tout spam filtering, but that applies only if you use the two mail programs they support-- Microsoft's antiquated Outlook Express and bloated Outlook. In addition, their filters assume your e-mail account runs on the Post Office Protocol standard, ignoring a newer, more convenient standard called IMAP.
McAfee's spam filter used an unnecessarily convoluted setup and didn't allow the encrypted login required by a test Gmail account.
The two security bundles can filter out ads on Web pages as well as in e-mail. Symantec's ad-blocking did zap many of the more annoying commercials online, but at the cost of erasing non-ad graphics on occasion. McAfee's ad-blocking, however, routinely dismantled innocent graphics -- including the masthead graphic at the top of The Post's home page-- while allowing plenty of real ads to sail through.
Don't bother with Symantec's weak parental controls. They offer only vague categories of restrictions on Web sites and programs, without telling what it bans in each area (although you can also block individual sites and applications of your choice), and can't enforce time limits on a kid's computer use.
Neither suite is too pleasant to live with when not blocking threats. Symantec's interface works way too hard at selling other Symantec applications, while McAfee's requires opening window after window to check or adjust its many settings. And the two companies' tech-support policies rank among the stingiest ever.
Both charge fees for all phone calls, unless they decide it was their software at fault, and provide only limited access to live help online (McAfee's live chats are as difficult to connect to as its manual update downloads).
If you're running Windows XP, you're better off sticking with the firewall built into SP2, then downloading Microsoft's AntiSpyware and using a mail program with a built-in spam filter, such as Microsoft's Outlook 2003, Qualcomm's Eudora or the free Thunderbird. Then run whatever antivirus program came with your machine. If one isn't active, Symantec is better than McAfee (I plan to review other antivirus utilities soon).
If you're not running XP, go with the McAfee suite for now. But think hard about whether you actually need to run Windows on your next computer. Compared with dealing with these programs, life with Mac OS X or Linux -- both blissfully free of spyware and viruses --may look awfully appealing.
September 20, 2005
Who's watching you?
Angus Kidman
SEPTEMBER 20, 2005
THERE'S nothing more likely to get computer users fired up than the thought that someone is stealing their data.
Our fear that personal and financial information could be grabbed without our knowledge goes a long way towards explaining why spyware (software that tracks what we type, where we visit and what we do on our computers) has grabbed so many headlines this year.
"Spyware has evolved from being an occasional nuisance to something that wastes IT user and technical support resources, and compromises the integrity of corporate systems, applications and data," say Gartner analysts John Girard and Mark Nicolett.
A study last year by IDC estimated that 67 per cent of PCs were infected with spyware.
Other sources say the incidence is as high as 90 per cent.
The 2004 SpyAudit report, collated from internet service provider data, suggests that system monitors, a common type of spyware, proliferated by 230 per cent during the year.
Disentangling these claims is difficult, in no small part because there's little consensus on a definition of spyware.
Spyware is any piece of unwanted software that tracks user activity, such as a keystroke logger that stores everything you type, or a package that notes every website you visit, and then sends that information to a third party.
The term is often used more lazily to include any program or website that serves up unexpected advertising, or even to cover websites that use cookies to store information about recent visits.
A study by software developer Eblocs finds that 98 per cent of pornographic sites contain some form of spyware or adware (although we'd venture to suggest adware is the dominant offender).
Ad-supported software is widely distributed on the internet, and although some of these programs merely exist as a smokescreen to collect information and sell advertising, others, such as the popular browser Opera, legitimately employ ads as an alternative to users paying for the program.
An aditional complication is that many software developers claim that there are legitimate reasons for automatically collecting information.
Microsoft, for instance, encourages users to submit data about usage and error messages to facilitate product development plans, but allows users to opt out, something that true spyware is at pains to avoid.
Many vendors argue spyware is more effectively handled by general antivirus and security packages rather than with specific tools, because it often intersects with these areas.
Experts agree, however, that PCs infected with the more malicious forms of spyware represent a threat not just to the privacy of individual users, but to the internet at large.
Read the rest of this article at the Australian
September 13, 2005
Qurb 3.0 Review
Product: Qurb 3.0
Vendor: Qurb
Price: $29.95
Editor Rating: 1 star
Prosa
+ Simple user interface
+ Integrates directly into your email client
Cons
- Frequently quarantines legitimate email
- Poor protection against spam
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
We tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
Qurb installed perfectly the first time. It correctly found our email clients and integrated into each one. The first time we ran Outlook Express, it popped up a helpful screen of information teaching us how to get started:

Usability
Qurb was easy to use. Like Spam Inspector, it installed a toolbar directly into Outlook Express with just two buttons, "Approve" and "Block":
![]()
Training
Immediately after installing Qurb for the first time, we downloaded 96 spam emails and 4 legitimate emails from our test account. It quarantined all 100 emails, including the legitimate ones. Qurb placed all of the emails into a new folder appropriately named Qurb.
We then trained the software by using the "approve" button on the legitimate emails and the "block" button on the spam and then imported an additional 291 spam email and 15 legitimate emails.
Qurbs results were a little unexpected in that it tended to allow spam through and block legitimate email. Overall, it quarantined 74 of the emails (26%), including 13 of the legitimate emails. The only legitimate emails that it allowed to pass were ones that we had flagged in the training session.
Our tests indicate that this product is little more than an address blocker, which means that you will spend quite a bit of time going through your quarantine folder to look for legitimate email.
Other Features
Qurb has a built-in update feature, but overall it is lacking in functionality.
Summary
Qurb blocked a low percentage of spam in our tests and tended to quarantine legitimate email from senders we didnt explicitly put in our approved senders list.
Price: $29.95
Free Trial: YES
Spam Eater Pro Review
Product: SpamEater Pro
Vendor: High Mountain Software
Price: $24.95
Editor Rating: 1 stars
Pros
+ None!
Cons
- Mediocre protection against spam
- Standalone program - does not integrate with your email account
- Extremely slow took hours to filter even a small number of emails.
- User interface very poor
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
SpamEater Pro installed perfectly out of the box.
Usability
Spam Eater does not integrate into your email program. Instead, to use it you open a separate program which occasionally queries your email provider and removes spam messages from your account. We found that having to run two programs (our email program and Spam Eater Pro) was cumbersome. It is also a problem if you access the same email account from two different locations, because the email that is removed can only be accessed from one location. Should Spam Eater Pro block legitimate emails, they will not be accessible from other mailboxes.
We were decidedly negative about the user interface. The status window could not be minimized or hidden, nor was there any way to cancel an update short of using ctrl-alt-delete. The primary results window did not appear in the task bar. And in the main window, each email is flagged with a cryptic icon E or F (we still arent sure what this means). Clicking on the column headers allows you to sort that column, as is typical in most windows applications, but the column headers were also combined with dropdown boxes. Not only is this confusing, the dropdown isnt wide enough to read the contents. It was little things such as this that made the program feel cumbersome and difficult to use.

Training
Spam Eater did not support any type of automated training ability. Instead, you are forced to manually enter a new rule for every different type of spam email. Because of this, we couldnt see ourselves using this product on a long-term basis.
We then attempted to login to our test email account using the product. After downloading seven emails the program hung. We stopped and started the program several times, but we were never able to complete the testing process. Finally, we started it again and allowed it to run overnight. When we returned in the morning, the program had successfully cycled through our emails.
Of the 96 spam and 4 legitimate emails, Spam Eater Pro blocked 57 and allowed the 4 legitimate emails (57% accuracy).
No training options are available, so we then proceeded to filter an additional 291 spam and 15 legitimate emails, again allowing the program to run overnight. Spam Eater Pro blocked 154 (53%) of the spam (but did allow the legitimate email through). These were among the poorest results of any of the products we tested.
Other Features
Spam Eater Pro was lacking in functionality. The only type of rule it supported was checking for literal strings of characters spammers have long since figured out how to beat this type of filtering technology.
Another important piece of functionality that Spam Eater Pro is missing is the ability to share spam rules with other users. This dramatically increases the accuracy of spam filtering, and without it, the accuracy of the filter drops.
Summary
Spam Eater Pro provided poor protection against spam, scored poorly for usability, and was among the slowest of the products we tested. For a few dollars more, you are better off with one of our top picks.
Price: $24.95
Free Trial: YES
Spam Butcher Review
Product: Spam Butcher 1.7
Vendor: Spam Butcher
Price: $29.95
Editor Rating: 2 stars
Pros
+ None!
Cons
- Below average protection against spam
- Does not integrate into email client
- Minimal functionality
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
SpamButcher installed perfectly the first time. After we installed, it asked us for our email address and automatically configured itself. SpamButcher requires your password to auto-configure, but this information is not accessible by anyone else.
Usability
SpamButcher does not integrate into your email client. Instead, it runs in the background and periodically checks your email, removing any spam it finds. Like other spam filtering programs that utilize this approach (as opposed to direct integration into your email client), this can cause problems for you if you use the same email account from different locations, especially if you need to locate a legitimate email that was blocked accidentally.
This product had one very annoying feature. You have to click on the system tray to examine your spam, because it doesnt appear in the task bar, nor can you alt-tab to it.

Training
After installing SpamButcher for the first time, we downloaded 96 spam emails and 4 legitimate emails from our test account. It quarantined 35 spam emails (36% accuracy) and also blocked all of our legitimate email. Not a good start.
After recovering our blocked email, we then imported an additional 291 spam email and 15 legitimate emails. SpamButcher quarantined 122 of them (42%) and allowed 11 of the legitimate emails to pass through. This wasnt nearly as good as other products we tested.
Other Features
The product was light on features. It does not have a community feature nor some of the more advanced algorithms that our other top ranked products have.
Summary
Spam Butcher provided average protection against spam. It is a light on features and higher priced than other more effective products.
Price: $39.95
Free Trial: YES
Cloudmark Desktop
Product: Cloudmark Desktop
Vendor: Cloudmark
Price: $39.95 (1-year subscription)
Editor Rating: 3 stars
Pros
+ Very good protection against spam.
Cons
- Light on extra features, such as reporting spam abuse
- Leaving messages on server causes them to be re-downloaded on every refresh
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
Cloudmark installed perfectly the first time. It installed seamlessly into both Outlook and Outlook Express.
Usability
Like other good spam filtering applications, Cloudmark was very easy to use. It installed a toolbar directly into Outlook Express with just two buttons, Block and Unblock (it also had an options button):
![]()
We did have a very big technical problem with Cloudmark. We use our email accounts from both work and home, and in order to ensure that we have access to them at both locations, weve configured our email clients to leave the messages for five days on the server instead of removing them. Cloudmark would download the same messages each time from the server. This product would be much better if it remembered which email it had already checked.
Training
After installing Cloudmark for the first time, we downloaded 96 spam emails and 4 legitimate emails from our test account. It correctly quarantined 50 of the spam emails (52%) and allowed the legitimate emails through.
We then selected the 46 spam messages and clicked on the block button. This sends information about the spam emails back to Cloudmark. Each time you block an email, it counts as a vote. When a spam email gets enough negative votes from users, SpamNet will then filter it from everyones email inbox. At least, this is how it works in theory. The real test came next.
We then imported an additional 291 spam email and 15 legitimate emails. Cloudmark quarantined 238 of them (82%) and allowed all of the legitimate emails to pass through much better than the initial test. It allowed some spam through, such as a faked Yahoo forum newsletter, several Viagara ads, mortgage solicitations, as well as an ad for an adult website.
Other Features
Cloudmark does little more than filter spam. It doesnt give you the ability to report spammers, and while there is a whitelist feature that lets you tell SpamNet which addresses to always allow, it is very basic. For instance, you cant allow or disallow certain domain names or servers.
Summary
Cloudmark provided very good protection, although not perfect. It lacks any additional features beyond spam filtering and is priced higher than other good programs.
Price: $39.95 (1 year subscription)
Free Trial: YES
Matador 4.1
 |
Product: Matador 4.1 Vendor: MailFrontier Price: $39.95 Editor Rating: 3 stars Free Trial Link |
Pros
+ Blocks most spam and allows legitimate mail through
+ Integrates into Outlook and Outlook Express
Cons
- Light functionality
- Good protection, but not as good as other products
- Higher priced than other products
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a larger set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
Matador installed perfectly the first time. It installed seamlessly into Outlook Express and asked if we wanted to import our address book the first time we started our email client.
Usability
Like other good spam filtering applications, Matador was very easy to use. It installed a toolbar directly into Outlook Express with just two buttons, junk and Unjunk (it also had an options button):
![]()
Training
After installing Matador for the first time, we downloaded 96 spam emails and 4 legitimate emails from our test account. It correctly quarantined 94 of the spam emails and allowed the legitimate emails through.
Matador didnt need any training, so we then imported an additional 291 spam email and 15 legitimate emails. Matador quarantined 238 of them (82%) and allowed all of the legitimate emails to pass through a respectable showing. However, it failed to stop some blatantly pornographic spam making this a risky choice if you have children.
Other Features
The product was a little light on other features. It does not have a community feature nor some of the more advanced algorithms that our other top ranked products have.
Summary
Matador 4.1 provides very good protection and stopped most of the spam email that we tested with. However, we ranked it lower because it was lacking in features and was higher priced than other more effective products.
Price: $39.95
Free Trial: YES
McAfee SpamKiller
 |
Product: SpamKiller Vendor: McAfee Price: $34.99(1-year subscription) Editor Rating: 3 1/2 stars |
Pros
+ Near perfect protection against spam
+ Lots of useful added features, such as abuse reporting.
Cons
- High price
- Difficult installation
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
SpamKiller was a pain in the butt to install. The McAfee website makes use of an ActiveX installer and pop-ups. It took us awhile to figure out that we had to disable our anti-spyware tool (Webroot's Spy Sweeper - click here for a review) and our pop-up stopper before the software would install properly. However, once we got around this issue, the software installed without any further difficulties. SpamKiller detected our existing email accounts and imported our address books automatically.
Usability
Spam filtering software generally comes in two flavors. The first kind is embedded entirely within your email client. The second runs in the background and periodically polls your email server and removes spam when you find it.
SpamKiller is a hybrid. One portion of the program locates each of your email accounts and then runs in the background, removing spam. The other is embedded in your webbrowser, giving you an easy way to block spam that has made it through the filter from directly within your email client.
The user interface for Spam Killer was very pleasing. As with all of their products, McAfee devotes considerable attention to design.

Training
After installing SpamKiller for the first time, we downloaded 96 spam emails and 4 legitimate emails from our test account. It correctly quarantined all of the spam emails (100%) and allowed the legitimate emails through. This was a perfect result!
We then added our second test account to Spam Killer. This account had 291 spam emails and 15 legitimate ones as well. Spam Killer quarantined 268 of them (92%) and allowed all of the legitimate emails to pass through. These results were the second best of all the products we tested.
Other Features
SpamKiller has many additional features, including a nice reporting interface. Like Spam Inspector, Spam Killer allows you to report spammers to their ISPs, although this functionality isnt as nice or as complete as Spam Inspector. Spam Killer also has a very easy to understand rules interface that can allow you to easily customize your filtering should you so desire.

Summary
SpamKiller provides near perfect protection against spam and many additional useful features. It is expensive however and the purchase price only includes a one-year subscription, but we found it to be an excellent product.
Price: $34.99
Free Trial: No
EmailProtect Review
 |
Product: EmailProtect Price: $29.99 Company Info: Content Watch Editor Rating: 4 stars |
Pros
+ "Behind the scenes" integration with your email client - no buttons or menus.
+ Provides excellent spam filtering capabilities
Cons
- Tends to block opt-in newsletters
Review
We test each spam filter by first sending 100 spam emails to a test account with the spam filter installed. If necessary, we then train the product, typically by pressing a button marking the email as spam. After the training process is complete, we then send a different set of spam emails to the same account to determine the overall effectiveness of the product.
If applicable, we tested each spam filter on Outlook Express, Eudora, and Yahoo.
Installation
Installation proceeded without a hitch, but Email Protect forced us to enter an email address in order to get a trial key.
Usability
EmailProtect does not integrate into your email client. Instead, it runs in the system background and monitors incoming email. When it finds spam, it replaces it with an email indicating that it has blocked the message. You then need to open up the Email Protect interface to read it. While this approach does work, your inbox is still cluttered with blocked messages. If you purchase this program, we suggest that you set up a rule to move blocked spam into a separate folder (and we hope that Content Watch builds this functionality into the next version of their software).
Training
Of the 96 spam and 4 legitimate emails, EmailProtect blocked 90 and allowed 3 of the legitimate emails (97% accuracy). Of the four legitimate emails were passed, the one which was blocked was an opt-in newsletter.
No training options are available, so we then proceeded to filter an additional 291 spam and 15 legitimate emails, again allowing the program to run overnight. EmailProtect blocked 282 of them (97% accuracy). Nine spam emails made it through, but so did all of our legitimate email (with the exception of 3 opt-in newsletters). Overall, EmailProtect did a decent job.
Other Features
EmailProtect has an interesting feature called "category blocking", which allows you to pass or block spam emails in different categories (we did not test this feature to determine its effectiveness). It can also block specific email addresses or emails with forbidden words.
Like most of the products we tested, EmailProtect did not include any reporting functionality.
Summary
EmailProtect provides excellent protection against spam and has more functionality than most products.
Price: $29.99
Free Trial: YES
September 03, 2005
GotoMyPC Review
|
Product: GotoMyPC Price: $19.95/month (1 PC) Company Info: Citrix Editor Rating: 4 stars |
Pros
+ Extremely easy to use
+ Works over company firewalls
+ Quickest and easiest remote access software available
Cons
- High resolution displays will update slowly
- Clipboard doesn't transfer between PCs
GotoMyPC Product Review
GotoMyPC is probably the most well-known product that allows you to access one PC remotely from another. With it, you can be at home and use your PC at work as if you were sitting in front of it. It's perfect for use at the airport, Starbucks, or anywhere you can access the internet. So what's the catch? You will probably find the connection to be a little sluggish, certainly not as responsive as being in front of the computer. Nevertheless, this is an excellent software product that meets an everyday need.
Installation
Installation is super easy. Just set up an account at the website, and download the software. You'll need a credit card to try it out and you should be aware that you'll be able to use the system for free for up to 60 minutes of connect time, or 30 days, whichever comes first. This is convenient if you find the program to be of value, but if not, be sure to send a cancellation notice to them using their contact form.
Once you finish setting up your account, you'll be presented with a download link. This installs a small program on your PC which has the hosting software. After that, you'll probably need to reboot your computer and you're done! Total setup time takes less than 5 minutes.
When your computer restarts, you'll see a new icon in the system tray. This icon lets you know that your computer is accessible over the internet.
Connecting
Connecting to your computer is equally easy. Head to their website and login with your account information. If this is the first time you've used GotoMyPC from this computer, you'll have to download a small viewer application.
Once this is done, you'll be connected with your original PC.
Usability
Overall, we like this program. It is very simple and Citrix wisely decided not to overwhelm us with too many features. The features that are there are minimal and easy to use.
For instance, you'll find all the basics, such as File Transfer:
There is also drawing mode, which allows you to draw directly on the screen. This is useful if you are collaborating with someone else on the other end, because it makes it easy to highlight any area you want.
Finally, there is the ability to set up a remote printer. This allows you to print files directly from the remote PC on your local printer. A very handy function for office workers accessing their computers from home.
One drawback with the program is that it can be a little slow. We experienced a 2 second delay after the time that we clicked on links and icons before anything would happen. The problem gets worse with higher resolutions. Nevertheless, this program isn't meant to be used on a continual basis - instead, it allows you to access a remote computer on special occasions, such as when you may have forgotten an important file.
The other feature that was missing was the ability to share the clipboard between computers. This made it difficult to transfer screenshots, or cut-and-paste text snippets from one PC to another.
Other
The great news with this product is that it will work over many company firewalls! This is perfect for office works at larger corporations who maintain tighter security.
Conclusion
Overall, this is a great product. While there are other products available, they can be very difficult to set up or have problems connecting over firewalls. The setup and usage of GotoMyPC is a no-brainer, which makes it one of our top picks.
Purchase Price: $19.95/month for 1 PC
August 26, 2005
Earthlink Acquires Aluria Software
EarthLink Acquires Assets Of Aluria Software
ATLANTAAugust 22nd, 2005 EarthLink (NASDAQ: ELNK), the nations next generation Internet service provider, today announced it has reached an agreement to acquire the assets of Aluria Software, LLC, a privately held developer of protection and security products for consumers, small businesses and enterprise customers.
Aluria is best known for its consumer anti-spyware application, Spyware Eliminator, which, to date, has over 20 million users worldwide. Recently, Aluria launched its first business-targeted application, Paladin, which provides the same innovative, industry-leading anti-spyware protection for small businesses and corporations. The company also sells a number of other security, protection and system optimization applications.
Safety and security have always been central to our award-winning Internet service, and Alurias innovative products will enhance and improve our already robust suite of protection applications, said Matt Cobb, EarthLinks vice president of core applications. Alurias expertise, when combined with our easy-to-use tools, will help protect EarthLink subscribers from online threats like spyware, spam or phisher sites.
Our vision is that people want state-of-the-art Internet security tools that are intuitive and easy-to-use, said Rick Carlson, Aluria Softwares chief executive officer. We think our technology is a perfect fit for the protection services that EarthLink offers.
The agreement and EarthLinks obligation to close the acquisition are subject to certain conditions. The acquisition is expected to close in September, and once completed, the Aluria assets will become a part of a new division of EarthLink.
About Aluria Software
A privately held company founded in 1999 and headquartered in Orlando, Florida. Aluria software is the leading provider of high quality, user-friendly software and is a trusted partner of major associations and corporations. Aluria software protects millions of Internet users worldwide.
About EarthLink
EarthLink. We revolve around you. As the nations next generation Internet service provider, Atlanta-based EarthLink has earned an award-winning reputation for outstanding customer service and its suite of online products and services. Serving over five million subscribers, EarthLink offers what every user should expect from their Internet experience: high-quality connectivity, minimal online intrusions, and customizable features. Whether it's dial-up, high-speed, web hosting, wireless voice and data services, or EarthLink Extras like home networking, security or voice over IP, EarthLink provides the tools that best let individuals use and enjoy the Internet on their own terms. Learn more about EarthLink by calling (800) EARTHLINK or visiting EarthLink's Web site at www.EarthLink.net.
July 06, 2005
FTC shuts down makers of "SpyKiller"
The Federal Trade Commission halts the makers of "SpyKiller", a program that has consistently received some of the lowest marks by AdwareReport.
Scans Detected Spyware That Wasnt There; Spyware Removal Software Claims Were False.
An operation that used bogus scans and illegal spam to market an anti-spyware program that didnt work as claimed has had its assets frozen and been barred from making deceptive claims by a stipulated preliminary injunction order issued by a U.S. District Court judge at the request of the Federal Trade Commission. The agency alleges that the operation violated federal laws and has asked the court to permanently bar the deceptive marketing and order redress for consumers.
The FTC alleges that to capitalize on legitimate consumer concerns about spyware and induce consumers to download its anti-spyware product, SpyKiller, the operation aggressively and deceptively marketed SpyKiller, using the Web sites of affiliates, banner and pop-up ads, and spam.
The FTC alleges defendants sent pop-up and e-mail messages informing consumers that their computers had been remotely scanned and that spyware had been detected even though defendants had not performed any such scans. The defendants marketing materials urged consumers to access the SpyKiller Web site to get a free scan for spyware. While the SpyKiller scan was running, the program displayed a status report entitled Spyware Found on your PC: that included a category called Live Spyware Processes. In fact, the FTC alleges, this category deceptively identified anti-virus programs, word processing programs, or any of the processes running on the system as spyware. Then, even though the scan itself was free, consumers had to pay roughly $39.95 to enable SpyKillers removal capabilities. Defendants promised in their marketing materials that SpyKiller would find and remove all spyware, including all traces of particular spyware on consumers computers. However, the FTC complaint alleges the software failed to remove significant amounts of spyware, including specified spyware defendants claimed on their Web site to remove. The agency alleges that the deceptive claims violate the FTC Act.
The FTC also alleges that spam messages promoting the SpyKiller software contained similar deceptive claims, failed to identify themselves as advertising, used false from lines, gave no valid postal addresses, and failed to provide consumers with notice of and the ability to opt-out, in violation of the CAN-SPAM Act.
The court entered a temporary restraining order on June 1, 2005, and a stipulated preliminary injunction order on June 14, 2005. The agency is seeking a permanent ban on the deceptive claims and will ask the court to order consumer redress from defendants Trustsoft, Inc. and its Houston, Texas-based principal, Danilo Ladendorf.
The FTC held a workshop in April 2004 titled Monitoring Software on Your PC: Spyware, Adware, and Other Software. On March 7, 2005, FTC staff issued a report on the proceedings, and, after reviewing more than 750 comments submitted to supplement the workshop record, the FTC staff has concluded that spyware is a real and growing problem that can impair the operation of computers and create substantial privacy and security risks for consumers information. Copies of the report can be found at http://www.ftc.gov/os/2005/03/050307spywarerpt.pdf Consumers who want to learn more about spyware, including how to detect it, and how to prevent it, can go to http://www.ftc.gov/bcp/conline/pubs/alerts/spywarealrt.htm
The Commission vote to authorize staff to file the complaint was 5-0. The complaint was filed in the U.S. District Court for the Southern District of Texas.
NOTE: The Commission files a complaint when it has reason to believe that the law has been or is being violated, and it appears to the Commission that a proceeding is in the public interest. The complaint is not a finding or ruling that the defendant has actually violated the law. The case will be decided by the court.
Copies of the complaint and stipulated preliminary injunction are available from the FTCs Web site at http://www.ftc.gov and also from the FTCs Consumer Response Center, Room 130, 600 Pennsylvania Avenue, N.W., Washington, D.C. 20580. The FTC works for the consumer to prevent fraudulent, deceptive, and unfair business practices in the marketplace and to provide information to help consumers spot, stop, and avoid them. To file a complaint in English or Spanish (bilingual counselors are available to take complaints), or to get free information on any of 150 consumer topics, call toll-free, 1-877-FTC-HELP (1-877-382-4357), or use the complaint form at http://www.ftc.gov. The FTC enters Internet, telemarketing, identity theft, and other fraud-related complaints into Consumer Sentinel, a secure, online database available to hundreds of civil and criminal law enforcement agencies in the U.S. and abroad
July 01, 2005
October 2005 Anti-Spyware Testing Results
We've again greatly expanded the number of spyware bait programs in the October test with many newer spyware programs that were not around a few months ago. For this reason, most of the scores have dropped well below the 80% range. Don't be put off by a result of 70 or 75% - this is actually quite good. On the other hand, you should stay away from purchasing any product with a score less than 50%.
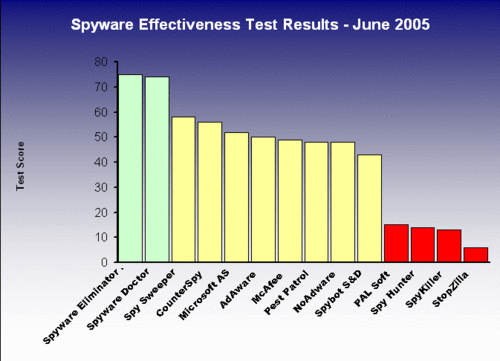
June 05, 2005
Anti-Spyware Coalition to define terms
A new group aims to clear up confusion over spyware and adware, and help end the problem of different anti-spyware tools flagging perceived threats in different ways
Anti-spyware software makers are taking another shot at creating a definition of spyware, this time with help from consumer organizations.
A new group, tentatively named the Anti-Spyware Coalition, plans to publish proposed guidelines later this summer that define spyware, best practices for desktop software development, and a common lexicon.
Debate has gone on for years over spyware and adware, with manufacturers defending some of these applications as legitimate marketing tools. The terms are slippery, frequently used to apply both to the information-thieving software and the often-annoying advertising tools bundled with free software programs.
Both spyware and adware can impact PC performance. They are often surreptitiously installed on computers to gather information about people that is used for advertising or provided to other interested parties. The market for tools to remove the unwanted software is booming.
If the new coalition succeeds, its work could clear up confusion over spyware and adware. Also, the group's work could help software makers and legitimate advertisers improve their products.
While specific examples of legitimate and illegitimate behavior aren't hard to pinpoint, identifying clear categories has proved difficult. "The key benefit is getting a handle on the nature of the problem, (getting) industrywide acceptance on what is accepted and what is not," Fewer said.
In an example of why standard definitions are needed, Computer Associates International earlier this year temporarily removed the Gator adware program from the spyware detected by its PestPatrol program. It has since been put back on CA's list of spyware, and the company has changed the way it deals with appeals from spyware makers.
Drafts of the coalition's guidelines are finished and should be published by the end of the summer, when they will be open to public comments, said Ari Schwartz, an associate director at the Center for Democracy and Technology.
The Anti-Spyware Coalition counts software makers, online businesses and security providers among its members. Watchdog groups are taking part too, but they have an associate role.
The Anti-Spyware Coalition is still in its formative stages, with all the parties involved meeting for the first time last week at the CDT offices, Schwartz said. There is commitment to form the coalition, but the group's name has not been formally announced yet, he said. The CDT, a Washington-based public advocacy group, is running the coalition.
Ultimately, according to Fewer, judging whether software is spyware comes down to three components: notice, consent and control. During installation of an application, it should be clear to the user what the tool does. The user should also have to give permission for installation and should be able to remove the application. In many cases, spyware and adware don't meet those basic rules, Fewer said.
The lack of a common approach to defining the unwanted programs has resulted in the anti-spyware tools that flag perceived threats in different ways. Sometimes one anti-spyware tool will identify an application as spyware or adware, while another won't.
"There is much confusion over what spyware is and what it is not. And it starts with the fact that there is no definition," said Tori Case, director of security management at CA.
"What one person calls spyware, another calls adware, another calls surveillance software and yet another says it is not anything. That has led to a lot of confusion," Case said. "If we could all agree, that would allow us to focus our energy on (making) better products and actually protecting against this stuff."
At the same time, makers of software judged to be adware or spyware have protested the flagging of their products by anti-spyware companies, to the point of threatened lawsuits. Microsoft, one of the new coalition's members and an anti-spyware tool provider, last week asked the Senate to rewrite anti-spyware legislation to prevent such lawsuits.
Coalition members include the major anti-spyware makers and several industry groups. Some consumer organisations, including the US Consumers Union, also participate, Schwartz said.
"This effort is really to try and answer questions about what consumers can do to protect themselves," Schwartz said.
The collapse of the Consortium of Anti-Spyware Technology vendors shows the difficulties facing industry efforts to tackle the problem.
If a user has a question about a potential threat, it should be answered in the same way, regardless of which anti-spyware company is involved, he said. "Users should not feel like they get a bureaucratic runaround from different companies," Schwartz said.
Formation of the Anti-Spyware Coalition comes two months after the collapse of the Consortium of Anti-Spyware Technology vendors, or Coast, which had many of the same goals. Coast fell apart after it admitted a company suspected of making adware, prompting the departure of several key anti-spyware members.
Despite similar goals, the coalition is different from Coast, Schwartz said. "Coast seemed to be trying to do too many things and trying to please too many people all at the same time. There seemed to be a lack of clarity as to their mission and who exactly they were serving," he said.
The Anti-Spyware Coalition won't allow members beyond anti-spyware software companies, consumer advocacy groups and distributors of anti-spyware tools such as PC vendors and Internet access providers, Schwartz said. Also, all new members have to be approved by existing members.
The participation of consumer watchdogs is also a key difference, said Richard Stiennon, vice president of threat research at anti-spyware company Webroot.
"At least there is a forum and the industry can't be accused of working blindly. It is extremely good that consumer advocates are part of the consortium because we are aligned with them," he said.
Still, while Webroot is part of the new coalition, Stiennon has doubts about its chances of success, especially in regard to the likelihood of a quick agreement on definitions. "When you get a bunch of technologists together in a room there are very strongly held opinions on definitions," he said.
May 27, 2005
And now it's time for a brief plug ...
We've just recently installed some new web analytics and learned an interesting fact:
Hey! That's great. We're glad to have you, and we're really glad if you find something of value.
If you would like to show your appreciation for us, don't send money! Instead, we would really appreciate if you could link to us from your webpage.
Not sure how? Just insert the following HTML in your page:
If you have an adware or spyware related site that you think others would find useful, and we'll take a look at it. If it's a good resource, we'll add it to our Resources page.
May 24, 2005
New York Attorney General Cracking Down on Spyware
ALBANY, N.Y. (AP) -- The windowless, cluttered 10-by-15-foot storeroom on the third floor of a Manhattan government building seems an unlikely setting for Attorney General Eliot Spitzer's next big thing. But purveyors of spyware and adware and even the major companies that advertise in the surreptitious downloads fear exactly that from the Democrat dubbed the "Sheriff of Wall Street."
"There has been a vacuum of enforcement to date," said Benjamin Edelman, a Harvard University student who specializes in spyware research.
Though Spitzer may get complaints he is attacking legitimate companies, Edelman said, the "fact is, there are lots of surprisingly big companies making serious money from these tactics. So Spitzer's intervention in users' defense is much appreciated and quite helpful."
| Sponsored Link |
|
New York Hotels Visiting New York? Check out our hot deals! |
The problem has become epidemic as people spend more time online and spyware developers get more aggressive.
Some repair shops blame spyware, particularly the subset of ad-delivery programs called adware, for more than half the trouble they're seeing. One study found spyware on the computers of 80 percent of participants.
Although users still get such programs attached to games, screensavers, file-sharing software and other freebies, often without their full knowledge, newer techniques need no user intervention whatsoever and rely on security flaws in Microsoft operating systems and browsers.
The Federal Trade Commission filed a major spyware case last fall. But it is understaffed, said Ari Schwartz of the Center for Democracy and Technology in Washington, D.C.
Enter Spitzer, a candidate for governor in 2006, is best known for his high-profile crusades against conflicts of interest in business but hasn't ignored cyberspace. Last year, his office settled a spam lawsuit against OptInRealBig.com of Colorado as his year-old investigation of a "spam ring" continues.
In pursuing spyware, last week's civil lawsuit against Intermix Media Inc. of Los Angeles is likely just the opening salvo.
Spitzer accused the company of secretly installing software that delivers nuisance pop-up advertisements and can slow and crash personal computers. Spitzer said such programs are fraudulent and threaten to discourage e-commerce.
"Mr. Spitzer has put a match to this and it will be interesting to see just how many volleys take place," said David Moll of Webroot Software Inc., an anti-spyware vendor.
Intermix denies any fraud or use of spyware, saying many of the practices in dispute were established by previous leadership. The company insists it is committed to the Internet's best practices.
Its competitors, meanwhile, insist their programs do not spy and say they welcome uniform rules.
"We strongly support efforts to clean up spyware and rid the Internet of malicious software," said Daniel Todd of 180 Solutions, a major adware company. "As a company that is providing free software and products to consumers, we think that working with technology experts, legal scholars, researchers and anti-spyware companies to establish such standards is a top priority."
Good thing, Spitzer said.
"People are fed up with adware and spyware," he said. "They feel as though they've lost control of their computers and they want something to be done."
Enforcement, however, is difficult.
"Those who engage in these abuses are hard to track down. An operation can be terminated and another literally pops up overnight," Spitzer said. "Hopefully, technology will provide a comprehensive solution at some point but until that time, there needs to be a cop in cyberspace who will stop the most egregious abuses."
Spitzer sees himself as the police.
While Congress and about half the states - including New York - debate legislation to clamp down on spyware, Spitzer is taking business fraud and consumer protection investigation into the 21st century:
His people set up three personal computers up in a storeroom in Spitzer's Manhattan office. For months, investigators visited the freebie-giveaway Web sites likely to carry adware and spyware. Investigator Vanessa Ip regularly analyzed the hard drive to detect any unwanted downloads.
"The most important thing was to try to mimic a typical consumer's experience," Ip said.
Kenneth Dreifach, chief of Spitzer's Internet Bureau, said the office is "limited only by the bounds of creativity and diligence of our investigators - which is limitless."
And don't expect Spitzer to focus only on companies that make and distribute spyware, Dreifach said.
"The companies with which they deal and companies that fund them realize that this is an illegitimate activity from which they want to distance themselves," he said. "No one should infer ... that actual advertisers that drive this activity are immune. They are not."
Companies including Netflix Inc. and Orbitz LLC have acknowledged using adware.
Spyware legislation typically defines it narrowly as surreptitious downloads that monitor a users' activity and could steal personal information.
Spitzer goes further - to include downloads of advertising onto hard drives that may or may not extract personal information.
Spitzer's spyware investigation recalls his successful national crusades against conflicts of interest among Wall Street stock analysts, dealers of mutual funds and insurance companies: A consumer concern is followed by a single lawsuit in an enforcement no man's land.
Negotiation for settlements follow, along with reforms to create new industry standards.
"This should be the next big thing for enforcement efforts because there are some likely targets and, more than with white-collar crime, this will resonate with people," said John C. Coffee, a Columbia Law School securities law expert who has closely followed Spitzer.
Those crusades on traditional American business have been good politically for Spitzer, Coffee said.
Spitzer appears to have prepared for the opportunity. Since Spitzer created the Internet Bureau in December 2000, the staff has doubled to four attorneys, a bureau chief, four investigators and seven college and law school students. The support staff has also doubled.
Even Spitzer's most recent public critic is pleased so far.
Bill Holstein, editor of Chief Executive magazine, has called for Spitzer's resignation, saying his investigations are overzealous and harmful to companies. Yet Holstein sees the spyware battle as "a case where the attorney general and his people are doing exactly what they ought to be doing.
"I agree e-commerce and the Internet are at risk," Holstein added. "It's smart politics, but it's also smart policy.
May 20, 2005
Users Downloading Less Adware
May 18, 2005
By Brian Morrissey
A leading spyware-removal firm reported the amount of adware programs it found on consumer computers dropped in the first quarter.
According to Webroot, a Boulder, Colo.-based maker of spyware-removal software, it found adware on 64 percent of computers it scanned in the first quarter, down from 73 percent in the fourth quarter of 2004. The average computer with adware had 6.9 copies of it, constant with the previous quarter.
The firm attributed the lower adware figures to consumer awareness of advertising software that often comes bundled with free software, such as file-sharing programs. Webroot estimates the adware market generates up to $2 billion annually.
The most prevalent adware program found was CoolWebSearch, which Webroot found on 8.2 percent of computers, the same level as the prior quarter. Webroot tracked a decline in distribution for Claria's GAIN software, which it distributes with the Kazaa file-sharing program. GAIN was on 2.2 percent of scanned computers, compared to 2.6 percent in Q4 2004.
Similarly, Webroot tracked a decline in distribution of 180Solutions' 180search Assistant, which was found on 2 percent of scanned computers compared to 2.6 percent in the previous quarter.
Webroot tabbed CoolWebSearch, which often redirects a user's home page to its search engine, as its "top threat" for Q1 2005. Over the last five quarters, the firm has tracked 17 variations of CoolWebSearch.
May 14, 2005
Can Microsoft Succeed in Security?
Microsoft has now assembled the pieces of a new PC security platform and is launching their first private beta test this month. The product will be an $80/year subscription service that includes anti-spyware, anti-virus, and anti-spam components and is scheduled for release sometime in 2006.
We are anxious to see how this offering stacks up against the established PC security vendors who have been doing this for years (ie: Webroot, McAfee, Norton, Aluria, and so on). In a move that seems calculated to take out an entire industry which has evolved around Microsoft's inability to secure their own software, it seems that the odds are against them.
Here's why. Microsoft is going heads up against a number of small (and by small, we mean perhaps 150 employees) companies which thrive solely on their ability to succeed where Microsoft has failed in the past (security). While these companies are staffed with highly motivated employees with a "startup" mindset, Microsoft is staffed largely with either line-level engineers - many quite brilliant, but with no chance of ever walking away with a million dollar stock option plan, or employees with sizable stock and options who have already checked out (even if they are punching in). While Microsoft is clearly the winner when it comes to providing software engineers with a stable paycheck (not to be discounted these days), they certainly aren't the place to go for techies looking to strike it rich.
The question is then, will an army of semi-motivated Microsoft engineers be able to tame an increasingly hostile internet dominated by hackers, spammers, and PC snoops? And even if they can't, will a super-simple PC security solution, even if it isn't as effective as the tools provided by outside vendors, be so appealing to the mass market that it will eventually make this cottage industry obsolete?
Only time will tell...
May 09, 2005
Webroot Problem Resolved
Webroot has emailed us letting us know that the problem has been resolved. It was apparently a DNS error, not spyware!
May 07, 2005
New Spyware Hijacking Webroot's Site
We've received a number of reports from our readers reporting a new hijacker that is blocking the Webroot website. Any attempt to navigate to Webroot's website lands on a webpage that simply reads "Go Away". Spy Sweeper is unable to detect or clean this hijacker.
We recommend that you run a scan with a backup anti-spyware product, such as Aluria's Spyware Eliminator or Microsoft AntiSpyware.
April 20, 2005
Has Microsoft Partnered With a Known Spyware Company?
Even while Microsoft continues to push forward with their "anti-spyware" effort, new evidence indicates that they have teamed up with known spyware company Hotbar. Are millions of computer users now at risk of infection via Windows Update?
While conducting testing of firewall products this evening, we were greeted an ominous pop-up alert while opening Microsoft Word:
Click to enlarge
For those of you who aren't familiar with Hotbar, they are a notorious spyware company that produces software well-known for the problems it causes in Microsoft Windows. (More information about Hotbar can be found here)
This couldn't be right. We run countless anti-spyware programs on our computers and it is very rare for us to install anything new. And when we do install something new, we're very suspicious of it, probably more suspicious than most internet users. How could Hotbar have ended up on our computer?
We then ran a scan with several anti-spyware tools, including Microsoft's very own AntiSpyware product. None of the top tools found anything.
Next, we went to Hotbar.com, and lo and behold - Hotbar is proudly displaying the "Microsoft Certified Partner" logo on their homepage, confirming that someone at Microsoft has approved some type of partnership between the two companies:
Hotbar's website on April 20, 2005 clearly showing they are now a "Microsoft Certified Partner"
What is even more suspicious is that this happened for the first time today - just two days after Microsoft pushed a mandatory software update to our computer. The alarm bells should really start going off in our heads when we consider the fact that Microsoft's very own anti-spyware program didn't detect Hotbar or prevent it from being installed.
Is it possible that Microsoft is now installing spyware on to millions of PC owners' computers without their knowledge or consent?
Safety fears singe Firefox's first No1
Editors Note: AdwareReport currently receives about 9.9% of its traffic from Firefox - an astonishing number, but not nearly the 50%+ that BoingBoing claims. Regardless of your choice in browser software however, don't expect it to serve as a magic bullet against internet threats.
Firefox, the internet browser that has won a cult following allowing it to chip away at Microsoft's market dominance, received a setback this week as several serious security weaknesses emerged.
News of the security problems will be especially disappointing for the Mozilla Foundation, the non-profit organisation behind the opensource browser, as it coincides with a report from www.boingboing.net which said that the popular blog had received more visitors using Firefox than Microsoft's Internet Explorer (IE) for the first time.
"This is probably the first time in Boing Boing's history, that Internet Explorer is not No1," Boing Boing wrote. "Microsoft, watch out!"
Firefox now claims more than 44 million downloads worldwide and accounts for around 5 per cent of the global market. Analysts believe that many Firefox users have defected from IE and Mozilla claims continuing strong rates of expansion - though the Microsoft product still dominates, claiming nine out of ten internet users.
Though Mozilla admits there is no "magic bullet" to ensure safety online, much of the browsers' popularity stems from its perception as a more secure browser than IE.
Mozilla itself has highlighted advice it claims came from the United States Department of Homeland Security's Computer Emergency Readiness Team "to recommend that consumers stop using Internet Explorer and switch to other browsers".
But a string of warnings posted on Mozilla's own site have prompted a backlash among some fans.
"The versions of Firefox up to version 1.0.3 have had terrible security risks," one user wrote on the Spread Firefox website. "I think these security risks have undermined the promise of Firefox as a more secure browser."
Experts have suggested that Firefox is now attracting as much attention as IE and that similar amounts of "malware" - or malicious software - are being developed for each product.
The security flaws in Firefox were issued with software "patches" by Mozilla to prevent attackers installing dangerous programs on users' computers or from acquiring personal data.
Some of the weaknesses relate to the anti-popup feature found on Firefox. This prevents adverts and other boxes appearing against a user's will. However, when users choose to allow certain pop-ups the program that powers them is allowed to run at a "privileged" level, which malicious hackers could exploit.
Mozilla is encouraging all Firefox users to update their browsers as soon as possible to plug the holes. Updates can be accessed at www.mozilla.org.
April 14, 2005
Fake Microsoft Security Trojan on the Loose!
Moral of the Story: Be very suspicious of any email that asks you to visit a website to update your computer, account information, or anything else...
Paul Roberts, IDG News Service
A new campaign by malicious hackers uses a Web site designed to look like Microsoft's Windows Update page to trick unwitting Internet users into infecting their computers with a Trojan horse remote access program, according to antivirus experts at Sophos.
The scam uses e-mail messages that appear to come from Microsoft to get recipients to visit a Web page that uploads the malicious program. Using the promise of Windows software patches to distribute malicious code isn't new. However, the latest attacks show that scammers are adopting strategies used by phishers to evade detection by gateway and desktop antivirus programs, says Graham Cluley, senior technology consultant at Sophos.
The attack was first detected on Thursday in Sophos's Vancouver, Canada, lab after it was distributed in a spam campaign. The messages have subject lines like "Update your windows machine" or "Urgent Windows Update," Cluley says.
What Happens
A link in the body of the e-mail message appears to take users to the Microsoft Windows Update Web site, but would actually forward them to a Web site operated by the attackers and install a Trojan horse program called DSNX-05, according to Sophos.
The Web site run by the hackers was registered to an Internet service provider in Toronto, but it has since been shut down. The site looked very much like the actual Microsoft Windows Update page and displayed Microsoft's corporate logo. One clue that something was amiss: The URL displayed in the Web browser address bar showed only the IP (Internet Protocol) address of the site, instead of the Windows Update address, Cluley says. Sophos does not know how many Internet users may have fallen for the ruse, he adds.
The method of attack is similar to the phishing identity theft attacks that have become common in the last year. As with many phishing attacks, gateway antivirus software does not detect the scam, because there is no malicious code in the e-mail. Desktop antivirus software with spam detection could spot the e-mail, but only if an antispam definition for the attack had been created and the user had updated the antispam definitions for their product, according to Cluley.
Real Update Coming April 12
Those behind the attack may have been trying to capitalize on anticipation of Microsoft's upcoming software security patch release next Tuesday, Cluley suggests. On Thursday, the Redmond, Washington, company said it intends to put out a number of security patches for its software.
"It's such a shame that, just as we're beginning to teach people more about security updates, cybercriminals are exploiting that," Cluley laments.
Sophos points out that Microsoft does not issue security warnings in the manner used by this attack. E-mail users should be on guard when receiving an unsolicited e-mail that contains an attachment or asks the reader to click a link to a Web page, Cluley says.
Although the Web page used in the latest attack has been disabled, those behind the scam could post the content in a new location and restart the attack, he warns, adding, "It's hard being an average Internet user. You just can't trust anyone."
April 08, 2005
Scam Web Sites Bilk Consumers Twice
Editors Note: Yet another type of online security threat to be aware of!
By Erika Morphy
NewsFactor Network
April 8, 2005 12:32PM
This is a new and more aggressive form of phishing, says Luis Corrons, director of PandaLabs. Previously, online scammers would troll for victims through mass e-mails. In this case, it is actually the buyer, in searching for the best prices online, who goes to the fraudulent Web page.
A new online scam could bilk consumers not only of their credit card information, but also of their savings, warns Panda Software.
A Web site discovered to be operating the scam has been dismantled by authorities. It advertised bargain rate airline fares, and consumers happened upon it by entering relevant terms in search engines, such as Google .
The site included a form asking the user to enter personal details, including credit card number, expiration date and verification value. Once those details were entered, an error page would appear, telling the user that the transaction was unsuccessful, and offering instructions on how to pay for the ticket by postal money order.
Luis Corrons, director of PandaLabs, expects that similar Web sites will be established by fraudsters, perhaps with offerings other than discounted airline tickets.
Different Kind of Fraud
This is a new and more aggressive form of phishing, Corrons says. Previously, online scammers would troll for victims through mass e-mails. In this case, it is actually the buyer, in searching for the best prices online, who goes to the fraudulent Web page. This creates a false sense of security that can lead users to proceed with the transaction.
Indeed, phishers continuously try out new ruses. "Pharming," a recently coined term, is becoming more common, for example. Unlike phishing, which directs users to fake sites through e-mail links, a pharming attack installs a Trojan horse virus on a user's machine. Then, when the user types in the URL of a targeted banking site, the virus reroutes the request to a fraudulent Web site, where personal information can be collected for identity theft.
Recent targets have been the British banks Barclays, Bank of Scotland, Lloyds TSB and NatWest.
Unrelenting Activity
Few believe online financial crimes will diminish anytime soon; it is an easy and non-violent way for criminals to steal money, says Sophos security consultant Graham Cluley. Perpetrators of these frauds grow savvier in their social engineering and technical ruses and are quick to discard a scheme once it becomes known to authorities and move onto the next.
Even hackers that were once bent solely on mischief are aligning themselves with spammers to make a quick buck, Cluley notes.
March 21, 2005
Hackers more active in 2004
Internet attacks on businesses and other organizations increased by about 28 percent in the second half of 2004 compared with the first six months of the year, a report on Internet security warned.
And hackers are setting their sights on the rapidly-emerging mobile-computing market, it added.
On average, businesses and other organizations received 13.6 attacks on their computer systems every day in the second half of 2004.
Thats up from 10.6 attacks in the first half of the year, says the report by Cupertino, Calif.-based Symantec Corp., which makes the popular Norton anti-virus software and other security products.
Theres all sorts of malicious code out there increasing in frequency and severity, said Dean Turner, executive editor of the Symantec Internet Security Threat Report, which was set for release today.
Users have to make themselves aware.
The burst in activity follows a shift in the motivations of attackers. Where the hacker community once sought notoriety, today it is largely a vast network of crooks going after other peoples money, experts say.
The favourite tools of online attackers include phishing, spyware, and adware. Phishing scams involve e-mails appearing to come from legitimate companies that direct people to divulge credit card numbers and other data.
Spyware is hidden software that captures information about a users web-surfing habits. Adware is a type of spyware that collects data to target users with e-mail marketing campaigns or pop-up ads.
Symantec says its anti-spam filters blocked an average of 33 million phishing messages a week in Decemberup from just nine million a week in the first half of the year.
The trend will continue upward this year.
Phishing attacks are difficult to defend against. As the sophistication of spoofed e-mail and Internet sites increases, it will become more difficult for users to determine what is legitimate and what is not, the report said.
Industry estimates of what phishing scams alone cost U.S. companies in 2004 range from $1.2-billion (U.S.) to $2.4-billion.
The recent proliferation of mobile devices is seeding a whole new category of viruses. At the end of December, there were 21 known samples of malicious code for mobile devicesup from just one at the end of last June, the report said.
Turner said those numbers will keep rising as the popularity of mobile computing grows. A short-range wireless connection standard called Blue Tooth is proving to be the conduit for most attacks.
Users may forget to turn off the connection feature as they move around public spaces, leaving themselves open to viruses, he noted.
March 17, 2005
FTC shuts down makers of "Spyware Assassin"
Firm purporting to remove spyware receives temporary shutdown order
Editors Note: First in a long line of bogus spyware company shutdowns? We can only hope so.
THE ASSOCIATED PRESS
SPOKANE, Wash. -- The Federal Trade Commission has temporarily shut down a Spokane company whose software purported to help people remove spyware, but that regulators claim often did nothing to stop the malicious programs.
A U.S. District Court judge in Spokane has approved a temporary restraining order against MaxTheater Inc., which makes Spyware Assassin. In April, the FTC will ask a federal judge to make the ban permanent.
The FTC alleges that Spyware Assassin offered customers a deceptive spyware scan. The FTC said the scan either said it had found spyware that didn't exist or said it would remove spyware and then didn't.
MaxTheater owner Thomas Delanoy, who is named in the complaint, told The Spokesman-Review newspaper he had been advised by his attorney not to comment.
Spyware is a growing online security threat that can be used to track a user's computer habits, steal valuable personal information and slow performance.
March 16, 2005
A letter from Cydoor
I received an interesting letter from Cydoor the other day. They want me to change our definition of Cydoor. I'm not sure what to make of this, so I thought I would post it on the site and leave the comments section open.
I would like to bring your attention to your categorization of our ad-serving technology as spyware. I believe that this categorization is mistaken, and I would like to show you why. I would also like to request that you update your description of Cydoor to be a mild adware.In the past, Cydoors client was defined as Spyware by several members of the press and the anti-spyware industry. The client itself was mostly bundled with free software for the sole purpose of enabling that application to display ads. The client communicated with a Cydoor host periodically in order to present new ad creatives and to report on ad performance. Though no personally-identifying information was ever transferred, this method was considered invasive because users did not explicitly agree to install a Cydoor component or to the transmission of information.
However, today Cydoor has significantly changed its technology to offer end-users and partners an unobtrusive ad-serving solution. With a greater emphasis on visibility and privacy issues, Cydoor provides its partners with a reliable source of revenue, while making sure users are aware of its activities.
How does it work?
Cydoor provides all its publishers with a complete interactive advertising solution, including ad serving, frequency capping, and performance statistics. Cydoor allows each publisher to implement a solution that provides them with the advertising flexibility that they require, including any and all communication to Cydoors servers. Cydoor has no presence on the end-users desktop in any way, and our partners can serve ads and generate revenue from their application or web property.
Users download the desired application, while noting that it is ad-supported. Cydoor strongly urges all its partners to state upfront that their application is freeware but is supported by advertising revenue, and most state it in their End User License Agreement (EULA). There is no installation, explicit or otherwise, of any Cydoor component on the users computer.
After installation, the partner application manages the various advertisements and their performance. The ads are served according to predefined impression requirements and caps and exposure is not based on any aspect of the users behavior. From time to time the partner application connects to Cydoor's servers in order to report aggregated performance records such as which ads were displayed, how many impressions they received, and which, if any, did the user click on. These are the same kind of performance parameters that are tracked by any online advertiser, including banners published on a web site.
Id like to emphasize that the application does not download ANY information from the Cydoor servers aside from ad creative. The application reports only basic aggregated campaign performance parameters. Under no circumstance does the application report on any other user behavior or does it transmit any personally identifiable content.
Id like you to note that as an example, two of our partners, Download Accelerator and PalTalk Instant Messenger are either certified as Spyware-Free or are working with the leading Anti-Spyware vendors to be removed from their Spyware list.
Please let me know if you need any additional information regarding my request.
March 15, 2005
Spyware Removal Starts At Home
Consumers, Microsoft and the Federal Trade Commission are similarly confounded when it comes to defining spyware and how best to combat a spreading plague of intruding and often malicious software. Its up to individual users to stop it on their own computers, at the first sign of infection.
Ask a personal computer user suffering from a spyware or adware infection and theyll easily define it for you. Slower Internet connection speeds, unwanted popup ads, changed Web browser settings or home pages, computer unresponsiveness and a general anxiety about exposing personal information and passwords.
"Adware and spyware victims need to take immediate action at the first sign of a spyware symptom," advises Richard Stokes, a computer engineer who runs AdwareReport.com, an established adware removal, consumer review site. "Dont wait for the government or for Microsoft to find an adware solution, because every moment you wait is another moment that you risk your privacy and general frustration with your computer.
"Having said that," Stokes added, "even when consumers do decide to find a spyware solution on their own, theyre often confused about which anti-spyware program will do the trick." Hundreds of anti-spyware programs elbow for search engine space, as consumers get bombarded with anti-spyware ads and promising spyware cures.
"As with anything consumers buy, the smart shopper will always come out ahead," said Stokes. Nobody wants to waste their time researching for the right spyware remover, but wasting your money purchasing a useless spyware remover can be twice as frustrating. "When people visit Adware Report, I encourage them to take their time, read the reviews and be certain that the spyware remover they buy is the right fit for them." Consumers need to make their own, knowledgeable decisions or their spyware problems are sure to persist.
Although the FTC and similar government agencies are finally making strides towards first defining and then solving the growing spyware epidemic, the burden ultimately falls on the individual spyware victims to take swift and intelligent action at the slightest hint of a spyware infection. It could take years before consumers see the benefits of the FTCs recent spyware and adware report (available at AdwareReport.com). Until then, the only viable solution is to continue turning to review sites like Adware Report to ease their confusion and help find anti-spyware solutions.
March 13, 2005
Federal Trade Commission releases 62 page report on Spyware
The FTC has released a very interesting report about their findings on spyware. The report is a bit lengthy at 62 pages, but I plan on reading this and distilling the most interesting points here on the site.
I immediately noticed this quote from the report relating to the difference between adware and spyware. It appears that even industry experts can't seem to agree on how adware and spyware differ:
Workshop panelists and commenters stated a range of views as to whether and when adware should be classi?ed as spyware. Some panelists argued that adware is spyware if users have not received clear notice about what the software will do or have not provided adequate consent to its installation or operation. In turn, some types of adware would not meet some de?nitions of spyware because they do not monitor computer use. Other workshop participants apparently would view adware as spyware if it causes consumers to receive pop-up ads, regardless of whether consumers are bombarded with such ads or just occasionally receive such ads.
If the industry can't seem to agree on even what spyware is, how can we expect the FTC or other governmental bodies to effectively legislate on this issue?
Read the entire report here (1.1Mb)
Afterthought: We've seen this same type of confusion recently when Lavasoft, Computer Associates, and Aluria decided to de-list WhenU as "spyware". Many industry experts, some of them rather thoughtlessly, expressed outrage at the de-listing, continuing to label WhenU as spyware, when they should actually be considered adware.
Are you experiencing display problems with our site?
Two readers wrote in today telling us that the left-hand navigation menu is overlapping the main copy. We've tested this in a couple of different browsers, but couldn't find a problem. So if you're having an issue, please drop us an email at and let us know what browser and version # you're using.
Thanks!
March 11, 2005
Symantec anti-virus flaw hits 30 products
A cross-platform flaw affecting many Symantec security products - both consumer and enterprise - has been discovered. Users of Symantec's Norton SystemWorks 2004, Norton SystemWorks 2004 (both Mac and Windows), Norton AntiVirus 2004, corporate anti-virus apps and Brightmail anti-spam software (among others) all need to apply patches following the discovery of the "highly critical" security bug. In all 30 packages are affected.
March 10, 2005
Broken Layered Service Providers (or, "my laptop is getting slower and slower and slower...")
I run one of the largest anti-spyware sites on the net and have every imaginable tool running on each one of my computers. I regularly audit my work laptop to ensure new strains of spyware aren't running in the background. I use Aluria Spyware Eliminator, Webroot Spy Sweeper, and Microsoft Antispyware. I run ZoneAlarm firewall, and F-Prot anti-virus.
And despite all of this, something ... somehow ... has managed to make my laptop grind to a halt while trying to surf the internet. Sometimes, the browser even freezes completely, and I have to open up a new window to finish what I was doing.
After hours of frustration, I have found the culprit: Broken LSPs (Layered Service Providers). These little snippets of code intercept all internet communication, sometimes for benevolent reasons, othertimes as a means of spying on your surfing habits. In my case, it turns out it wasn't spyware that was causing the problem. It was Google's Desktop Search program. I love this tool, but I have noticed that it slows down my computer, sometimes to unacceptable levels.
So I popped open Microsoft's AntiSpyware tool, which I use as a backup program to my preferred products. The reason I like this tool is not so much because of its effectiveness (it's better than average, but not great), and certainly not because of its usability (it's one of the more annoying programs I use), but because of its "advanced tools". In the "Advanced Tools -> System Explorers -> Winsock LSPs" section, I found the following:
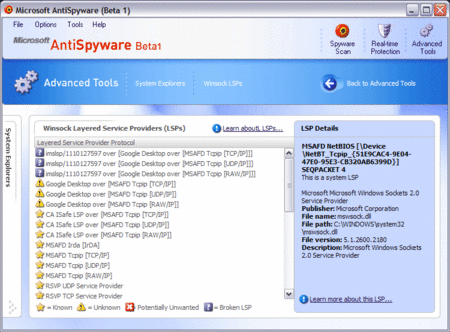
Great! A likely culprit. Those question mark icons at the top indicate that the Google Desktop search has somehow inserted some broken LSPs into the communication pipeline between my laptop and the internet. But now how to fix it?
Fortunately, the generous souls at Cexx have written a tool, aptly named "LSPFix", to fix the problem. I downloaded this program, ran it, and problem solved! My laptop is running fast as the blazes again!
My next question is why aren't the anti-spyware vendors including something like this in their products?
Important: if you don't know what you're doing, leave the "advanced" checkbox off, or you could cut yourself off from the internet.
March 01, 2005
Firewalls: What They Are and Why You Need One
So you've heard about spyware and all the problems it can cause with your computer, and you're now doing something about it. That's a good start, but did you know that you're still exposed to hackers, trojans, and viruses that can steal your financial information, hijack your email, or even destroy your computer altogether?
Anti-spyware tools block only a few types of common PC invaders, such as spyware, adware, dialers, search hijackers, and so on. For complete security, you also need a firewall (you also need an anti-virus program, but that's the subject of another article).
You should be using a firewall product if...
You regularly use wireless networks other than your own (ie: at a Starbucks or an airport)
You are at risk of having someone spy on you (paranoid employer, ex-spouse)
You have valuable or irreplaceable data on your computer (spreadsheets, legal documents, email, personal writing, etc)
You want an extra layer of defense against spyware, Trojans, and viruses.
What Do Firewalls Do?
There are a variety of ways in which an attacker can detect and get into your computer. Spyware companies make use of some of these methods ("drive-by installs"), but they aren't the only ones trying to take advantage of you. Spammers have written programs that will hijack your computer and use it to send junk email. Trojans and worms are often spread via email, instant messenger, or other means. Jealous spouses or paranoid employers can even purchase off-the-shelf software to spy on your every online move. Anti-spyware tools don't do anything to prevent any of these kinds of invasions.
This is where the firewall comes in. It plugs the security holes that anti-spyware tools don't, preventing outside attackers from gaining access to your system in the first place. And if a malicious payload does somehow manage to get on your PC, the firewall will prevent it from communicating with the outside world, rendering it useless.
In short, a firewall stops any and all data transfer between your computer and the internet except for that which you specifically approve.
Sadly, only 10% of computer users have any type of firewall installed on their computer.
Doesn't Windows come with a firewall?
Windows XP SP2 does come with a personal firewall but it provides only a bare minimum level of protection (Windows 2000 users and earlier, you're completely unprotected and you need to get some type of firewall installed ASAP). The firewall that comes with your operating system blocks in-bound attacks only, but leaves you completely exposed to threats that originate on your computer. For instance, if an ex-spouse installs spy software on your computer, Windows personal firewall is completely useless.
This quote from David Berlind at CNet UK explains it nicely:
"Once a malicious payload gets in, your reliance to stop it shifts from the inbound firewall to something internal to your network or workstation -- like your antivirus or anti-spyware software. But, in the cat-and-mouse game of security solution developers vs. hackers, there are some pretty clever mice. And, as was demonstrated by at least one recent exploit of a vulnerability in Internet Explorer, there are certain exploits that anti-anything (virus, spyware, pop-ups, etc) products are powerless against. What's your last line of defence to keep one of these exploits from phoning home? Outbound blocking -- a feature that the Windows Firewall lacks."
If you think you're safe because you've downloaded the latest Windows update, think again. Hackers are faster than Microsoft, the maker of the world's most insecure software products, will ever be.
So How Do You Remain Protected?
You should seriously consider purchasing a commercial firewall product. A good product will provide the following:
* Make your computer invisible to hackers by default
* Allow you to share files and printers with people you trust
* Ensures only applications you trust can access the internet
* Prevents malicious programs from disabling the firewall
* Automatically locks down your PC if the firewall is compromised
Windows firewall does none of these things and unfortunately has given a lot of people a false sense of security.
What Firewall Programs Are Out There?
We've tried a few and have settled on ZoneAlarm. This is the firewall we run on all of our personal and company computers. ZoneAlarm is the market leader and sells the most effective firewall software available.
| Download ZoneAlarm Pro Here |
February 28, 2005
March Reviews Are Ready!
The latest round of anti-spyware tests have been completed! We added more new spyware to our testing computers, which makes for a very difficult test. It takes nearly 10 minutes to boot up our infected image, and downloading anti-spyware programs on each takes a long time because the spyware programs running in the background hog all of the bandwidth.
No big surprises in the rankings. Spyware Doctor moved up a notch, while Microsoft AntiSpyware made its debut at #4. We were a little amazed that StopZilla performed so poorly in our tests. Their site looks terrific and they have great marketing, so we expected more. It just proves you can't believe the hype.
Finally, if you have a product that you would like us to review, . We can't personally answer all of the email we receive (there's just way too much!), but we do read each and every one.
February 22, 2005
Yet More Misleading Marketing...
An otherwise excellent article at Insecure.Org which discusses the withdrawal of Webroot from COAST (Consortium of Anti-Spyware Technology Vendors), makes mention of a "survey" Castlecops' conducted which was presumably conducted to capture public opinion about the Aluria-WhenU debate.
If you haven't been following along, we've been somewhat critical of Castlecops and other spyware commentators for their alarmist stance that they've taken regarding Aluria's decision to de-list WhenU as a spyware company. Our view has been all along that if any company chooses to go legit, then the anti-spyware community should embrace them with open arms. Castlecops (and others) disagreed and remained critical of Aluria. Since then, we've seen Lavasoft and PestPatrol follow in Aluria's footsteps. We consider ourselves vindicated.
Are our criticisms of Castlecops unwarranted? Their hearts are in the right place, but our complaints stand. The above article irresponsibly mentions this sham of a survey conducted by Castlecops which had but a single question:
Do you trust Aluria's Spyware Eliminator after the WhenU Deal?
Yes - 14.00% (240 votes)
No - 86.00% (1474 votes)
Should you take the above survey at face value, you would be inclined to think that most people think rather poorly of Aluria (and now Lavasoft and PestPatrol) due to the de-listing. However, the above survey suffers from two errors which are well known to most marketers:
1. Leading Question - the above question leads respondents into clicking 'No' because of the way it is worded.
Example: "Do you trust John after he donated all that money to the orphans?" ... no, of course I don't! (I don't know why, but it's obvious I shouldn't. That lousy John.)
2. Sampling Error - the above survey was conducted on Castlecops, a site visited largely by tech-savvy security professionals. These are hardly mainstream computer users and no survey data collected on Castlecops should be used as an indicator of how ordinary people might feel about an issue.
To prove this point, we took a survey of our own to get a more accurate picture of how people really feel about this. We asked visitors to this site two questions:
1. Are you familiar with the fact that Aluria has delisted WhenU as a spyware company?
2. If the answer for the above question was yes, then do you trust Aluria's Spyware Eliminator after the WhenU Deal?
Note that we left the wording on the leading question the same in order to isolate the effect of the sampling error. Our readers tend to be very mainstream computer users (they self-report only an average level of knowledge about spyware) between the ages of 35 and 50.
Our results
Overall, 46.6% of our readers stated that they didn't trust Aluria. The other 53.4% stated that they did (in other words, the delisting of WhenU was not seen as a breach of trust).
We then divided up the survey respondents by those who had some familiarity with the WhenU delisting vs. those who hadn't. Only 19.4% of our readers knew about WhenU delisting. A full 80.6% had never heard of it.
Of those who had heard of the delisting, a whopping 72.7% stated that they still trusted Aluria. 27.3% said that they no longer trusted Aluria.
Of those who had not heard of the delisting, only 41.7% said they did still trusted Aluria, while 58.3% stated they no longer trusted them.
What did we learn from this?
First, the Castlecops survey was not an accurate reflection of how mainstream computer users truly feel about the WhenU delisting. Their survey result reflected a far more paranoid population of security professionals.
Second, most people who had heard of the delisting (and presumably had formed their own opinion about it) felt that it was not something that breached their trust in the company. On the other hand, those who had no prior knowledge of it indicated that they no longer trusted Aluria. This is what we would expect to see from a leading question such as the one in the Castlecops survey.
So are the mainstream users right or are the security professionals? One could argue that the security professionals, by virtue of their expertise, have a more informed opinion and thus should be listened to. We agree with that, and so we sliced our data one last time. Among the respondents to our surveys who claimed to have "above average" to "expert" knowledge about spyware, 58.3% still trusted Aluria.
February 20, 2005
Microsoft's security strategy is still lacking despite new IE, Gartner says
Call us skeptical, but Microsoft has had security as it's "#1 priority" for over two years ago and if anything, Windows has become even less secure. Case in point: entire software industries (anti-spyware, anti-virus, firewall) have come about to address Microsoft's gaping security holes. Past experience has proven that independent companies do a much better job than Microsoft at sealing the cracks in their own software.
Saturday February 19, 2005 (05:06 PM GMT)
Bill Gates put Microsoft's security strategy front and center this week, announcing a new version of Internet Explorer, free antispyware and an antivirus service, but his vision does not look far enough ahead, a Gartner analyst said.
Neil MacDonald, a research director at Gartner, said Microsoft's security announcements were a missed opportunity.
At the RSA Conference in San Francisco, Gates said Microsoft will release IE 7.0, which continues the hardening of IE 6 with XP Service Pack (SP) 2, in beta in mid-2005. IE 7.0 will not be available for Windows 2000 users.
February 11, 2005
Microsoft Probes Spyware System Attack
More entertainment in the spyware industry: Microsoft now recommends you purchase an anti-virus program to fix the security holes in their own security products.
REDMOND, Wash. Feb 10, 2005 Microsoft Corp. is investigating a malicious program that attempts to turn off the company's newly released anti-spyware software for Windows computers.
Stephen Toulouse, a Microsoft security program manager, said the program, known as "Bankash-A Trojan," could attempt to disable or delete the spyware removal tool and suppress warning messages. It also may try to steal online banking passwords or other personal information by tracking a user's keystrokes.
To be attacked, Toulouse said a user would have to be fooled into opening an e-mail attachment that would then start the malicious program. He said the company had not seen any evidence so far that the program is widespread.
Toulouse said Redmond-based Microsoft was recommending that users who believe they might be infected use antivirus software, such as products made by Symantec Corp. or McAfee Inc., to try to remove it.
From ABCNews
February 09, 2005
Breaking News: Trojan attacks Microsoft's anti-spyware
Virus writers have created a malicious program that can disable Microsoft's new anti-spyware application, security experts warned on Wednesday.
AdwareReport Comment: Microsoft has made themselves a lot of enemies over the years and despite their latest attempt to resolve their nagging security problems through the purchase of Giant AntiSpyware, all they have succeeded at doing is making themselves a bigger target. One of the biggest problems that spyware programmers face in trying to defeat anti-spyware tools are the wide variety of tools available out there. Microsoft has inadvertently shot itself in the foot by trying to mass-market one.
By Dan Ilett ZDNet (UK) February 9, 2005, 9:54 AM PT
Antivirus experts, who are calling the Trojan "Bankash-A," say it is the first piece of malicious software to attack Windows AntiSpyware, which is still in beta.
"This appears to be the first attempt yet by any piece of malware to disable Microsoft AntiSpyware," Graham Cluley, a senior technology consultant at Sophos, said in a statement. "As Microsoft's product creeps out of beta and is adopted more by the home user market, we can expect to see more attempts by Trojan horses, viruses and worms to undermine its effectiveness."
Windows AntiSpyware, built using technology from Microsoft's acquisition of Giant Company Software, is designed to protect Windows PCs from spyware--software that is installed on computers without their owners' knowledge. Typically, spyware generates pop-up ads or keeps track of people's Web surfing.
Like many other Trojans, Bankash attempts to steal passwords and online banking details from Windows users, Sophos said in an advisory. The program targets users of U.K. online banks such as Barclays, Cahoot, Halifax, HSBC, Lloyds TSB, Nationwide, NatWest and Smile.
Sophos called the Trojan "Bankash" because it attacks banking customers and installs a file called ASH.DLL onto a victim's hard drive.
Microsoft's British press office was awaiting comment from the company's U.S. headquarters at the time of writing.
Dan Ilett of ZDNet UK reported from London.
February 08, 2005
New version of Aluria Spyware Eliminator Released
Last Friday, Aluria released version 4.0 of their product. We finally got a chance to install and review it, and it rocks! There are a lot of improvements in the product, but two stand out the most:
1. A new user interface
Let's face it, Aluria's old user interface was a bit lacking and unappealing for many of us. I often mentioned this to them, and apparently a lot of of other users did as well. The new release sports a brand new interface that is downright good looking.
2. New Spyware Detection Technology
We ran the new version on our heavily polluted test PC and the results were off the charts. So much so, that we're going to re-image a brand new machine, manually re-infect it, and test it again. We talked to Aluria about this and the new version makes use of similar technology that Giant Company created for their AntiSpyware product (and which is no longer commercially available). Apparently this method for detecting spyware does not need signature files. For those of you who don't know, signature files are used to match specific spyware programs and must be created manually. This is the reason that different spyware programs will give you such different results, and why the same spyware program that seems so effective one month might be outdated a month later. If these signature files aren't kept up to date, the software becomes virtually useless.
The challenge for anti-spyware companies then has been to keep these signature files as up-to-date and accurate as possible. However, if you can devise a technology that doesn't require them, then in theory, you may have discovered the magic bullet that can kill all (or potentially all) spyware. Has Aluria done this? We'll see in the next few months.
February 02, 2005
anti spyware recommendation
We saw this letter on CNet today and thought we would share it. Although we get the occasional support complaint about just about every company we review (some more than others), Aluria's customer support has stood apart from the crowd.
This is not an advertisement, but a recommendation based on personal experience. I recently had a spyware infection on my computer that was hijacking my browser home page and giving me unwanted popups. Neither free Spybot or Adaware could detect or remove the spyware.
So I purchased Spyware Eliminator by Aluria Software and it didn't detect the spyware either. But Aluria has a toll-free spyware hotline, which I called. The tech support rep was unbelievably helpful and he walked me through the process of identifying and removing the spyware.
No spyware removal program is 100% accurate, especially with new threats. I simply do not have the time to write lengthy descriptions of a problem to be posted on a forum, and then wait for a reply that may or may not solve my problem. I use my computer for my business and can not tolerate any infection which could compromise the security of my system.
In my opinion, Aluria's software is no better or worse than the rest of the pack, but their toll-free support sets them apart from the crowd. Their call center is located in Orlando, Florida, and I was transfered to a real live person with practically no wait. Your mileage may vary.
January 11, 2005
Hackers Use DRM To Plant Massive Amounts Of Spyware
Hackers are turning digital rights management features of Microsoft's Windows Media Player against users by fooling them into downloading massive amounts of spyware, adware, and viruses.
Hackers are turning digital rights management features of Microsoft's Windows Media Player against users by fooling them into downloading massive amounts of spyware, adware, and viruses, security firms said Tuesday.
According to anti-virus vendor Panda Software, two new Trojan horses -- dubbed WmvDownloader.a and WmvDownloader.b -- have been planted in video files seeded to peer-to-peer file-sharing networks like eMule and KaZaA. The Trojans take advantage of the new anti-piracy features in Windows Media Player 10 and Windows XP SP2 to trick users, said Panda.
When a user tries to play a protected Windows media file, the anti-piracy technology demands a valid license; if that license is not stored locally, the player looks for it on the Internet so the user can download or purchase it.
However, these Trojans only "pretend to download the corresponding license from certain Web pages," said Panda in its online alert. "What they actually do is redirect the user to other Internet addresses from which they download a large number of adware, spyware, dialers, and other viruses."
Others, including Kaspersky Labs and Ben Edelman, a Harvard student and spyware researcher, have confirmed the effects of the two Trojans.
Edelman's test of one of the Trojans on a clean PC demonstrated its impact.
"I pressed 'Yes' once to allow the installation. My computer quickly became contaminated with the most spyware programs I have ever received in a single sitting...all told, the infection added 58 folders, 786 files, and an incredible 11,915 registry entries to my computer."
From Information Week
January 08, 2005
Bad guys love to prey on gift PC purchases
Got a new PC? It's important that you get antispyware and antivirus software installed as soon as possible.
RACHEL KONRAD
The Associated Press
SAN JOSE, Calif. - Susan Love's problems began with a smile.
The New York City fund-raiser clicked on a happy-face attachment in a friend's e-mail last year. The virus crashed her computer within an hour.
Love, 57, salvaged the data. But within a few months, her computer's performance slowed to a crawl. In December 2003, she upgraded to a Sony Vaio with an extra-large monitor and Microsoft Windows XP operating system.
Within a few days, "spyware" - programs that sneak onto computers uninvited - began sponging up valuable memory. Then her e-mail stopped arriving.
Instead of crafting holiday e-mails, she spent hours installing the latest antivirus, antiadvertising and antispyware software.
She also instituted a rule: Her computer never gets turned off, so security programs patch vulnerabilities around the clock.
"You have to become something of a nerd to make sure your computer is safe," said Love, a former English teacher who recently installed anti-adware on her daughter's computer. "If you don't sweep the computer every night, you could (get) hit."
Love won't be the last to get a holiday crash course in computer security.
Hackers, spammers and spies go into overdrive in December and January, when unsuspecting neophytes unwrap new computers, connect to the Internet, and, too often, get hit with viruses, spyware and other nefarious programs.
"People want to get on the Net right away, just like they want to put together and start using any Christmas present," said Tony Redmond, chief technology officer of Palo Alto, Calif.-based computer giant Hewlett-Packard Co. "They should be warned that the Net is a very, very dangerous place."
Hewlett-Packard's new PCs ship with 60 days of virus and adware protection.
Although few researchers produce holiday-specific security data, experts at IBM Corp., Dell Inc., Hewlett-Packard, software companies and Internet service providers agree that the holidays are prime time for hackers.
Holiday viruses are so rampant that consumers could be attacked even if their first online destination is to a Web site for updating security patches.
Kris Murphy, help desk coordinator for North Carolina Internet service provider Indylink.org, said his minister got attacked last year a few minutes after unpacking and connecting the machine.
At the time of infection, the minister was updating security patches to Windows.
"Hackers know that you are most vulnerable as soon as you go online for the first time," said Murphy, whose 10-person company hires temporary consultants during the holidays to handle higher call volume. "Inexperienced people tend to fall into traps more readily because they don't recognize that this guy might be trying to get your credit card information."
Technology executives describe the relationship between hackers and security programmers as an arms race. Both sides keep ratcheting up fire power.
But lack of consumer awareness, if not downright naivete, allows the war to escalate.
According to a recent survey by the National Cyber Security Alliance, of the 185 million Americans with home computers, 1 in 3 says he'll never get hit by viruses or other cyberattacks.
In a Consumer Reports magazine study, 36 percent of U.S. home computers showed signs of being infected with spyware, and 41 percent of surveyed households said they actively tried to prevent it.
American businesses are savvy about firewalls, spam filters, multiple passwords and other network protections, says Stuart McIrvine, director of corporate security strategy at IBM.
But problems at the consumer level, from spyware to security risks in coffee shop wireless networks, are so severe that every hardware and software vendor should be worried about a backlash.
Seasonal attacks start around Thanksgiving, when online shopping begins an annual spike and marketers pummel consumers with junk e-mail, from the perfect stocking stuffer for a balding spouse to a limited-offer holiday cruise.
"W32/Zafi-D," a mass mailing and peer-to-peer worm, harvests addresses from Windows address books and other files.
Infected e-mails' subject line begins, "Merry Christmas!" and the text reads, "Happy Hollydays."
Tony Ross, analyst at British security firm Sophos Plc., advises consumers to get a CD-ROM with the newest updates from their electronics vendor, next-door neighbor or the computer at their office before connecting to the Internet.
December 29, 2004
Firefox - a cure for spyware?
Is Mozilla's new web browser, Firefox, a cure against spyware?
We looked a little deeper and found that the answer is a definite 'no', despite some claims found on the internet.
A look at our logs indicates that Firefox is now the second most popular browser used to visit our site. While this is a distant second to Microsoft's Internet Explorer (6% using Firefox as compared to 89% using IE), Firefox still has a huge user base. And while most anti-spyware products actively protect against known backdoors in IE, few (if any?) do the same for Firefox. So for now, there are substantial opportunities for spyware companies willing to invest in a little R&D.
So our suspicion was that perhaps a few spyware companies, enterprising little devils that they are, are already targeting Firefox. And it appears we were right.
Although Mozilla claims that Firefox is immune to spyware because it doesn't load ActiveX controls (and other reasons), this doesn't appear to be a cure-all. Among the symptoms we found Firefox users suffering from:
* Adding new shortcuts (Shopping, Travel, etc)
* Removing all bookmarks
* Disabling themes
Furthermore, using Firefox won't help you in any way if you already have spyware running on your computer. This is because many spyware programs will automatically upgrade themselves and load even more spyware in the background, without having to go through your browser at all.
Conclusion
Firefox is an excellent browser and is (currently) less susceptible to spyware than Microsoft IE, it won't give you 100% immunization, and in fact, may become even more susceptible to spyware in the future because few anti-spyware companies are offering protection for Firefox users.
December 16, 2004
Microsoft Acquires Giant Company
Source: Giant Company
Microsoft Acquires Anti-spyware Leader
Giant Company Software Inc.
New offerings will help customers keep spyware and other deceptive software off of their computers.
On December 16, 2004, Microsoft announced its acquisition of GIANT Company Software, Inc., a provider of top-rated anti-spyware and Internet security products. Microsoft will use the acquisition to provide its customers with new tools to help protect them from the threat of spyware and other deceptive software. In addition, key personnel from Giant will be joining Microsofts security efforts.
Microsoft plans to make available a beta version of a spyware protection, detection, and removal tool, based on the Giant AntiSpyware product, within one month for Microsoft customers. The upcoming beta will scan a customers PC to locate spyware and other deceptive software threats and enable customers to remove them. The tool will be configurable to block known spyware and other unwanted software from being installed on the computer. It will be available for Windows 2000 and later.
Details of the Microsoft solution beyond the planned beta, including product plans, pricing, and a timeline for delivery, are not yet available. The anti-spyware technology will complement the enhanced security features available in Windows XP Service Pack 2 to provide a higher level of protection for browsing and other Internet computing.
More information about Microsoft and its efforts to address computer security, including spyware customer guidance and information on anti-spyware solutions is available at http://www.microsoft.com/spyware.
Limited functionality for the Spynet Research Center will be available during this transition. Spynet can be reached at http://www.spynet.com
December 15, 2004
iPod Drawing Winner
Congratulations to Chris Bloom, who won a free iPod!
Thanks to everyone who entered!
December 10, 2004
Aluria releases v3.3 - Remember to Upgrade!
Aluria Software released a major upgrade of their software today (v3.3). In addition to over 2800 new spyware definitions (bringing the total of to 23608), it also includes something called the "Spyware Retrieval Service". This opt-in feature allows the product to send suspicious looking files back to Aluria's research lab for closer examination.
This version also supposedly includes a module specifically designed to attack "About:Blank". If you are infected with About:Blank and can give the software a try, send us an and let us know how it works.
December 08, 2004
Win a Free iPod Mini!
Have you seen these yet? Apple's iPod Mini holds over 1,000 songs ... you could bring enough music for a three-day weekend getaway, and it all fits in your pocket!
Not bad for $249, but it gets better: we like these so much that we're going to give one away this week! Just email us the name of the product you purchased and your order # and you're entered to win. We'll announce the winner next Monday, December 13th.

December 04, 2004
Happy Holidays From Adware Report!
| This weekend, when you purchase any anti-spyware product, Adware Report will send you a free copy of Aluria Softwares The Everlasting Pop-Up Stopper. This $30 software package is yours, no strings attached, as our way of saying thank you for visiting our site. |
Whats a Pop-Up Stopper?
While anti-spyware products eliminate unwanted software which slows down your computer, they dont block annoying pop-up and pop-under windows that interfere with your web surfing experience. Thats where pop-up stopping software comes in. With it, youll stop annoying pop-up ads forever. And if you surf the internet through a dialup connection, youll be amazed at how much faster you can surf the web.
How To Get Your Free Software
After you purchase your software through one of the links on our side-by-side comparison or review pages, simply email your receipt (or order number and the name of the product you purchased) to us at: [email protected]. Well send you download instructions and your registration code by email. We have a limited number of free copies to give away, so be sure to email us your receipt as soon as you receive it.
December 03, 2004
Digital Camera Giveaway
From now until December 31st, anyone who purchases a copy of Aluria's Spyware Eliminator will be entered into a drawing to win a free Canon S410 Digital ELPH Camera. Please note that this giveaway is being run by Aluria, so there's no need to send us your email receipt or order number! You will be automatically entered.

December 02, 2004
Anti-Spyware Tools All the Rage
By Sean Michael Kerner
The market for anti-spyware tools will hit $305 million by 2008, according to new research from IDC. The firm also revealed that it estimates 67 percent of consumer PCs are infected with some form of spyware.
In 2003, IDC reported the market for anti-spyware tools to be only $12 million. That number is forecast to grow by 260 percent in 2004.
IDC cites the ease with which spyware infiltrates user PCs among the reasons for the growth of spyware and the tools that fight it. Spyware, also known as adware or malware, is often bundled with downloadable applications and it can also "infect" PCs just by simply browsing.
"Today, more malicious spyware can easily infiltrate corporate firewalls," said Brian Burke, research manager of Security Products at IDC, in a statement. "These programs make their way into the corporate intranet under the guise of less-threatening network traffic and, once in, they can wreak havoc."
Spyware is not always malicious. Some of the most common occurrences of spyware are of the adware nature that are planted by advertisers to track when users see an ad or visit a site and when they return.
Malicious uses of spyware include browser hijacks that redirect users and forms that allow for key logging, PC scanning and data corruption. IDC warns that at its worst spyware can lead to theft of company trade secrets and identity theft.
"The range of spyware from semi-legitimate to completely criminal is a challenge to consumers and corporate customers," Chris Christiansen, program vice president of IDC's Security Products and Services programs, said in a statement.
IDC said that anti-spyware features are soon to become key components of server-based gateways, security suites and anti-virus products.
The scourge that is spyware was identified in a recent IDC survey as the fourth greatest threat to enterprise security. Other surveys have also shown similar or greater infestations of spyware. A recent AOL/National Cyber Security Alliance (NCSA) Online Safety Study, found that 80 percent of scanned computers actually had some form of spyware or adware present.
The U.S. government hasn't been idle in the fight against spyware, either. In October Congress passed a slew of anti-spyware laws designed to deter and penalize spyware offenders.
Original URL: http://www.internetnews.com/security/article.php/3442551
December 01, 2004
More on Spyware Smear
In a previous article, Spyware Smear Campaigns, we discussed how we uncovered an article at SpywareGuide claiming that Aluria Software was compromising the privacy of their customers by selling their contact information to third parties. We discovered that this article was not only written by the CEO of a rival software company, but was, shall we say, just a bit misleading as it totally misquoted Alurias privacy policy.
Well we have new developments to talk about!
But first, lets state explicitly that there is a difference between reporting about this and being a participant. Some readers have written in trying to engage us in a debate about this. To this we responded more or less, please feel free to debate it with Aluria, well be happy to just watch. That said, lets continue on with this story.
CastleCops has found out that the privacy policy quoted in the article did indeed exist at one time (February, 2004 was when it was pulled down). Based on this, they write:
Adware Report has it wrong, and Spyware Guide was correct. The link above thanks to Web Archive clearly shows in the first paragraph of Aluria's Privacy Policy, that the statement did in fact exist. Compare the Web Archive to the statements made at Adware Report and the Google Cache of Spyware Guide. With this evidence that our anonymous reader presents, Spyware Guide has every right to bring back their now defunct articles.Note: Updated with new evidence, showing SpywareGuide was correct about Aluria.
And there the article concludes, smugly and not-so-subtly suggesting that Adware Report owes everyone a big fat apology.
Not so fast, fellas.
There are a few problems with this conclusion that are sadly, the signature of the anti-spyware jihadists who lurk in various warrior forums and other places round the net. Not that we disagree with their sincerity and enthusiasm mind you (because we hate spyware, too) but rather when youre looking for a conspiracy, everything looks like a conspiracy. The problem is sometimes theres just no conspiracy there. And from the discussions we've had with everyone about this, thats the case with Aluria.
For starters, the article was a smear job, plain and simple. It stretched the interpretation of Alurias privacy policy to the absolute limit in an effort to paint them as being some kind of evil company that will sell your credit card number, social security number, and anything else you give them to whomever they want.
It was about the most superficial, one-sided argument one could make.
It completely ignores the fact that this doesnt make the slightest bit of sense for a privacy company because it would cause irreparable damage to their reputation. It ignores the fact that Aluria has never sent out a marketing email to its customers. It ignores the fact that Aluria forbids all of its affiliates from making use of email marketing. And most of all, it ignores the fact that 99% of most privacy policies on the internet are created as cut-and-paste jobs by harried marketers who didnt really take the time to think about what they were putting up there, and not by lawyers who understand the implications that these privacy policies can have.
In short, Wayne Porters article in so many words claimed that because Aluria legally could, that they would. All reasonable explanations be damned. Coming from an anonymous netizen with no connection to the spyware industry, it could be overlooked as someone being a bit overzealous. But coming from the CEO of a rival anti-spyware company, it's hard to imagine that it had any other purpose than to paint Aluria in the most negative light possible.
Its not too much of a stretch to imagine why someone like this would write such an article: Prove Aluria is untrustworthy, and there is one less competitor to worry about. Nothing like a good old fashioned negative advertising campaign to stir up some business.
However, if youre going to put a smear job like that out there, you should at least make the slightest effort to check it, say, once a year and see if its still accurate. But CastleCops says they shouldnt. And they dont bother to ask Wayne Porter why he left it up there. Why not? Because it was literally accurate at one time, so therefore they should be allowed to leave it up with no further notice necessary.
Well, technically they might be right. But its still sleazy marketing.
-----------------------
Oh, wait. I almost forgot the most important thing. This has been an incredible waste of time. I've had lengthy emails from a Harvard lawyer, two CEOs, engineers, and who knows who else who want nothing more to argue about this ad nauseum. And you write me and want to know why I've had three WHOLE days to respond to this and yet I haven't, and don't I have some kind of responsibility to society to correct this terrible wrong I've perpetuated? No, gosh darn it, because I've been doing productive things like reviewing spyware, spending time with my family, playing with my dog, eating turkey, and getting away from the computer as much as possible. You should, too. Stop writing about about 10-month old privacy policies already. Geez.
November 30, 2004
More Spyware Sleazebags
Well, here's an interesting one. Now we have anti-spyware review sites using spam as a way to generate traffic. We received this email today on one of our spam bait accounts:
Don't buy ANY anti-spyware programs! Did you know that 95% of the anti-spyware programs recently hitting the internet in waves are actually spyware themselves. Some greedy companies are taking advantage of a world scared of spyware and viruses by releasing anti-spyware programs that ALSO collect your personal information, surfing habits, contact lists, and more. Learn about 'Rogue Spyware' at my website:http://www.spyware-reviews.com for reviews of the current top 5 anti-spyware applications, free scans and valuable discounts.
Best,
BruceBruce Stefani
http://www.spyware-reviews.com
Top 5 anti-scumware programs exposed.
But wait! It gets better. Bruce has not only steeped to new lows as a spammer, he's also copied some of our articles almost verbatim. You can also click here for a nice, easy-to-read version from Copyscape that shows exactly what sections Bruce Stefani has stolen from Adware Report.
Another example can be seen here with our article, What is Spyware?.
They say imitation is the best form of flattery. Thanks, Bruce!
P.S. Bruce, next time, don't spam the guy who you stole from.
November 27, 2004
Spy Hunter Review
| Product: Spy Hunter Price: $29.99 Company Info: Enigma Software Group Editor Rating: 0 stars |
 Click for more info |
+ none
Cons
- Riddled with false positives
- Disabled little of the spyware it detected.
Spy Hunter Product Review
This bare bones, low quality program has few features and failed to remove any of the common spyware we tested for. In addition, it detected a number of spyware programs that were not really installed on our test computers. It is currently the poorest performing product of any we tested, with an overall rating of 21.5%.
Usability
Spy Hunter installed with no problems on both of our test PCs.
Spy Hunter has an intuitive, if a bit simplistic, user interface. The Start Scan button was prominently placed, and the basic options you would expect to find in a spyware removal tool are all there: Start Scan, Stop Scan, Start Remove, and Update.
A full scan took about 15 minutes on our Windows XP box. One annoyance about the program is that the scan results were limited to a very small portion of the screen. It was very difficult to read them because the window wasnt big enough, and the screen cant be resized.
Removal
While Spy Hunter detected 46% of the spyware on our system, it disabled only 15% of it. This was the poorest performance of any of the products weve tested to date.
The latest spyware definitions update file is dated 9/2/2004 and contains 16,968 signatures. This is extremely out-of-date for an anti-spyware tool and this product will not protect you against many of the latest spyware programs released in the past three months.
Rollback
Spy Hunter does not include a rollback or quarantine feature. Rollback is absolutely critical in case a scan accidentally breaks an existing piece of software. On the other hand, because Spy Hunter doesnt actually disable any spyware, the point is moot.
Other Options
Spy Hunter includes only a single option: start scan on boot. It does not include a scheduler, which is another important function found in the better spyware removal tools.
Summary
We recommend that you avoid this product at all costs. It failed to remove any spyware in our tests and the scan results were filled with false positives a probable marketing ploy designed to separate fools and their money.
Purchase Price: $29.99
Free Trial: No free scan is offered.
November 26, 2004
PAL Spyware Remover 1.1 Review
| Product: PAL Spyware Remover 1.1 Price: $29.95 Company Info: PAL Solutions, Ltd. Editor Rating: 1 star |
 Click for more info |
+ None
Cons
- Below average detection and removal capabilities
- 90s era user-interface
- Hasn't been updated since March, 2004
PAL Spyware Remover Product Review
PAL Spyware Remover is a disappointing product. It scored rather low in our testing results, and the user interface was outdated and difficult to use.
Usability
PAL Spyware Remover installed without any hassles on both of our test computers.
With a user interface straight from 1996, PAL Spyware Remover screams retro. The programs functions are located on 7 Win95-style tabs. The important one, Scan, is the second one in.
Removal
PAL Spyware Remover took over 20 minutes to scan our hard drive. We confirmed that it actually scanned every file and did not take shortcuts.
However, the latest version of the program has fewer than 600 spyware definitions in it and the results were very disappointing. While the program detected 39% of the spyware we installed, it disabled only 15% of it. Furthermore, the scan results were riddled with "false positives", which makes the program appear to be more effective than it actually is.
Rollback
Strangely, while PAL has a quarantine feature, it lacks a rollback feature. Once spyware has been quarantined, it can only be deleted.
Other Options
PAL Spyware Remover lacks a scheduler, and can only be configured to run automatically during Windows startup. If you start up your computer in the morning and allow it to run for 20-30 minutes unattended, then this might not be a problem. Otherwise, you will have to remember to run daily scans on your own.
PAL Spyware Remover does have a live update feature, but it is turned off by default. Youll have to navigate to the Settings tab to turn it on.
Summary
The combination of a clunky user interface along with poor detection and removal capabilities makes PAL Spyware Remover a no go. We suggest you look elsewhere.
Purchase Price: $29.95
Free Trial: No free scan only
November 24, 2004
Spybot S&D (Search and Destroy) 1.3
| Product: Spybot S&D 1.3 Price: Free Editor Rating: 2 stars |
 Click for more info |
Pros
+ Free!
Cons
- Latest version (1.3) has serious instability problems and can slow down Internet Explorer or hang the operating system.
- Detects a lot of spyware but often leaves it running.
- Infrequent updates
- No customer support
- Scheduler doesnt work
Review
Spybot S&D 1.3, a freeware spyware removal tool, provides poor protection against spyware. While it detected only 54% of our test spyware, it removed only 23% of it. It has a good user interface and ran faster than nearly every other product we tested, but then crashed our Windows XP computer, rendering it virtually unusable. The price is right, but you may want to backup your system before installing the latest version (read various reports of Spybot instability here).
Usability
We were impressed with the simple and easy-to-use interface. Unlike Ad-Aware or other programs, Spybot (correctly) assumes that most people want to do one thing: remove spyware. They hide all the clutter in the advanced mode. We would have liked to see the scheduler added to the basic mode interface, however.
Removal
As of December 2004, Spybot S&D detects 21,322 spyware signatures. Spybot experts usually recommend that the program should be run in conjunction with another spyware removal program (typically Adaware) in order to provide reasonable protection, although our tests indicate that Spybot is probably no longer capable of removing anything that AdAware (or other good products) can't.
We were disappointed by its performance. While it was extremely quick, completing a scan in only about 6 minutes, the latest version crashed our server when we tried to fix the problems it detected (the latest version did not cause our browser to slow down as in previous tests). Many other people have reported similar stability problems with Spybot S&D as well. After a reboot, our PC was running normally again, but only about 23% of the test spyware had been cleaned.
Like most other products, Spybot doesnt do a complete scan on your system. Instead, it looks in the most common areas only. While the end result is faster, we would prefer to have a more thorough scan along with the ability to schedule it during off hours.
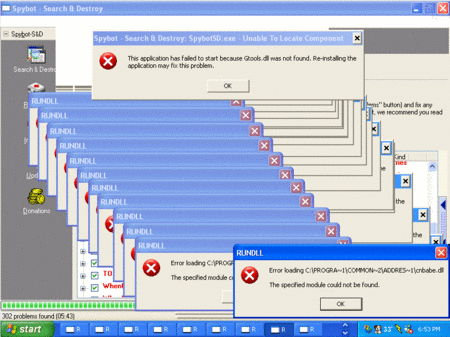
Screenshot of Spybot S&D crashing our server
Another problem with Spybot was a lack of descriptive information about the pests it detected.
Immunization
Spybot S&D provides limited immunization functionality. It does not monitor your RAM or stop browser hijackings in progress. It does purportedly block against about 1,800 browser helper objects that could embed themselves into Internet Explorer, and has an interesting feature to block known bad addresses in the browser, although we question the usefulness of this feature.
Rollback
Spybot S&D does provide rollback capabilities within the program, but in our tests it didnt save all of the tracking cookies that it deleted. However, Spybot S&D does create a checkpoint using Windows XPs system restore functionality, so in a bad situation, you should be able to restore your PC to a previous state. Be warned that the checkpoint feature in v1.3 has been reported to erase previous checkpoints, but this functionality worked properly in our tests.
Other Options
It took us awhile to find the options area (hint: Mode menu, then advanced mode). This is actually a fairly nice area of the program if you want to exercise serious control over the most minute aspects of the program. Our complaint here is that many are trivial or poorly implemented (such as the skins functionality). However, one critical feature, the scheduler, didn't work at all on either of our test PCs. We would prefer that the Spybot writers focus their effort on improving the effectiveness of the product rather than including so many bells-and-whistles.
Support
The program was well laid out so a lot of documentation isnt necessary. In addition, Spybot seems to support more languages than any other product we tested.
However, there is the usual complaint with freeware products: non-existent support. If you run into issues with the product, you will have to go online and wade through a developers forum and hope someone there can (and is nice enough to) solve your problem. Support emails to the company went unanswered.
Summary
Spybot S&D (particularly v1.2 and prior) once provided better protection against spyware, but the commercial vendors have since passed them. Speed and a nice user interface can't make up for average protection, infrequent updates, non-existent support, and the risk of a PC crash.
Sadly, Spybot S&Ds source code has been appropriated by a number of other vendors who continue to shamelessly market it as their own. Don't fall for this. Check out our list of rogue vendors, and if you were considering purchasing any of the products on that list, don't - either purchase one of our recommended commercial products or at a minimum, download Spybot's offering.
Price: Free
NoAdware Review
|
Product: NoAdware 2.0 Price: $29.95 Company Info: NoAdware Editor Rating: 1 star Download NoAdware |
 Click for more info |
Pros
+ Attractive and easy-to-use interface
Cons
- Very poor protection against spyware
- High-pressure sales tactics, including use of false positives in their free scan
- May cause legitimate software to stop working
- Many reports of customers being ripped off
NoAdware Product Review
NoAdware is a controversial product. It is heavily advertised on the internet as an effective adware removal tool. Our tests indicate differently however. We uncovered a product that was unable to detect real adware on our computer, and instead tried to fool us with "false positives". Unfortunately, some of the adware programs it claimed to detect were actually operating system files and legitimate software, including Apple's Quicktime player. Even worse, we've recently (November, 2004) received a rash of emails from people claiming that they paid for the software but the product key wasn't sent and they couldn't get refunds. We were extremely disappointed with NoAdware and strongly recommend that you look elsewhere for an effective product.
Installation
NoAdware installed without a hitch on both of our test PCs. Immediately after running the software, the program prompted us to download the latest spyware definition files.
Usability
NoAdware has a well-designed user interface that is simple to use. Even the most casual user will have no problem figuring out how to use the software. While the software had an attractive user interface on Windows 2000, the Windows XP version was plagued with graphics problems (see screenshot).
Scanning on our Windows 2000 test computer took less than 5 minutes. This indicated to us that either NoAdwares definition file is extremely small, or more likely, it is not performing a full search of the hard drive, instead taking short-cuts which usually leave a significant amount of spyware undetected.
Removal
NoAdwares adware removal capabilities left a lot to be desired.
We ran NoAdware on two infected PCs running a variety of common applications. It flagged two legitimate applications (Quicktime movie player and zlib.dll, a component used by Windows to decompress zip files) as spyware. Allowing NoAdware to remove these files would have caused problems with both Quicktime as well as with Windows.
Furthermore, NoAdware triggered a number of other false positives on both of our test beds. Specifically, it claimed that Flingstone Bridge and Hotbar existed on a brand new installation of Windows 2000. It also claimed that a number of harmless cookies were dangerous adware.
In our first tests of NoAdware several months ago, it failed to catch any of the test spyware that we had installed on our machines. However, the latest version removed only 39% of the spyware programs in our test. While this is a significant improvement over our initial tests, this is still quite low for a commercial product.
Rollback
NoAdware does not allow rollback or quarantine. This feature is necessary in case you inadvertently remove a program that is not spyware (such as Quicktime). Without this feature, NoAdware could potentially cause serious problems on your PC that you won't be able to recover from.
Other
Internet spyware experts have long claimed NoAdware is a "rogue" software product. While these experts can often be overly alarmist, we feel that their warnings that NoAdware makes use of aggressive and deceptive advertising should be heeded. For an extensive list of rogue software, check out Spyware Warrior.
Conclusion
NoAdware is extremely light on features and provides basic scanning and removal capability only. It lacks helpful (and arguably even necessary) features that other products include, such as a scheduler that allows you to scan your computer at night when youre not around.
Summary
NoAdware provided some protection against spyware but could very likely cause stability problems on your PC due to its tendency to flag system files and other applications as spyware. The free scanner is ripe with false positives which could either be a high-pressure sales tactic or merely bad programming. Either way, we suggest you look elsewhere.
Purchase Price: $29.95
Free Trial: No, but the company does offer free scanning to determine the extent of spyware on your computer.
November 22, 2004
Update on CWShredder
A few readers have wrote in to let us know that CWShredder has been purchased by Intermute, and that it is again receiving updates. We originally posted about this great free tool, but at the time, the developer had decided to stop supporting it. The new version (again, we haven't tested this thoroughly) is supposed to remove all the latest variants of CoolWebSearch, when even the best commercial products won't.
Giant AntiSpyware Review
 |
Product: Giant Antispyware 1.0 Price: $29.95 Company Info: Giant Company Editor Rating: 3 1/2 stars |
 Click for more info |
Pros
+ Excellent spyware removal functionality
+ "SpyNet" community shares new spyware definitions between Giant AS users
+ Frequent spyware definition updates
+ Beautiful and easy-to-use user interface
Cons
- new product
- Some user interface annoyances
- A few support complaints
Giant Antispyware Product Review
Giant has made an impressive entry into the antispyware market with the introduction of their novel "SpyNet" technology. Giant users benefit from the combined learning of hundreds of thousands of computer users the world over. When new spyware is detected by just a few people on the network, everyone gets protected. Despite the newness of the product, it is already proving very effective. The latest version claims to have over 1,000,000 signatures in their database so far - over thirty times what any other anti-spyware vendor currently claims. While obviously this number is not an even comparison to other vendors' claims (and they never are), what is obvious is that Giant's product offers extremely effective protection against spyware.
The product provides thorough coverage by detecting spyware running in memory, stopping browser hijackings, examining your startup settings, and eliminating registry changes made by intruding programs.
Going beyond the raw effectiveness of the product, Giant AntiSpyware installs flawlessly, auto-configures, and has a beautiful user interface.
We were very impressed with this product and while it was easily a contender for our #1 position, the relative newness of the product and some support issues held it back.
Installation
Giant Antispyware installed perfectly on both our Windows 2000 and Windows XP test platforms.
Usability
Giant AntiSpyware has a well-designed user interface that is beautiful and easy-to-use.
The first time you run the program, the Giant Setup Assistant will open and guide you through the setup process. By default, the program will connect you to SpyNet as well as set up automated scanning at 2am. This is a nice touch and a marked departure from most antispyware products which require you to set this up manually.
There are a few annoyances with the user interface however. If you schedule daily scans and are away from your computer for a few days, you will have to contend with closing a "scan result" window for every day you were away. This would be a very minor glitch, but clicking the close ("X") button in the top right of the window doesn't dismiss the window - it loads the entire application into memory. For those with slow computers, this can result in a lengthy wait while you suffer through numerous loads. Another annoyance with the program are the frequent "pop-up toast" alerts that often appear while you're working. It would be very nice if Giant provided a way to suppress these windows, or at least only show the most critical ones.
Giant AntiSpyware will guide you through to your first scan. There are two options: an "intelligent" (quick) scan, and a full (slow) scan. The intelligent scan took only 2 minutes on our Windows 2000 PC, while the full scan took only 8 minutes.
The program also installs runtime software that constantly monitors your browser homepage settings and looks for spyware that is trying to install on your PC. The program successfully blocked a number of spyware programs that we purposely tried to install.
Spyware Removal
We ran Giant Antispyware on two infected PCs running a variety of common applications. It did not flag any legitimate applications as spyware.
In our spyware removal effectiveness test, Giant Antispyware tied for first with Aluria's Spyware Eliminator. Giant detected and removed 85% of the spyware we tested it against, and it completely recovered all of the disk space used by each. Giant AS was very effective against the most common forms of spyware, but failed to catch the newer ones, presumably because few people in the SpyNet program have so far encountered these.
Rollback
Giant AntiSpyware lets you rollback any changes it makes. This is helpful if you have wiped out spyware that is needed by an otherwise useful program (Real Player and Kazaa are typical examples of software embedded with spyware on your PC that wont run without it).
Customer Support
Giant's customer support was quick to respond to our test emails and offers a "no questions asked" refund policy. In addition, the company now offers live chat on their website for quick turnaround of support issues.
However, we have received a number of complaints in the past two months stating the company had been slow in returning support emails, but Giant claims this was a temporary problem and everything should be running smoothly now.
Other Options
Giant includes a number of "security agents" with their software as well. These include a department-of-defense level "file shredder" as well as functionality to remove your internet "tracks" from your computer (both are located in "advanced tools").
Giant Company also has an excellent online spyware library that you can click through to find out more information about the spyware programs installed on your PC as well as the companies who created them.
Summary
Giant AntiSpyware offers superior protection and immunization against annoying spyware. While it scored very highly in our spyware effectiveness testing, the product is a bit newer than others so we've adopted a wait-and-see approach to ensure that the bugs are out of the system. However, its SpyNet unique SpyNet technology, frequent updates, excellent user interface, and competitive price have propelled Giant AntiSpyware all the way to our #2 spot, displacing Webroot's Spy Sweeper.
Purchase Price: $29.95
Free Trial: Yes, 15 days.
November 21, 2004
CoolWebSearch: The nastiest spyware on the planet
What the spyware companies hope you don't ask
Every week we get a number of emails asking what will remove CoolWebSearch or it's twin brother, About:blank. We could never give an educated answer because frankly, we had heard so much bad news about this piece of spyware that we were afraid to install it on our test computers.
However, we recently made a large investment in a new test lab. This lab allows us to create virtual servers, infect them, test anti-spyware tools, and then blow away the server so we can start over. So we rolled up our sleeves and installed CoolWebSearch.
Bad news. So far, we've had very little success finding anything that will remove this product. Put simply, this parasite will really mess up your PC. The second we find a product that will remove it, we'll let you know.
November 13, 2004
Spyware Smear Campaigns
About once or twice a week we receive a borderline-hostile email challenging our reviews and recommendations. We are sometimes able to trace these emails back to the source only to discover that the person who wrote it has some affiliation with a rival anti-spyware company. We thought we caught someone else doing exactly this a few days ago, but it turns out we were wrong. However, the chain of emails led to us uncovering some of the dirty tactics spyware vendors are now using on each other.
The original email was very "anti-Aluria", citing the WhenU-Aluria controversy. While we appreciate the various viewpoints on this subject, we are entitled to our own. We can summarize our position by stating that while we personally do not want pop-up advertising on our computers, as long as WhenU gives people a clear and informed choice about whether or not to accept this type of advertising, then they are not a spyware company - regardless of their past history. Furthermore, Aluria has given spyware companies a way in which they can reform. God Bless 'em.
We dug up some more coverage of the debate in this article printed recently in the Boston Globe. At the end, the article begins to uncover just a bit of the hostilities and smear tactics that many spyware companies are now resorting to in an effort to improve their sales.
If only it went that far.
The reader who sent in the email found this article at Spyware Guide, which purports to explain why Aluria is an untrustworthy company. The casual reader would be fooled by this article, as I was, into thinking that perhaps there was something fishy going on at Aluria. I contacted the President, Rick Carlson, about this and to make a long story short, here's what I found:
* The article misquotes Aluria's privacy policy. These are not typographical or small deviations, either. They are gross fabrications:
Spyware Guide:
ALURIA believes in permission-based marketing. By using our website and/or purchasing any products and services marketed by ALURIA, you expressly consent to the terms of this policy."
The above text does not appear anywhere in Aluria's privacy policy. Here's another quote:
The personal profile information that you submit to ALURIA and its Advertisers remains your property, but by submitting that information to ALURIA, you grant ALURIA the right to use that information for marketing purposes including, but not limited to, sharing such information via co-registration with Advertisers.
The above quote, as Spyware Guide points out, would make you think Aluria is going to sell your information to anyone they can. I was quite surprised when I read this, because we have bought a number of licenses of Aluria's product for testing purposes and have not received one unsolicited email from them. Rick Carlson, Aluria's president, verified this and said that the company has never sent out a single unsolicited email to purchasers of their products.
This makes a lot of sense, given that the actual quote from the privacy policy is this:
This Privacy Policy also applies to consumers that have agreed to receive e-mail and direct mailings from ALURIA and its Advertisers, whether at one of our Websites, via email, direct mail, on third party websites, via co-registration or otherwise. The personal profile information that you submit to ALURIA and its Advertisers remains your property, and will not be used by Aluria for marketing or shared with other companies without your express consent.
This quote expressly states that Aluria will not share your information with anyone without your permission.
* The article was written by Wayne Porter, the CEO of XBlock.
XBlock's XCleaner was one of the original products that we reviewed here at Adware Report. We eventually removed it from the reviews because the product did not work well on our computers and we could never get an reply from their customer support. We had assumed that the company had gone out of business, but it does appear that they are still selling their software.
* Spyware Guide is a website owned and operated by XBlock.
Emails sent to Spyware Guide are returned by XBlock customer support. Also, the WHOIS registrant for this site is:
Registrant/Owner:
000-WP83754
Xblock Systems LLC
10187 Sperry Road
Kirtland OH, 44094
* Aluria's lawyers have sent a Cease & Desist letter to Spyware Guide to remove this article, and for good reason. It's not a matter of simply disagreeing with the article. The article grossly misquotes Aluria's privacy policy for the purpose of undermining their respectability as a company.
We'll keep our ears open about this one and keep you posted to new developments.
Upcoming Spyware Tests
A note to our readers regarding the spyware tests.
Comparative testing of spyware products is extremely time and labor intensive. To run our monthly tests, we first load each PC with a number of spyware products, creating system checkpoints along the way (so we can undo any mistakes). Then we have to install products one-by-one, perform our tests, and manually verify which spyware products were removed and to what degree. After each test is complete, we revert back to our previous checkpoint and repeat the process. The entire process takes several days of work. We have had so many requests to review new products, that this has delayed new testing for over a month now.
To remedy this, we're upgrading our systems to allow us to perform quicker and more standardized testing of all the new anti-spywareproducts. This will allow us to add more "bait" programs to our spyware effectiveness test and cover more products in far less time than it took us before.
Thanks for your patience while we sort this out!
The FBI's Spyware (Magic Lantern)
My thanks to Stephanie Harris Tallent for alerting me to the FBI's keylogger, Magic Lantern. From About.com:
Calling it a just "workbench project," that could not be further commented on, the FBI has confirmed the existence of its latest Internet-eavesdropping, controversy-raising snooping device exotically code-named "Magic Lantern."
Magic Lantern is software that, once installed on the suspect's computer, will record every keystroke typed. The gathered keystrokes will then be analyzed by the FBI to extract passwords. The harvested passwords will be used by the FBI to access the suspect's email messages and other encrypted documents, or to gain access to other computers contacted by the suspect via the Internet.
While the FBI has long acknowledged using its controversial Carnivore system to intercept data transmitted to and from a suspect's computer over the Internet, Magic Lantern differs substantially in design and, as civil liberty advocates will argue, its level of intrusion on personal privacy.
Carnivore is installed between the suspect's PC and the Internet, typically on hardware under the control of the suspect's Internet service provider. Magic Lantern, however, is installed directly on the suspects computer via a Trojan horse virus delivered over the Internet. Identity-stealing hackers have recently been sending similar viruses to computer users around the world via disguised email attachments hoping to gather passwords, user names, bank account and credit card numbers, and similar personal information.
When asked if use of Magic Lantern would require a court order, as does Carnivore, FBI spokesman Paul Bresson told reporters only that, "Like all technology projects or tools deployed by the FBI it would be used pursuant to the appropriate legal process."
Since Magic Lantern is essentially "just another virus," anti-virus software can be written to defeat it. According to a Reuters report of December 12, the FBI has not asked anti-virus software vendors to refrain from creating anti-Magic Lantern software. Most vendors, however, have stated they would not cooperate with the FBI unless ordered to do so by the courts.
Civil liberty groups argue that use of an Internet snooper systems like Carnivore and Magic Lantern represents an unreasonable search and seizure according to the Fourth Amendment to the Constitution.
The FBI claims authority to intercept telephone and Internet communications under Title III of the Omnibus Crime Control and Safe Streets Act of 1968 and parts of the Electronic Communications Privacy Act of 1986, or "ECPA".
According to the Department of Justice, interception of Internet data requires a much higher level of judicial approval than traditional searches.
"Unlike typical search warrants, federal magistrates are not authorized to approve such applications and orders, instead, the applications are viewed by federal district court judges. Further, interception of communications is limited to certain specified federal felony offenses." -- Testimony of FBI Assistant Director Donald M. Kerr before the House Judiciary Committee - July 24, 2000.
Congress, however, had concerns about possible misuse or overuse of Internet snooping systems in August, when lawmakers required the FBI to provide them with detailed reports on the Agency's actual use of Carnivore.
Of course, that action came before Sept. 11, 2001. Given the importance of the war on terrorism and the fact that terrorist groups are known to formulate plans, raise funds and spread propaganda over the Internet, do not look for Congress to clip the wick of the Magic Lantern.
November 10, 2004
ActiveX often marks spyware spot
Adware Report's Comment: Microsoft says we should all buy new PCs to protect ourselves from spyware. Is anyone surprised by this comment?
SEATTLE A technology called ActiveX is the main reason Microsoft's dominant Internet Explorer browser has become so susceptible to invasive spyware, security experts say.
ActiveX, which permits an outsider to silently upload programs to a Web-connected computer via the browser, has become the tool of choice for spyware distributors.
The most common type of spyware called adware tracks Web-surfing habits and reports back to advertisers. But cybercrooks are increasingly using ActiveX to surreptitiously upload more invasive forms of spyware designed to carry out an array of identity-theft schemes.
A recent survey by the National Cyber Security Alliance and America Online found 80% of the PCs in 329 homes infected with an average of 93 types of spyware.
Microsoft has responded with Service Pack 2 a free upgrade for Windows XP computers containing an array of operating system and browser safeguards. One key upgrade a download-monitoring tool alerts the PC user any time someone tries to use ActiveX to install a program through the Explorer browser.
But Service Pack 2 only helps owners of Windows XP PCs. Roughly 43% of the 500 million PCs on the Internet at any given time use earlier versions of Windows, according to Google.
To get access to the most secure version of Internet Explorer, Microsoft advises hundreds of millions of owners of PCs using older versions of Windows to buy a new PC.
"It's like buying a car," says Gary Schare, Microsoft director of security for Windows. "If you want to get the latest safety features, you have to buy the latest model."
Windows PC owners can switch to alternative browsers supplied by Firefox or Opera, both free. Mac owners can use Safari. None supports ActiveX technology, making them immune to the most pervasive forms of spyware. (Related story: Firefox ignites interest in alternative browser)
"We've been anti-ActiveX since day one," says Hakon Wium Lie, Opera's chief technology officer. "It is very hard to limit some really nasty things, while keeping the good things."
November 05, 2004
FTC to Congress: Lose the Anti-Spyware Plans
The following article re-iterates many of the points we made two weeks ago in our press release about anti-spyware legislation, and then goes on to make a few more excellent points.
November 5, 2004
By Roy Mark
Original article can be found here.
The Federal Trade Commission (FTC) again warned Congress today that anti-spyware legislation is unnecessary with the existence of adequate fraud laws to contend with spyware perpetrators.
FTC Commissioner Orson Swindle, speaking to Capitol Hill staffers at a Cato Institute luncheon Friday, questioned the need for new laws.
"Our experience at the Department of Justice and at the FTC is that [current] law is adequate," Swindle said. "Most, if not all, spyware is executed under a deceptive cloud. If people are deceived, it's a deceptive practice."
The FTC has been skirmishing with the House of Representatives all year over the need for anti-spyware legislation. In April, the FTC held a spyware workshop, and concluded that technology solutions, combined with current deceptive practice laws, would be a superior alternative to any new laws.
However, regardless of the FTC's stance, the House went ahead with two anti-spyware bills: the Spy Act (H.R. 2929) and the Internet Spyware Prevention Act of 2004 (H.R. 4661). The Spy Act prohibits unfair or deceptive practices related to spyware and requires an opt-in notice and consent form for legal software that collects personally identifiable information from consumers. The Internet Spyware Prevention Act makes it a crime to intentionally access a computer without authorization or to intentionally exceed authorized access.
Both bills are likely to die on the Senate side when Congress reconvenes in a lame duck session on Nov. 16, but anti-spyware advocates in the House have vowed to revive the legislation when the new Congress meets in January.
Swindle said the biggest problem facing the FTC is not the need for new laws, but the ability to locate and prosecute spyware vendors.
"I'm of the opinion that many of the scams in this country are short-lived. They get a lot of money, they take a lot of money and the guys are out of there," Swindle said. "Sometimes they get caught and they don't have any money left. The cost of getting caught amounts to nothing more than another line item on the balance sheet."
Jim Harper, director of information policy studies at the Cato Institute, added that anti-spyware legislation would be no more effective than the CAN-SPAM Act signed by the president in December.
"We didn't need federal spam legislation. The problem there wasn't the need for a new law, but finding the people who send spam," Harper said. "CAN-SPAM hasn't worked because you can't find spammers. You can't reach them because they are operating in an eastern block country or the country where they are operating doesn't cooperate with the [U.S.] federal government."
Swindle pointed to the FTC's first case filed against a spyware operator in October as an example of the current law working.
"We didn't need a new law to get that done," Swindle said. "We're confident we're going to win that case and there's more coming."
Swindle was quick to praise the "good intentions of Congress" in attempting to deal with spyware, but he cautioned the Hill staffers about the unintended consequences of well meaning legislation.
"First you have to get by defining what spyware is," Swindle said. "Poorly written legislation can cause enormous problems. We have to write rules based on laws passed by Congress in order to implement the law. Quite frankly, sometimes we have no earthly idea what the Congress meant to say."
November 04, 2004
When Bad Companies Go Good: A Step in the Right Direction or Just Another Scam?
Aluria Software Certifies WhenU as Spyware SAFE, Industry insiders Hit The Roof.
A heated debate has erupted surrounding the recent endorsement by Aluria Software, a well-known anti-spyware vendor, of WhenU, a well-known adware company. Aluria has certified WhenU as spyware-free as part of their Spyware SAFE Certification Program, a move which has drawn criticism from some industry insiders. Are they right or simply acting from their own self-interests?
We dug deeper for the facts.
(Full Disclosure: We recommend Alurias product, Spyware Eliminator, on this site.)
In this corner: WhenU SaveNow!
First, what is WhenU? The program is considered to be Adware, an application that displays advertisements on your desktop, usually through pop-up windows or through a bar that appears on your computer screen. This particular program watches your browser and will display advertisements when it sees targeted URLs. For years, this program has been one of many responsible for the unwanted popup ads that have tormented web surfers.
Adware it can be good or it can be bad
In its pure form, adware is not unethical or a threat to your privacy. In fact, desktop advertising is a legitimate business. Many forms of advertising-supported software exist, most notably the famous free email client, Eudora, or the equally famous web browser, Opera. If you choose to pay for the software, the ads go away. If not, the advertisers pay for it so you can go on using the software for free.
The problems started when companies began installing adware without the users knowledge. This was often done by distributing the software with file sharing programs, including BearShare, iMesh, KaZaa, and the Global DivX player. While these companies claimed to get consent from users before installing, often this disclosure was buried deep within lengthy EULAs that few people ever read. Even worse, some companies figured out how to install the software on peoples computers when they visited a particular website (drive-by installs) without ever informing them. Before long, there were lots of companies engaging in these practices, and our computers began to grind to a slow, pop-up-serving halt.
Anti-spyware products effectively end this problem by forcefully removing these parasites, usually kicking and screaming. WhenUs adware product, SaveNow, is one of these parasites that are targeted by practically every spyware removal product on the market.
Apparently, WhenU has changed their stripes. They realized that there was little future in spyware, so theyve claimed to reform their business model so that they could continue doing business. Until recently, nobody believed them. That is, until Aluria audited them as part of their Spyware SAFE certification program.
The Spyware SAFE program
Adware Report (this site) has been audited by Aluria and can attest to the thoroughness of the process. To become certified, the company must comply with 24 criteria, including the ones on the partial list below:
* Any software installation package must have a EULA with clear notification of all items installed, their functions, and intentions.
* Software will not be installed without explicit notification and consent of the user
* Software will not exploit vulnerabilities or change security settings
* Software will not install programs that can not be easily uninstalled through Add/Remove programs
* Software will not request personal information or make use of data for marketing purposes without clear and explicit user opt-in
* Software will not automatically opt-in users to deals, offers, newsletters, etc.
* Software will not serve advertising that is not clearly branded by the company
* Software will not install anything that removes or prevents other software from functioning
* Software will not monitors users behavior, such as keystrokes, emails, IMs, without explicit permission from the user
* Software will not alter search results
* Software will not redirect users to unrequested websites
(The complete list is available here.)
Taken as a whole, the criteria to become certified is comprehensive and ensures that if you install a spyware SAFE application, no untoward activity will take place on your computer.
The New WhenU
We visited the WhenU site (http://www.whenU.com) and were surprised by the new look. The site reads Advertising You Want and the company has remade itself into the image of an upright corporate citizen. With a clearly labeled privacy center as well as a branded spyware scanner, it appears, on the surface at least, that WhenU is serious about their new image. But just to make sure, we loaded up the infamous SaveNow adware program to see if it truly complies with Alurias SAFE certification criteria.
The program did serve ads when we visited certain websites. The install program clearly told us we were installing adware, the ads were branded, no other software was loaded, and the program uninstalled cleanly from memory and our hard drive with add/remove programs.
By most definitions, WhenU is no longer spyware.
So Whats The Problem?
Desktop advertising is a legitimate opt-in business model, provided that consumers are offered it as a safe and informed option. If you dont want advertising on your desktop (and most people dont), then simply dont install the software. Adware only becomes a problem when companies install it without your knowledge and/or use sneaky tactics to prevent you from removing it.
So is Aluria in the wrong for certifying WhenU as spyware SAFE? Eric Howes, a spyware commentator from the University of Illinois, thinks so. He calls the current situation Conflict of interest 101 and claims that Aluria shouldnt be in league with the very people [spyware companies] are supposed to be judging.
We take a different position. If the Aluria program has made it possible for a bad company to turn good, then theyve done more than fight the problem. Theyve taken perhaps the first step towards solving it. Alurias program provides spyware companies with a motive as well as a viable way to come clean. Contrast this with the anti-spyware legislation making its way around Congress, which is all but useless against the east European and other foreign spyware companies.
While we havent performed a thorough audit of WhenU ourselves, it does appear that they are abiding by the certification criteria. If so, theyre no longer a spyware company and it makes no more sense for Aluria to remove their products then it would to remove Eudora. We cant help but feel that comments like Erics are based out of nothing more than past prejudices.
Criticism within the pharmaceut oops! Spyware industry
What we didnt expect was the reluctance of other spyware companies to perform their own objective tests of the new WhenU. Instead, theyve resorted to launching attacks against Alurias bold and unprecedented move. Surprising perhaps, but only until one realizes that having bad guys is good for business. You cant sell the medicine unless theres a disease.
Our conclusion is that there is entirely way too much posturing going on around this. Aluria made a bold and surprising decision to certify WhenU in their Spyware SAFE program, and rivals have predictably used it to launch attacks in an attempt to discredit their certification program.
However, we feel that Alurias program has been the first real step towards a cure, not merely a treatment.
October 25, 2004
'Spam King' ordered to disable spyware
Associated Press
CONCORD, N.H. A U.S. federal judge has ordered a man known as the "Spam King" to disable so-called spyware programs that infiltrate people's computers, track their Internet use and flood them with pop-up advertising.
U.S. District Judge Joseph DiClerico issued a temporary restraining order Thursday against Stanford Wallace and his companies, SmartBot.net Inc. of Richboro, Pa., and Seismic Entertainment Productions Inc. of Rochester. SmartBot's principal place of business is Barrington.
Prosecutors sought the injunction on behalf of the Federal Trade Commission, which targeted Wallace in its first anti-spyware action.
The judge ordered Wallace to remove software code that exploits security holes in computer operating systems and Web browsers, then tracks people's Internet use to bombard them with pop-up ads.
Wallace also is accused of trying to sell computer users $30 (U.S.) remedies called "Spy Wiper" and "Spy Deleter" that the FTC says don't work.
"Spyware" describes a broad category of software that can be installed through unsafe e-mails or Web pages. It sometimes is bundled with other software that consumers download and install, such as file-sharing programs that can be used to download music and movies illegally.
Spyware programs quietly monitor which websites a consumer visits, and some may even redirect users to different sites. They can make computers sluggish or cause them to crash.
"We see it as good relief for consumers," FTC attorney Laura Sullivan said of DiClerico's order. She could not say how pervasive Mr. Wallace's spyware was.
Mr. Wallace's lawyer, Ralph Jacobs of Philadelphia, said Mr. Wallace wants "to use the Internet for advertising in lawful and proper ways."
"There are a wide range of advertising practices on the Internet that use some of the techniques the FTC objects to, and the defendant looks forward to an opportunity to establish exactly what advertising practices are allowable," Mr. Jacobs said.
Mr. Wallace formerly headed a company called Cyber Promotions in the 1990s that sent as many as 30 million junk e-mails daily to consumers, earning him the nicknames "Spamford" and "Spam King." He left the company after lawsuits by America On-line and CompuServe.
The judge scheduled a hearing for Nov. 9.
October 22, 2004
Spyware Legislation: Too Little, Too Late?
CHICAGO, Oct. 22 /PRNewswire/ -- Congress recently passed the "Spy Act" to
help subdue the serious spyware threat facing millions of Americans. But as
they work out the legislative kinks, the anti-spyware market is already
turning the tables against spyware.
In this election year, there appears to be only one thing that Republicans
and Democrats can agree on - anti-spyware legislation. Last week's
extraordinary bipartisan support for the "Spy Act," a vote of 399-1, shows
just how serious spyware PC infection can be. While the "Spy Act" would
create a complicated set of rules governing software capable of transmitting
information across the Internet and give the FTC authority to police
violations with fines of up to $3 million, where does this legislation leave
consumers and those already in the anti-spyware industry?
As usual, the market is leagues ahead of the government. "I don't believe
that legislation is going to have much of an effect on the market at all,"
said Richard Stokes, the founder of Adware Report
(https://adwarereport.com), a popular anti-spyware product review site.
"Anti-spyware laws will discourage domestic spyware companies, but it won't
eliminate them because most spyware firms will continue to operate from
outside the country."
As Washington bureaucrats continue to debate how far-reaching spyware
legislation should be, the market continues to push the anti-spyware envelope
with improved software to eliminate spyware. "Anti-spyware companies are
battling the problem head-on and making it much harder for the bad guys to
make money doing what they're doing," said Stokes.
And while the battle against spyware is far from over, corporations will
get immediate benefits from investing in spyware removal products. "By the
time congress catches up," added Stokes, "the anti-spyware companies will have
licked the problem." Most anti-spyware pundits predict that within the next
two years there will be a handful of top anti-spyware products that completely
eliminate spyware.
In fact, a few anti-spyware products are already making a serious impact.
Most recently, Chicago based GIANT Company developed GIANT AntiSpyware with
SpyNET, the industry's first anti-spyware network. By connecting millions of
consumers, SpyNET has amassed a library of nearly 200,000 spyware signatures,
making it the most up-to-date and most effective anti-spyware software
currently on the market.
As snailish Congressional leaders debate the efficacy of spyware
legislation, anti-spyware developers and review sites, like
https://adwarereport.com, already provide consumers with viable solutions
to help eliminate their threats today.
October 11, 2004
House and FTC Fight Spyware
Monday, October 11, 2004
By Roger Park, Associate Editor
The House announced it has passed an anti-spyware bill that would institute prison penalties for people convicted of installing such programs without a computer user's permission. The Federal Trade Commission also announced they have filed the first case in the country against two software companies infecting computers with spyware and then trying to sell people the cure, according to the Associated Press
The new bill, "Internet Spyware Prevention Act," gives the Justice Department $10 million to crack down on spyware companies," the AP reported.
Offenders under his bill would be sentenced for up to five years for secretly installing spyware to break into someone's computer and committing another federal crime, the AP reported.
The FTC requested a temporary restraining order from the U.S. District Court for the District of New Hampshire against Seismic Entertainment Productions Inc., Smartbot.Net, Inc., and their owner Sanford Wallace, the AP reported.
The FTC accused the companies of bombarding computer screens with pop-up ads and then luring consumers to pay $30 to fix the problem. The commission is seeking an injunction to the get the companies to stop and offer restitution to consumers, the AP reported.
iMedia Connection
October 06, 2004
About:Blank
About:Blank is another name for the CoolWebSearch morphing spyware. As mentioned in the CoolWebSearch article, this is one of the most insidious and prevalent spyware programs currently on the net, largely because it is nearly impossible to remove. This particular spyware has been unusually active over the past two weeks (October, 2004).
About:Blank displays the following characteristics:
1. Replaces your home page with a new one titled "about:blank". This page contains a pseudo-search engine with various subjects like "art", "cars", and "shopping".
2. Installs a Browser Helper Object into Internet Explorer. This BHO consumes system resources and slows down your internet connection.
3. Restores itself after its file directory is deleted.
4. Restores its registry settings once they have been deleted.
5. Is difficult to remove from memory.
6. Starts with the operating system. If you remove it from the auto-start settings, it will restore itself there.
7. Later versions change their executable to avoid detection by the simple hash recognition algorithms that most anti-spyware products use.
8. May also store executable code in your temporary internet explorer files.
Effective Tools
CWShredder will remove older variants, but because it is no longer being updated, it is becoming less effective every week. Webroot Spy Sweeper, Ad Aware, nor Spybot S&D seem to be effective at removing this product. Aluria has just released a new update to their Spyware Eliminator product which they claim will remove About:Blank (but keep in mind that we have not tested this).
September 16, 2004
Spybot S&D Ineffectiveness
It appears that others are validating our test results with Spybot S&D. Although we too appreciate the developer's idealism, Spybot has just not performed all that well in our tests. It would really be a lot better if a small team of volunteer developers could keep up with the aggressive spyware companies, but that's just not the way things work.
Your thoughts?
From "Spyware Confidential"
Idealism vs. commercialism
-8/17/04
I used to be a big fan of Spybot. I thought it had just the kind of rough-and-tumble feel that works best against spyware, it includes a bunch of other features, and its developer operates in an altruistic fashion. However, I perform a lot of real-world testing against some very nasty spyware, and I've seen Spybot either miss major spyware or not be able to remove the stuff it does find. Though I appreciate the developer's idealism, I'm not sure it competes well with other developers' commercial interests in keeping spyware definitions well researched and up-to-date.
A spyware-removal tool is only as good as its definition file, and there's something of an arms race among major developers of spyware removers, such as PestPatrol, Spyware Doctor, and Spy Sweeper, to have the most comprehensive and frequently updated definitions. Also, spyware prevention has become very good in the major commercial programs, which monitor new programs you install for spyware. In the end, Spybot's resident protection hasn't seemed effective enough on my test machine.
September 15, 2004
August Spyware Effectiveness Test Results
In our August round of testing, we analyzed seven of the most popular spyware removal products and rated each according to their ability to detect, remove, and completely cleanse a target PC of all spyware.
Test Results
Our results found the top commercial products to be more effective than popular free alternatives. Two products, Aluria Spyware Eliminator and Webroot Spy Sweeper, performed the best of all spyware-removal software tested. Of the free products, Lavasoft Ad Aware removed a significant amount of spyware, while Spybot S&D detected a large amount of spyware but often failed to remove it.
Detection
Our detection test measured the extent to which each product detected the spyware that we had intentionally installed on our test computer.
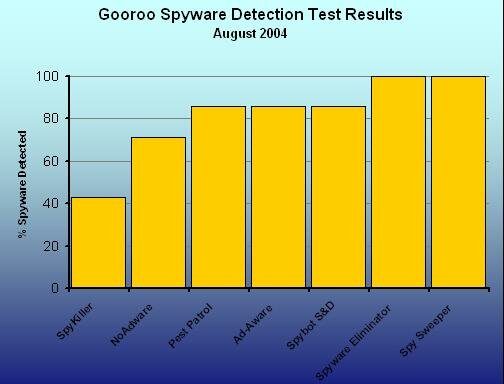
Spy Sweeper and Spyware Eliminator performed the best, but free alternatives, such as Ad Aware, also performed reasonably well. It is perhaps of little surprise that some heavily advertised commercial products such as NoAdware and SpyKiller performed rather poorly.
Removal
The removal test measured the extent that each product successfully disabled our test spyware.
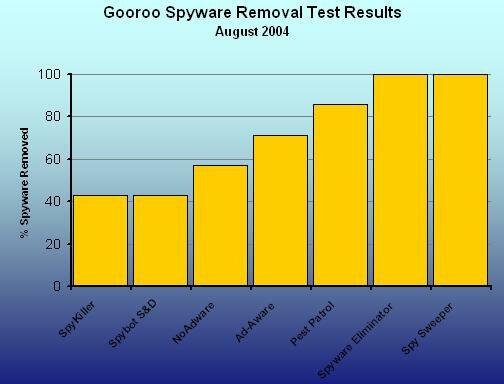
The top commercial products performed much better than the free alternatives, with Ad Aware performing better than Spybot S&D.
Cleansing
The cleansing portion of our test measured the extent to which each product removed all traces of the targeted spyware. This included registry settings and associated text and image files. While these files are harmless (once their host spyware has been disabled), they continue to consume disk space.
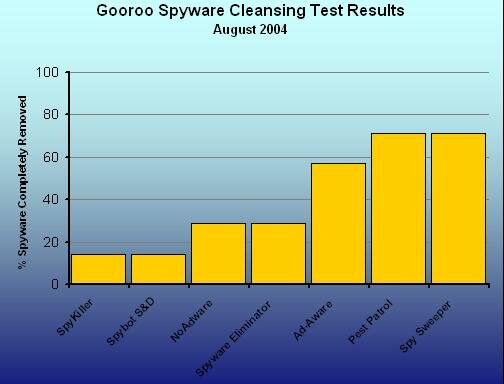
We found that none of the tested products thoroughly removed all traces of detected spyware. Two commercial products, Spy Sweeper and Pest Patrol, performed the best in this regard, while Ad Aware came in third.
Overall
In terms of pure effectiveness, three commercial products, Spy Sweeper, Spyware Eliminator, and Pest Patrol stood out. The latest version of Ad Aware performed well, while NoAdware, Spybot S&D, and SpyKiller coming in last.
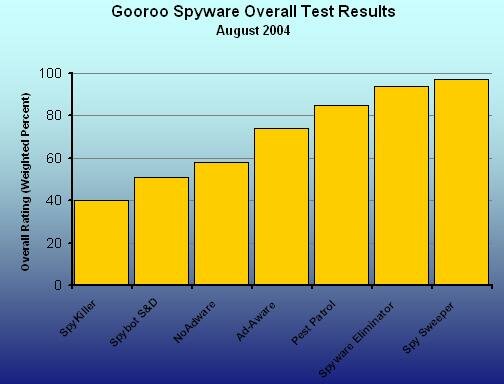
Why This Test Is Useful
This is the first and only test that attempts to provide a fair comparison between different spyware removal products.
Anti-spyware vendors often make use of various marketing measures to bolster their claims of effectiveness. By far the most abused of these is the number of spyware programs protected against measure. While there is some comfort in knowing that your spyware-removal solution will protect against more spyware programs than competing products, this measure doesnt take into account the recency or prevalence of different threats. While an older product may protect against considerably more spyware than a newer one, much of that protection may be against outdated programs that are not as widespread as they once were.
Furthermore, spyware vendors often include multiple traces related to a single spyware program, such as associated html, text, and image files. A single spyware program will typically have as few as one or as many as 40 associated files. Even if your software claims to have 28,000 entries in its signature file, you have no way of knowing if that means you are protected against 700 spyware programs or 7,000.
Finally, another common tactic that vendors use is to count tracking cookies in their spyware counts. Tracking cookies are for the most part harmless snippets of data that websites use to track your usage of their site. While some websites do use them to track your surfing habits (DoubleClick is a prime example of this), the vast majority of cookies are completely harmless.
Our test avoids these problems in comparing different products by testing the effectiveness of each anti-spyware tool against a limited number of known, current spyware programs. Each program is rated for its ability to detect, remove, and completely cleanse these pests from a target computer.
This test does not attempt to capture "soft" aspects of each product, such as usability, price, or the inclusion of various features (such as a scheduler). It merely attempts to provide a fair comparison of raw effectiveness of each product. See our product reviews to compare these aspects of each product.
Click here for more details about our anti-spyware testing methodology.
September 13, 2004
Aluria website being upgraded today
A few people have emailed us informing us that the Aluria website isn't working. We called up the company and they informed us that they are upgrading their servers (the current ones have been going down as a result of the hurricanes) and hope to have service restored soon.
September 12, 2004
CWShredder
What is CWShredder?
CWShredder is a utility used to remove the extremely stubborn CoolWebSearch spyware program. CoolWebSearch is an aggressive and sophisticated browser hijacker which receives frequent updates by the authors. CoolWebSearch is nearly impossible to remove by hand, and often the only way to do so is by manually re-installing the entire operating system. While a good spyware removal product such as Spyware Eliminator or Spy Sweeper will usually be able to remove CoolWebSearch, this particular breed of spyware is so frequently patched that sometimes these products can not keep up.
In such a situation, you may be able to remove CoolWebSearch with this handy little utility, CWShredder, written by Merijn Bellekom. Unfortunately, Merijn claims that the current version of CWShredder, v1.59.1 will be the last as he is unable to keep up with all of the latest versions of CoolWebSearch.
When do I need to use CWShredder?
If you are already running an effective spyware removal tool on your computer and you notice any of the following systems, you may be infected by a recent update of CoolWebSearch. Try running CWShredder and see if this fixes the problem:
* Hijacks to various search engines. Different variants of CoolWebSearch will redirect you to different sites.
* When a URL is mistyped in the browser, CoolWebSearch will redirect the page to affiliate websites as well as CoolWebSearch.com.
* Installs bookmarks to adult websites in the favorites menu.
* Installs toolbars into the browser.
* Slows down PC.
* Can cause reboots.
* Targets anti-spyware websites, usually vendors of spyware removal tools. Once infected with CoolWebSearch, you may be unable to visit these websites to download their products.
* Will open porn popups if it thinks the website being viewed is pornographic in nature.
* Can cause significant slowdowns when attempting to type into a browser.
* Will add CoolWebSearch.com to the trusted sites list.
* Your anti-spyware product refuses to start or scan.
Download CWShredder
As a service to Adware Report readers, we have mirrored the latest version (v1.59.1) of CWShredder on our server.
User feedback on customer support
Your opinion is important!
Please tell us about your customer support experiences with the different vendors whom we review on this site (or any others). We've opened up the comments section of this article, or if you'd prefer, you can just send us a private email using the "contact us" link at the top of every page.
Thanks for sharing!
Security Warnings at Aluria Software
If you receive a security warning when visiting the Aluria website today, don't panic. Aluria is installing new webservers in response to the downtime which resulted from Hurricane Charley. Until their new SSL certificate is in place, you may see a popup warning you that the publisher can not be verified. Just press 'ok' and continue.
This problem should be resolved by this evening.
September 11, 2004
Addaware
|
Product: Addaware SE Price: $39.95 Vendor: Lavasoft Editor Rating: 3 stars Addaware download |

|
Pros
+ Better spyware protection than most products
+ Addaware SE has an improved user interface over previous versions.
Cons
- Still a confusing user interface. Most of Addawares useful functionality is hidden from the average user.
- Cant schedule scans on-demand or boot-up scans only mean your computer will be unavailable while it checks for spyware.
- Poor customer support.
- Higher priced than other top rated solutions
Addaware Adware Remover Review
Addaware SE, the latest update to Addaware's flagship product, is a good product that provides decent protection against many spyware programs, but lacks some important functionality such as the ability to schedule scans. The user interface is difficult to use and might appeal more to people comfortable with computers.
It can detect spyware programs running in memory, examine startup settings, block browser hijackings, remove tracking cookies, and fix registry changes made by intruding programs. It can also remove stubborn spyware by flagging it for deletion (before it loads) during the next bootup cycle.
Our August test results indicated that Addaware protects against many common spyware programs, but not as effectively as our top rated products. However, Lavasoft does offer a free Addaware download.
Addawares real-time monitoring (immunization) is not as effective as other products and was difficult to locate and configure. It does block browser hijackings, protect important registry settings, and block suspicious processes, and it even has functionality to scan for spyware in memory but this is very limited. During our tests, it did successfully detect in-process spyware, but it was unable to terminate the offending process.
Usability
Lavasoft has made significant improvements in the user interface with the latest version of Addaware. Many of the cryptic and non-working buttons (such as "ProcWatch") are gone, although some remain (such as the "Add-ons" button).
If youre a computer engineer and enjoy tinkering with background processes and log files, Addaware exposes this sort of powerful functionality to you. On the other hand, if you are a regular computer user, you will likely become very frustrated by the complexity and awkwardness of this program.
Removal
Scanning was very fast completing in about 6 minutes on our Windows 2000 test PC. This was much faster than any other product we tested.
While Addaware claims to detect more spyware programs than other vendors, in our tests it failed to find a number of unwanted browser plug-ins (such as the "Websearch toolbar") that other products correctly detected. In our more formal Spyware Effectiveness Test, Addaware missed 22% of common spyware. This gap in effectiveness is the reason many spyware experts recommend that you run Addaware in conjunction with another product.
More problematic for Addaware was the fact that it failed to disable 33% of the spyware that it detected. This spyware remained operational after Addaware had finished its scan and removal process.
Other applications responded very sluggishly while scanning was being performed. This would not be as much of a problem if scans could be scheduled, but the current version supports only on-demand and startup scans. If you are running a laptop or a slow desktop, this is probably not the product for you because you will have to manually start Addaware (or have it auto-start when you boot up) and sit there while it finishes.
In our tests, Addaware did not trigger any false positives.
Quarantine
Certain common applications (such as the free Real Player) will not function properly without their embedded spyware. If you run Addaware (or any other spyware remover), you may find that these applications will no longer run. Fortunately, Addaware quarantines all spyware so that you can restore it later if necessary.
Other Options
As stated above, Addaware has made signficant improvements with the user interface. The options settings which were so hard to find in the previous version of Addaware, have now been clearly relocated to their own icon at the top of the form. They've even replaced many of the confusing nested options screens with simple interfaces that are easier to understand.
However, as with previous versions, the options offered are more suited to people who are very comfortable working with computers. For instance, because spyware scanning is time consuming, the most important option any spyware program could have is the ability to schedule scans when you are not around. Addaware lacks this basic and necessary functionality.
Instead, it offers a variety of infrequently used options. Do you want to place your log files in specific locations? Would you prefer to scan your registry, or deep scan it? How about your hosts file?
Summary
Lavasoft's Addaware SE is a huge improvement over previous versions in terms of usability, but still lags behind the top products in terms of sheer effectiveness. Lavasoft does offer a free Addaware download, however. It is a better product than most others on the market, but its lack of scheduling ability, average real-time monitoring, and complex user interface detract from its sheer power.
Purchase Price: $39.95
Free Trial: Yes
September 02, 2004
Ad-Aware SE Review
|
Product: Adaware SE Price: $39.95 Vendor: Lavasoft Editor Rating: 3 stars Adaware download |

|
Pros
+ Better spyware protection than most products
+ AdAware SE has an improved user interface over previous versions.
Cons
- Still a confusing user interface. Most of Adawares useful functionality is hidden from the average user.
- Cant schedule scans on-demand or boot-up scans only mean your computer will be unavailable while it checks for spyware.
- Poor customer support.
- Higher priced than other top rated solutions
AdAware Adware Remover Review
AdAware SE, the latest update to Lavasoft's flagship product, is a good product that provides decent protection against many spyware programs, but lacks some important functionality such as the ability to schedule scans. The user interface is difficult to use and might appeal more to people comfortable with computers.
It can detect spyware programs running in memory, examine startup settings, block browser hijackings, remove tracking cookies, and fix registry changes made by intruding programs. It can also remove stubborn spyware by flagging it for deletion (before it loads) during the next bootup cycle.
Our August test results indicated that AdAware protects against many common spyware programs, but not as effectively as our top rated products. However, Lavasoft does offer a free Ad Aware download.
AdAwares real-time monitoring (immunization) is not as effective as other products and was difficult to locate and configure. It does block browser hijackings, protect important registry settings, and block suspicious processes, and it even has functionality to scan for spyware in memory but this is very limited. During our tests, it did successfully detect in-process spyware, but it was unable to terminate the offending process.
Usability
Lavasoft has made significant improvements in the user interface with the latest version of Ad Aware. Many of the cryptic and non-working buttons (such as "ProcWatch") are gone, although some remain (such as the "Add-ons" button).
If youre a computer engineer and enjoy tinkering with background processes and log files, Ad-Aware exposes this sort of powerful functionality to you. On the other hand, if you are a regular computer user, you will likely become very frustrated by the complexity and awkwardness of this program.
Removal
Scanning with Ad-Aware was very fast completing in about 6 minutes on our Windows 2000 test PC. This was much faster than any other product we tested.
While Ad-Aware claims to detect more spyware programs than other vendors, in our tests it failed to find a number of unwanted browser plug-ins (such as the "Websearch toolbar") that other products correctly detected. In our more formal Spyware Effectiveness Test, AdAware missed 22% of common spyware. This gap in effectiveness is the reason many spyware experts recommend that you run AdAware in conjunction with another product.
More problematic for AdAware was the fact that it failed to disable 33% of the spyware that it detected. This spyware remained operational after Adaware had finished its scan and removal process.
Other applications responded very sluggishly while scanning was being performed. This would not be as much of a problem if scans could be scheduled, but the current version supports only on-demand and startup scans. If you are running a laptop or a slow desktop, this is probably not the product for you because you will have to manually start Ad-Aware (or have it auto-start when you boot up) and sit there while it finishes.
In our tests, Ad-Aware did not trigger any false positives.
Quarantine
Certain common applications (such as the free Real Player) will not function properly without their embedded spyware. If you run Ad-Aware (or any other spyware remover), you may find that these applications will no longer run. Fortunately, Ad-Aware quarantines all spyware so that you can restore it later if necessary.
Other Options
As stated above, AdAware has made signficant improvements with the user interface. The options settings which were so hard to find in the previous version of AdAware, have now been clearly relocated to their own icon at the top of the form. They've even replaced many of the confusing nested options screens with simple interfaces that are easier to understand.
However, as with previous versions, the options offered are more suited to people who are very comfortable working with computers. For instance, because spyware scanning is time consuming, the most important option any spyware program could have is the ability to schedule scans when you are not around. Ad-Aware lacks this basic and necessary functionality.
Instead, it offers a variety of infrequently used options. Do you want to place your log files in specific locations? Would you prefer to scan your registry, or deep scan it? How about your hosts file?
Summary
Lavasoft's Adaware SE is a huge improvement over previous versions in terms of usability, but still lags behind the top products in terms of sheer effectiveness. Lavasoft does offer a free AdAware download, however. It is a better product than most others on the market, but its lack of scheduling ability, average real-time monitoring, and complex user interface detract from its sheer power.
Purchase Price: $39.95
Free Trial: Yes
August 28, 2004
What is Spy ware?
spy ware has eclipsed viruses as the fastest growing online threat, infecting nearly 90% of Internet connected PCs. If you are like most internet users, chances are you are infected with not just one, but many, of these programs. Simply surfing the internet, reading email, downloading music or other files can infect your PC without you knowing it.
What is spy ware?
The term "spy ware" generically refers to software programs made by unscrupulous marketing companies that allow them to snoop on your browsing activity, see what you purchase, and cause pop-up ads to appear on your computer.
More specifically, Adware is any software program that causes advertising banners to be displayed to the user. spy ware is any software program that sends data back to a third party without asking you for permission.
Why are these programs a problem?
spy ware causes lots of problems on your PC without you ever suspecting it's there. Have you ever noticed that your computer runs a lot better when you first purchase it than it does months later? The most likely culprit is spy ware.
Why should I care?
spy ware ...
* Consumes resources on your PC
* Slows it down
* Causes it to crash
* Interferes with your web browser, slowing it down or causing downloads to fail. It can even hijack your browser, redirecting you and your children to sites with objectionable material
* Slows down your internet connection because while you are surfing, it is sending information about your surfing habits to ad companies, who then target you with popup ads that fit your preferences
* Costs you money - If you are paying for dialup internet access, spy ware is literally costing you money.
In short, while spy ware is typically not hazardous to your PC, it is annoying and unnecessary. It's the next generation of spam.
How did I get it?
spy ware can infect your system in many different ways: visiting a spy-spreading web site, opening a spy-carrying email attachment, downloading a spy as part of another (often "free") software program, etc. Your privacy, and even your identity, is at high risk if you surf the Internet more than one hour a week, share your computer or use file-sharing programs like KaZaa. Traditional anti-virus programs and firewalls don't offer protection from invasive and harmful spy ware programs that can manifest themselves in many ways on your PC.
What can I do?
If you're in a hurry, visit our review page to discover reputable products that will completely protect you against this threat.
Be careful! There are programs out there that claim to stop spy ware, but will actually install it on your PC and prevent anti-spy ware programs from operating correctly in the future.
Want to know more? Visit our resources page to learn about other sites that will teach you about spy ware and keep you informed.
Other spy ware Resources
August 24, 2004
CoolWebSearch Spyware
One of the most complex, sophisticated, and devious browser hijackers ever invented, CoolWebSearch (one word - "cool web search" is technically not correct) is the name given to a range of various browser hijackers. The latest versions have grown increasingly aggressive and complicated and manual removal is virtually impossible. Oftentimes, re-installation of the entire operating system is required, thus use of a reputable spyware remover is highly recommended. New variants of CoolWebSearch are released every few weeks, making it increasingly important to ensure that your spyware remover has the latest updates.
CoolWebSearch Symptoms
* Hijacks to various search engines. Different variants of CoolWebSearch will redirect you to different sites.
* When a URL is mistyped in the browser, CoolWebSearch will redirect the page to affiliate websites as well as CoolWebSearch.com.
* Installs bookmarks to adult websites in the favorites menu.
* Installs toolbars into the browser.
* Slows down PC.
* Can cause reboots.
* Targets anti-spyware websites, usually vendors of spyware removal tools. Once infected with CoolWebSearch, you may be unable to visit these websites to download their products.
* Will open porn popups if it thinks the website being viewed is pornographic in nature.
* Can cause significant slowdowns when attempting to type into a browser.
* Will add CoolWebSearch.com to the trusted sites list.
Removing CoolWebSearch
CoolWebSearch is very difficult to remove manually. The latest versions are virtually impossible to clean short of re-installing the operating system or restoring a previous version of the Windows registry, thus use of a good spyware remover product is recommended.
Unfortunately, most spyware removers will not work against Cool Web Search, so a niche spyware remover called CoolWebShredder is commonly used to destroy this parasite. However, this tool will no longer be updated after the current version (1.59), because the author (who volunteers his time) does not have the tools to remove the latest variants.
Past CoolWebSearch Variants
* CoolWebSearch/DataNotary hijacks to dataNotary.com and replaces the default stylesheet used by IE. This stylesheet includes javascript that actively watches the currently loaded page and tries to guess when the user is viewing porn sites.
* CoolWebSearch/BootConf Also replaces the CSS file, hijacks MSN search, and installs a program, bootconf.exe, that resets all hijacked settings every time the computer is restarted.
* CoolWebSearch/MSInfo Similar to the previous, but points to true-counter.com.
* CoolWebSearch/SvcHost This variant causes an error when the user attempts to access one of many well-known websites (such as Yahoo search). The error page is then hijacked and the user is sent to slawsearch.com.
* CoolWebSearch/DNSRelay This variant hijacks URLs that have been typed without a leading http:// or www to activexupdate.com.
Articles about CoolWebSearch
CoolWebSearch is winning the Trojan War
Nothing Cool about CoolWebSearch
CWShredder Software Gets Final Release
Summary
CoolWebSearch should be considered one of the top 10 worst spyware offenders.
August 16, 2004
Service restored at Aluria
I have finally gotten in touch with Aluria and have confirmed that everyone is safe and sound, which is the most important thing! People are a bit shaken up, but that's to be expected after a disaster of that magnitude.
On the spyware front, power has been restored to Aluria's website and service has resumed as usual.
August 15, 2004
SpyKiller Review
|
Product: SpyKiller 6.22 Price: $49.95 Company Info: Swanksoft Editor Rating: 1 star Download SpyKiller |
 Click for more info |
Cons
- High-pressure sales tactics, including use of false positives in their free scan
- Does not provide any details about the spyware it detects
- Very poor protection against spyware.
SpyKiller Review
SpyKiller is a barebones spyware removal tool that provides little more than the most basic detection functionality. It does not provide detailed scan results and so we werent able to conclusively determine its effectiveness. However, follow-up tests on clean PCs indicate that SpyKiller may be finding false positives in an effort to goad users into purchasing the product.
As of July 2004, Spy Killer claims to protect against 17,899 items.
Installation
SpyKiller installed without any problems on both of our test PCs. It loaded the latest spyware definitions immediately after starting the program for the first time.
Usability
SpyKillers user interface was simple, although nowhere near as attractive as other products. A large Scan Now! button made it very clear what we needed to do.
Scanning on our Windows 2000 test computer took 10 minutes, and nearly 45 minutes on our Windows XP machine. The majority of the time was spent deep scanning the registry, while relatively few actual files were scanned. This is surprising given that SpyKiller claims to protect against nearly 18,000 definitions. It is possible that SpyKiller is taking short-cuts which often leave a significant amount of spyware undetected.
Removal
SpyKiller initially appeared to be very promising. On our Windows XP machine (loaded with test spyware), Spy Killer claimed to have found 43 spyware processes running in memory (highly suspect as had only installed 30) and 10 spyware files on disk. Of the 30, it had correctly identified 10.
So to be sure, we decided to try SpyKiller on a brand new installation of Windows 2000. This time, SpyKiller claimed to find 45 spyware processes running in memory and again, 6 files on disk. We attempted to verify this with a fresh copy of Webroots Spy Sweeper (installed from CD) and found that the box was almost perfectly clean (with the exception of Microsofts harmless Alexa toolbar registry entry).
Given our second test on a clean PC, we are led to believe that Spy Killer is making use of false positives to spur people into buying their product. Buyer beware.
Rollback
SpyKiller does not allow rollback or quarantine. This feature is necessary in case you inadvertently remove a program that is not spyware (such as Quicktime). Without this feature, you may end up inadvertently breaking your other software and have no way to fix it.
Other Features
SpyKiller is missing a scheduler, which means you will not be able to schedule scans during off-hours, such as at night when you are away from the computer. Nor does it provide detailed scan results or information about the spyware it finds on your PC, very nice features which are included with our top picks.
Summary
While SpyKiller did detect some spyware in our tests, follow up tests on clean PCs indicate that it triggers false positives, possibly to pressure customers into purchasing the product or simply due to faulty programming. Given the uncertainty of the product as well as the high price, we suggest you look elsewhere.
Purchase Price: $49.95
Free Trial: No, but the company does offer free scanning to determine the extent of spyware on your computer.
Update on Aluria Software
While we haven't heard back from anyone at Aluria Software yet, the local news indicates that there was minimal damage in their county. It appears that their ISP has gone down as a result of widespread power failures in the area.
Progress Energy has already restored about 15% of the power and is working very quickly to complete repairs. It's anyone's guess as to when exactly their ISP will be up again, but it may be as soon as tonight or tomorrow.
August 14, 2004
Aluria website down due to Hurricane Charley
We are waiting for more news and will post it here as soon as we hear anything.
August 10, 2004
Spybot S&D stability problems
We receive a considerable amount of email challenging our claim that Spybot S&D has caused stability problems on our Windows XP test platform. Specifically, this program slowed Internet Explorer to a crawl, a problem we were able to fix by running another top spyware removal tool. A little research showed the other users weren't quite so lucky. From the looks of it, Spybot S&D has crashed more than a few PCs, some to the point where a complete re-install of the operating system was required.
And yet despite the frequency of these claims, nearly every report of Spybot S&D instability has been met with criticism, if not open hostility. Apparently, some people feel as strongly about Spybot S&D as others do to more traditional causes, such as religion or politics.
Update: After several months of just hearing about these problems, we saw it with our own eyes. The latest version of Spybot S&D rendered our server unusable after a scan. We were bombarded with popup error messages every few seconds ... a few from Spybot S&D, most from spyware programs which had been incorrectly disabled.

Screenshot of Spybot S&D crashing our server
So while we do stand by our test results, we don't ask that you take us on our word. One reader asked that we produce a list of internet links to reports of Spybot S&D causing computer and operating system crashes.
The following quotes are just a few that can be found through a casual Google search, with links included. None of the websites referred to below are associated in any way with Gooroo or Adware Report.
Adaware kept finding the same stuff and wouldn't remove all of it. Spybot S&D kept making my computer crash.
We no longer recommend SpyBot S&D. Version 1.3 has too many stability problems and frankly seriously wrecked some of our clients computers. We have used/recommended SpyBot for many years, until 1.3 came out. It the problems are addressed, we would probably recommend it again.
Apparently I don't know how to use Spybot S&D and Ad-aware properly. Using the to remove spyware has caused Windows to destablize and/or made it impossible to use some programs - inculding Spybot and Ad-aare so that I couldn't get back in to restore what had been removed.After running Ad-aware or Spybot none of the System Restore points were available even though there had been several before removing the spyware.
http://help.lockergnome.com/index.php?showtopic=22691
And here are a number of quotes from the CNET User Opinions page. This thread was particularly critical of Spybot S&D, with over 112 reports of Spybot S&D problems. Beyond tens of reports claiming that Spybot S&D has hung various operating systems are reports of false positives, overlooked spyware, permanent operating system crashes, and even allegations that Spybot S&D is installing spyware. While we are reluctant to believe all of these claims, there are enough reports in this thread alone to warrant caution against using this product.
"A good product gone bad" I have used SpyBot for a number of years. When this update became availabe, I quickly uninstalled the 1.2 and installed this one. I have run it three times and it has found the same 5 "DSO Exploits" and told me it removed them three times. I uninstalled and went back to the 1.2 which no longer has updates available and it removed the five files and found 4 more than 1.3 did not identify. I filed a bug report, but intill the product is fixed, stay with the 1.2, even with the outdated March updates or move onto a different program. Very disappointing as using Ad-Aware and Spybot has been my normal routine for a long time now. At this point, I have uninstalled Spybot completely since my 1.2 can't be updated any more."WARNING TO XP/ME USERS!!!!"
This is to warn all windows XP and ME owners NOT to use this new version. It tries to creat a system restore point when you first use it and then freezes up your computer!! You will then find that all your system restore points are screwed up and dont work. Only AFTER it tries to create a system restore point,and the program freezes, that a message comes up that says you can turn it off. This stinks!! The programmer shoot be SHOT for this terrible feature. They should spend more time trying to add more spyware detections then screwing up peoples good computers. And dont believe the bull they are doing this for FREE. LOL. And you must believe in the tooth fairy. Get real. This program has gone down the drain!!! And to believe CNET gave it five stars. What a joke. Guess CNET doesnt use XP or ME. So much for their credibility."beta software full of critical bugs- do not download"
I used 1.2 for quite a while (Together with Adaware) but will never reinstall 1.3 until the critical bugs have been fixed.This update installs something named "teatimer" which runs as a background process and freezes your entire system after 30 minutes running (happend on two of my three systems).There are also NO updates (for the definitions) for almost three months - so you run at high risk relying on Spybot.Malware that can seriously harm your system is released daily, so up-to date definitions are a MUST for this type of application.Spybots database is definitely outdated.It used to be a nice program, but with all the features not completely implemented this very much looks like a public-beta test.Serious bugs have not been addressed in 1.3(Spybot will break your internet connection when removing some spyware.I sent them a bug report explaining the issue but never got a response.In addition, this has been posted in their support forums by several users so they know about the problem), instead more features have been added (teatimer) which are not working as advertized.dont get me wrong, I donated for 1.2 (and know many who did),because I liked it and wanted to support the developement of the project.However, Spybot 1.3 should never have been publically released in its current state."DO NOT INSTALL THIS SOFTWARE!"
Im a 25 year IT executive with a Fortune 500 company. I have never posted here before, but feel compelled to write. I and many of my staff have personally used Mr. Kollas SpyBot S&D since the day of its inceptions and have been a major supporter of this excellent program until now. Based on our evaluation of SpyBot S&D ver1.3Final, I DO NOT recommend this software any longer, and it SHOULD NOT be installed or utilized. Further significant concerns have arisen as to the integrity of Mr. Kolla and his associates.http://earthlink.com.com/3302-8022_4-10289035.html?pn=1&fb=2
For a long time, I used both Ad-aware and Spybot. Tried the new version of Spybot and was quite disappointed. As fast as adware/malware evolves, the lack of updating is a problem. It also gave me a lot of false positives. Even claimed my own site had CoolWebSearch. They never replied when I e-mailed them about this. I just finished reformatting my system, (one too many "experiments") and didn't bother re-installing it. Ad-aware has handled the task quite nicely.I installed Spybot and after running it a time or so recived error message something like this: detected two changes, ignore or accept. I tried to delete the error message but couldn't. Tried clicking the ignore or the accept and one wouldn't let me move on and the other let me miove on but my computer was crashed bad. My DUN was deleted and I couldn't create another. I tried running System Restore but it wouldn't run. I ran Recovery Disk which re- installed all my software. Computer works ok now.
http://www.freedomlist.com/forum/viewtopic.php?p=120640
New spyware/malware programs are being released constantly. The latest variants include auto-updaters and "stealth" code that is growing in sophistication by the week. We recommend that if you are going to rely on a spyware removal program that is currently five months out of date, that you unplug your computer from the internet before using it.
August 09, 2004
Cydoor
Cydoor causes popup and pop-under ads to be displayed while you are browsing the internet. It also re-routes your web requests through third-party servers for the purpose of capturing your web surfing habits.
Cydoor can not be uninstalled using the Windows uninstaller and no uninstaller is provided.
Cydoor consumes about 3.4Mb of hard drive space.
Update - March 16, 2005
Cydoor responds:
I would like to bring your attention to your categorization of our ad-serving technology as spyware. I believe that this categorization is mistaken, and I would like to show you why. I would also like to request that you update your description of Cydoor to be a mild adware.In the past, Cydoors client was defined as Spyware by several members of the press and the anti-spyware industry. The client itself was mostly bundled with free software for the sole purpose of enabling that application to display ads. The client communicated with a Cydoor host periodically in order to present new ad creatives and to report on ad performance. Though no personally-identifying information was ever transferred, this method was considered invasive because users did not explicitly agree to install a Cydoor component or to the transmission of information.
However, today Cydoor has significantly changed its technology to offer end-users and partners an unobtrusive ad-serving solution. With a greater emphasis on visibility and privacy issues, Cydoor provides its partners with a reliable source of revenue, while making sure users are aware of its activities.
How does it work?
Cydoor provides all its publishers with a complete interactive advertising solution, including ad serving, frequency capping, and performance statistics. Cydoor allows each publisher to implement a solution that provides them with the advertising flexibility that they require, including any and all communication to Cydoors servers. Cydoor has no presence on the end-users desktop in any way, and our partners can serve ads and generate revenue from their application or web property.
Users download the desired application, while noting that it is ad-supported. Cydoor strongly urges all its partners to state upfront that their application is freeware but is supported by advertising revenue, and most state it in their End User License Agreement (EULA). There is no installation, explicit or otherwise, of any Cydoor component on the users computer.
After installation, the partner application manages the various advertisements and their performance. The ads are served according to predefined impression requirements and caps and exposure is not based on any aspect of the users behavior. From time to time the partner application connects to Cydoor's servers in order to report aggregated performance records such as which ads were displayed, how many impressions they received, and which, if any, did the user click on. These are the same kind of performance parameters that are tracked by any online advertiser, including banners published on a web site.
Id like to emphasize that the application does not download ANY information from the Cydoor servers aside from ad creative. The application reports only basic aggregated campaign performance parameters. Under no circumstance does the application report on any other user behavior or does it transmit any personally identifiable content.Id like you to note that as an example, two of our partners, Download Accelerator and PalTalk Instant Messenger are either certified as Spyware-Free or are working with the leading Anti-Spyware vendors to be removed from their Spyware list.
Please let me know if you need any additional information regarding my request.
NewDotNet
New.net is a company that sells alternate top-level domains not supported in the official DNS system, and publishes a spyware application that makes use of these domains. The Top-level domains new.net provides are: .shop, .xxx, .club, .ltd, .inc, .travel, .tech , .sport, .family, .law, .med, and .mp3.
The new.net application is an Internet Explorer plug-in that gives the appearance of providing extra top-level domains (.shop, .xxx and .mp3, for example). Unlike many spyware programs, it does not secretly collect information, and the latest versions no longer inflict unrequested pop-up ads on the user. It does, however, install itself without the knowledge or permission of the user, and is designed to generate revenue for the new.net company. It redirects search queries to the new.net search engine, and is classified as a security risk because the update component stealth downloads any code the new.net server instructs it to.
Several different versions of the software exist. Early versions installed themselves into the Windows directory as a DLL titled "newdotnet_(X)" (where "X" is a number) and had no uninstall option. More recent versions create a folder in Program Files. In 2002, new.net added an extra program to the standard stealth installer. This program, known as FirstLook, was a pop-up advertising downloader. After considerable user anger and bad publicity, the new.net company stopped including FirstLook in the product.
New.net is hidden within a large number of apparently harmless programs, including Audiogalaxy, Babylon, BearShare, Grokster, iMesh, KaZaA, Radlight, and RealPlayer.
The program functions by inserting itself into the Winsock system. In consequence, a new.net infection is a frequent cause of lost network connectivity. A typical symptom for dial-up systems is that the user is able to dial out normally but cannot access the Internet. Older version of new.net often caused Internet Explorer to crash from time to time. It is believed that the later versions do not suffer from this issue.
The functionality of this product does not adhere to most Internet standards.
Older versions of NewDotNet cause frequent browser problems and may also trigger pop-up ads on your PC.
Use of an automated spyware removal tool is highly recommended, as you may permanently disable your internet connection by uninstalling manually.
CommonName
CommonName is a browser hijacker that installs an unwanted toolbar into Internet Explorer which displays links to paid sponsors websites as well as a search textbox. It also searches for terms that you type into the Address bar or within selected search engines, such as msn, Yahoo, and AskJeeves, and then hijacks your request by directing you to a sponsored website. The company claims that over 22 million desktop computers are running their software.
CommonName markets their software by pointing out that simple search terms are easier to remember than complex URLS.
CommonName includes re-installation software that will attempt to defeat your efforts to remove it and is likely to slow down the performance of your browser.
This software consumes approximately 16Mb of hard drive space.
August 08, 2004
IGetNet
IGetNet is a browser hijacker that re-routes your web requests to MSN or Netscapes search engines through their servers. It examines your search terms and if youve typed in a search targeted to one of their advertisers, it will re-route your request to the advertisers site.
IGetNet is easily recognizable because it changes your IE address bar (which is usually blank) to read Enter Keyword or Web Address Here. In addition, if your type auto.search.msn.com, search.netscape.com, or ieautosearch in the Address field, you will be re-routed to http://www.igetnet.com.
IGetNet uses over 1Mb of your hard drive space.
Autosearch
Autosearch falls within the class of spyware known as homepage and browser hijackers. It installs an unwanted toolbar within Internet Explorer and can dramatically slow down your browser. Should you type in a web address incorrectly, Autosearch will redirect you to www.tunders.com. This site displays ads and is not a search engine.
Autosearch first appeared in January of 2004 and recognizes a number of other common browser hijackers, such as IGetNet, CommonName, and NewDotNet.
It consumes approximately 57k of storage space on your hard drive.
August 03, 2004
Pest Patrol 4.4
|
Product: Pest Patrol 4.4 Price: $39.95 Vendor: Computer Associates Editor Rating: 3 stars |
 Click for more info |
Pros
+ Good overall detection and spyware removal capabilities
+ Comes with additional spyware blocker programs that monitor memory and browser cookies.
Cons
- Confusing user interface
- Flagged legitimate software as spyware
- Lacks a built-in scheduler
Pest Patrol Review
We found Pest Patrol to be a good product with some annoyances. It is also priced more expensively than our other higher ranked products, which hurts its overall rating.
It can detect spyware running in memory, stop browser hijackings, examine your startup settings, remove tracking cookies, and eliminate registry changes made by intruding programs. Pest Patrol did not alert us when spyware was installing itself on our computer, but overall has good spyware removal capabilities.
Usability
At first, we found Pest Patrols user interface to be quite pleasing. But it quickly became confusing as we navigated through rows and rows of tabs and buttons. After just a few minutes of use, the program felt cluttered, and we wondered if anyone at Pest Patrol had thought about usability.
Pest Patrol comes with a few memory-resident spyware blocker programs that monitor your computers' memory and browser cookies. We found these programs to be ineffective and somewhat intrusive.
Spyware Removal
To run a scan, you have to first select a drive and then press the scan button. While simple enough for a skilled computer user, this process is not all that intuitive and will be very confusing to the novice.
Pest Patrol took about 20 minutes to do a full scan which was slightly faster than the higher rated products we tested. Pest Patrol performed a thorough scan on every file in our system and didnt take any shortcuts.
However, we uncovered a major problem with Pest Patrol. During our test scan, it flagged innocuous files used by a very popular file sharing application (such as jpgs, bmps, and text files). In all, it discovered 151 bogus traces including a winzip executable containing nothing but mp3s. We felt this was quite misleading and wondered if Pest Patrol is really as thorough as it claims to be.
Quarantine
Pest Patrol had a very annoying quirk here. We pressed the quarantine button only to receive a message that quarantining was no longer required and that delete was completely reversible. As with so many other software companies, it seems the people at Pest Patrol didn't really stop to think about usability.
Other Options
One feature that we really liked about Pest Patrol is the built-in library that had thorough and informative descriptions of most of the spyware programs we have ever encountered.
One feature we hated was the lack of a scheduler that would allow us to run scans at night when we are away from the office. We currently use another product for this, and each morning we are surprised to find up to a dozen new spyware traces on our computers from the previous day.
Most of the other built-in options that Pest Patrol has (such as a list of running processes or startup files) seemed to be last-minute additions to the product. These options made the user interface more confusing than it needs to be and should be removed, or at least hidden.
Support
The product does not include a help file. Instead, the help sends you to their website which contains a getting started section as well as a tutorial. The tutorial was confusing if you really need some hand holding to run this product, we feel youll find it a frustrating and tedious experience wading through the online documentation.
The company offers email and forum support. Email inquiries have up to a 24 hour turnaround time.
Summary
Pest Patrol is a good spyware blocker, although it is priced higher than our other top rated tools and lacks a scheduler so you can't scan while you're away from the computer. It has very good spyware removal capabilities, but because of its over-enthusiastic tendency to flag file sharing applications as spyware, we feel this may be a better choice for small business or corporate use.
Purchase Price: $39.95
Free Scan: Yes but it wont delete the spyware it finds.
July 07, 2004
WebThisWebThat Spyware
In the past month, a new form of adware has appeared that runs invisibly on your computer and modifies Yahoo and Google search results pages. This adware removes the #1 and #2 search results and replaces them with paid advertisements. The ads are nearly indistinguishable from regular Google search results ... the only difference being that they never have the "cached version" link available. Clicking on them leads you to a "search engine" that returns nothing but paid advertisements.
The name of this new spyware is "WebThisWebThat".
How to Get Rid of WebThisWebThat
We've done some research and found that it isn't so easy unless you are comfortable digging into your operating system internals. Here are a couple of good programs that get rid of this spyware:
Aluria Spyware Eliminator
Webroot Spy Sweeper
If you're a little braver, then deletion can be done manually with the following steps:
1. reboot into safe mode and delete the file called "cmcfg32.exe" which resides in your [windowsdir]\system32 folder.
2. Using a utility which allows you to modify your startup programs, remove cmcfg32 from the startup list.
3. Reboot your PC.
July 03, 2004
Are Cookies "Spyware"?
A number of readers and vendors have emailed us asking if cookies are really spyware. To get to the bottom of this, we spent some time talking with vendors and industry experts.
What Is A Cookie?
This excellent definition comes from GetNetWise.
A cookie is a piece of information sent by a Web server to a user's browser. Cookies may include information such as login or registration identification, user preferences, online "shopping cart" information, etc. The browser saves the information, and sends it back to the Web server whenever the browser returns to the Web site. The Web server may use the cookie to customize the display it sends to the user, or it may keep track of the different pages within the site that the user accesses. Browsers may be configured to alert the user when a cookie is being sent, or to refuse to accept cookies. Some sites, however, cannot be accessed unless the browser accepts cookies. (See also "Personally identifiable information")
Some advertisers use cookies to track your surfing habits while on their website, but it's important to note that unlike spyware, cookies can not be used to track your surfing on other websites. Nor do Cookies consume a noticeable amount of bandwidth.
Thus, cookies can't be considered spyware in the regular sense of the term.
Why Does This Matter?
Many vendors count cookies as a way of beefing up the total number of spyware programs they purportedly protect against. It seems harmless enough, but it does make it more difficult to judge how effective one product might be in comparison to another. When vendors begin counting cookies, it may be a sign that their products aren't as strong when it comes to protecting against actual spyware.
If this seems a little complicated for your tastes, don't despair - our updated July review will take cookie calculations into account!
June 22, 2004
Website update: Comments functionality removed
We turned off the ability for our readers to make comments on reviews tonight.
Although the vast majority of comments have been constructive, another unscrupulous review site felt it necessary to spam us. Although we won't dignify the website by naming them, they are a very well-known and highly advertised site. We will mention that this site doesn't even look at the vast majority of the software that they claim to "review", a fact that inspired us to create Gooroo reviews.
Rest assured that the Gooroo team does install every product we review on our bed of test computers and that our staff typically spends two to four hours on each product so that we can present you with screenshots, support and documentation surveys, and objective statistics. In short, everything that you need to make an informed decision and avoid scams.
We apologize that we are no longer able to provide our readers with the ability to make comments. If you have pressing information that you would like to see posted on the site, please email it to us at using the contact button above.
June 06, 2004
Opensite Spyware
Opensite is one of the latest new adware programs to hit the internet. It displays advertisements based on keywords in the address bar, and it may also change the default home page in Internet Explorer.
Opensite has been associated with operating system freezes on Windows 2000.
Publisher: zuvio.com
Click on "Continue Reading" to read the terms of service.
Terms of Service
When using Zuvio, Page Access, and/or Open Site you agree to the following terms and conditions (the "Terms of Service"). You can always check out the most current version of these Terms of Service at this page. In addition, when using particular Zuvio services, you shall be subject to any posted guidelines applicable to such services, including the any applicable sweepstakes rules and any terms or conditions applicable to Zuvio services provided in conjunction with any of Zuvio's content and service partners. All such rules and guidelines are hereby incorporated by reference into the Terms of Service. If you do not agree to these Terms of Service please do not use the site and do not register to be a member of Zuvio. We reserve the right, at our discretion, to change, modify, add, or remove portions of these Terms of Service at any time. Please check these terms periodically for changes. Your continued use of the Zuvio Service following the posting of changes to these terms (including Zuvio's Forum Guidelines) will mean you accept those changes.
Overview
Zuvio is a multi-purpose service which allows you to use or access a wealth of products and services, including e-mail, software, search services, chat rooms and bulletin boards, shopping services, news, financial information and broad range of other content (collectively the "Zuvio Service"). These Terms of Service apply to the Zuvio Service as well as any new products or services that we may add in the future (unless stated otherwise).
General Terms of Service and Restrictions on Use of Materials
By using the Zuvio Service, you agree to be legally bound and to abide by the Terms of Service, just as if you had signed this Agreement. If you do not comply with the Terms of Service at any time, Zuvio reserves the right to terminate your access the Zuvio Service. Zuvio may discontinue or alter any aspect of the Zuvio Service, including, but not limited to, (i) restricting the time the Zuvio Service is available, (ii) restricting the amount of use permitted, and (iii) restricting or terminating any user's right to use the Zuvio Service, at Zuvio's sole discretion and without prior notice or liability. You are responsible for all charges associated with connecting to the Zuvio Service through an available access number. You are also responsible for obtaining or providing all access lines, telephone and computer equipment (including modem), or other device, necessary to access the Zuvio Service. You further certify that you are an individual.
In order to permit Zuvio to protect the quality of its products and services, you hereby consent to Zuvio employees being able to access your account and records on a case by case basis to investigate complaints or other allegations or abuse.
You acknowledge that the Zuvio Service contains information, software, photos, video, text, graphics, music, sounds or other material (collectively, "Content") that are protected by copyrights, patents, trademarks, trade secrets or other proprietary rights, and that these rights are valid and protected in all forms, media and technologies existing now or here after developed. All Content is copyrighted as a collective work under the U.S. copyright laws, and Zuvio owns a copyright in the selection, coordination, arrangement and enhancement of such Content. The Zuvio name and logo are exclusively licensed to the Zuvio Network, Inc. All other trademarks appearing on the Zuvio Service are trademarks of their respective owners. Zuvio's partners may also have additional proprietary rights in the content which they make available through the Zuvio service. You may not modify, publish, transmit, participate in the transfer or sale, create derivative works, or in any way exploit, any of the Content, in whole or in part, except that you may download one copy of the materials on any single computer for your personal, non-commercial home use only, provided you keep intact all copyright and other proprietary notices. Modification of the materials or use of the materials for any other purpose, including use of any such material on any other web site or networked computer environment is strictly prohibited. In the event you download software provided by Zuvio, the software, including any files, images incorporated in or generated by the software, and data accompanying the software (collectively, the "Software") are licensed to you by Zuvio. Zuvio does not transfer title to the Software to you. You may not redistribute, sell, decompile, reverse engineer, disassemble, or otherwise reduce the Software to a human-readable form.
Registration
If you elect to register to use the Zuvio Service and/or participate in any sweepstakes, contest, or other services offered by Zuvio you agree to: (a) provide true, accurate, current and complete information about yourself as prompted by the Zuvio Service's registration form (such information being the "Registration Data") and (b) maintain and promptly update the Registration Data to keep it accurate. If you provide any information that is untrue, inaccurate, or incomplete, or Zuvio has reasonable grounds to suspect that such is the case, Zuvio has the right to suspend or terminate your account and refuse any and all current or future use of the Zuvio Service (or any portion thereof).
Zuvio's Privacy Policy
Pursuant to Zuvio's privacy policy, we may disclose to third parties certain information contained in your Registration Data or related data unless you choose to opt out from such disclosures or in the good faith belief that such action is reasonably necessary to comply with the law, legal process, or to enforce the Terms of Service. For more information, please see our full Privacy Policy.
Open Site & Page Access Software
If you elect to download and install Open Site and/or Page Access software your homepage may be changed to the Zuvio service. The Open Site software will serve you targeted advertising based on websites you may be viewing. Your privacy is important to us and no data is ever sent back on the habits of our users. All the data from the software is stored locally on your computer to have the software better serve you. To delete Open Site software simply go to Control Panel->Add/Remove Programs and select to remove Open Site. To change your homepage back simply select Tools->Internet Options and change the value in the homepage field to whatever you would like your homepage to be.
Community Standards and Conduct in Zuvio Forums
You acknowledge that all Content, whether publicly posted or privately transmitted, is the sole responsibility of the person from which such Content originated. This means that you are entirely responsible for all Content that you post, email or otherwise transmit via the Zuvio Service. Zuvio does not control all of the Content posted via the Zuvio Service and, as such, does not guarantee the accuracy, integrity or quality of such Content. You understand that by using the Zuvio Service, you may be exposed to Content that is offensive, indecent or objectionable. Under no circumstances will Zuvio be liable in any way for any Content, including, but not limited to, for any errors or omissions in any Content, or for any loss or damage of any kind incurred as a result of the use of any Content posted, emailed or otherwise transmitted via the Zuvio Service.
You agree to not use the Zuvio Service (including the Zuvio Forums described below) to:
upload, post, email or otherwise transmit any Content that is unlawful, harmful, threatening, abusive, harassing, tortuous, defamatory, vulgar, obscene, libelous, invasive of another's privacy, hateful, or racially, ethnically or otherwise objectionable;
harm minors in any way;
impersonate any person or entity, including, but not limited to, a Zuvio official, forum leader, guide or host, or falsely state or otherwise misrepresent your affiliation with a person or entity;
forge headers or otherwise manipulate identifiers in order to disguise the origin of any Content transmitted through the Service;
upload, post, email or otherwise transmit any Content that you do not have a right to transmit under any law or under contractual or fiduciary relationships (such as inside information, proprietary and confidential information learned or disclosed as part of employment relationships or under nondisclosure agreements);
upload, post, email or otherwise transmit any Content that infringes any patent, trademark, trade secret, copyright or other proprietary rights of any party;
upload, post, email or otherwise transmit any unsolicited or unauthorized advertising, promotional materials, "junk mail," "spam," "chain letters," "pyramid schemes," or any other form of solicitation, except in those areas that are designated for such purpose;
upload, post, email or otherwise transmit any material that contains software viruses or any other computer code, files or programs designed to interrupt, destroy or limit the functionality of any computer software or hardware or telecommunications equipment;
disrupt the normal flow of dialogue, cause a screen to "scroll" faster than other users of the Zuvio Service or an Zuvio Forum are able to type, or otherwise act in a manner that negatively affects other users' ability to engage in real time exchanges;
interfere with or disrupt the Zuvio Service or servers or networks connected to the Zuvio Service, or disobey any requirements, procedures, policies or regulations of networks connected to the Zuvio Service;
intentionally or unintentionally violate any applicable local, state, national or international law, including, but not limited to, regulations promulgated by the U.S. Securities and Exchange Commission, any rules of any national or other securities exchange, including, without limitation, the California Stock Exchange, the American Stock Exchange or the NASDAQ, and any regulations having the force of law;
"stalk" or otherwise harass another member or user of the Zuvio Service; or
collect or store personal data about other users, or members.
A "Forum" refers to a chat area, bulletin board, "instant messaging" or virtual community offered as part of the Zuvio Service. Zuvio also provides its users with access to e-mail. The Forums and e-mail shall be used only in a noncommercial manner. You shall not, without Zuvio's express written approval, distribute or otherwise publish any material containing any solicitation of funds, promotion, advertising, or solicitation for goods or services.
It is our policy to respect the privacy of all users. Therefore, in addition to our Privacy Policy, we will not monitor, edit, or disclose the contents of a user or member e-mail unless required in the course of normal maintenance of Zuvio Service and its systems or unless required to do so by law or in the good-faith belief that such action is necessary to: (1) comply with the law or comply with legal process served on Zuvio; (2) protect and defend the rights or property of Zuvio; or (3) act in an emergency to protect the personal safety of our users or the public. You shall remain solely responsible for the content of your messages.
All Zuvio Forum communications, including chat and bulletin board communications are public and not private communications. Although Zuvio reserves the right to remove without notice any Forum posting for any reason, we have no obligation to delete content that you may find objectionable or offensive. By uploading materials to any Forum or submitting any materials to us, you automatically grant (or warrant that the owner of such materials has expressly granted) us a perpetual, royalty-free, irrevocable, non- exclusive right and license to use, reproduce, modify, adapt, publish, translate, create derivative works from and distribute such materials or incorporate such materials into any form, medium, or technology now known or later developed throughout the universe. In addition, you warrant that all so-called "moral rights" in those materials have been waived.
Your privilege to use the Zuvio Forums and contribute to discussions on the Zuvio Forums depends on your compliance with the member conduct guidelines set forth above. Zuvio may revoke your registration privileges and/or take any other appropriate measures to enforce these guidelines if violations are brought to our attention. Further, Zuvio, in its sole discretion, may terminate your membership or participation in any community, chat room or other Forum for any reason.
Parental permission is required for children 12 years of age or under to use any Zuvio Forums. Please remember, when using any Zuvio services or Forums, you agree to abide by the member conduct guidelines set forth above. Zuvio does not permit registered users under the age of 13 to participate in chat.
Zuvio reserves the right to monitor some, all, or no areas of Zuvio Forums for adherence to these or other rules that may be published from time to time. You acknowledge that by providing you with the ability to distribute your content, Zuvio is acting as a passive conduit for such distribution and Zuvio is not undertaking any obligation or liability relating to any content or activities in any Forum or Forum area.
Submissions
By posting or submitting content to this site, you grant Zuvio and its affiliates and licensees the right to use, reproduce, display, perform, adapt, modify, distribute, have distributed, and promote the content in any form, anywhere and for any purpose; and warrant and represent that you own or otherwise control all of the rights to the content and that public posting and use of your content by Zuvio will not infringe or violate the rights of any third party.
If you send us creative suggestions, ideas, notes, drawings, or other information (collectively, the "Submissions"), the Submissions shall be deemed, and shall remain, the property of Zuvio. None of the Submissions shall be subject to any obligation of confidence on the part of Zuvio, and Zuvio shall not be liable for any use or disclosure of any Submissions. Without limitation of the foregoing, Zuvio shall exclusively own all now known or hereafter existing rights to the Submissions of every kind and nature throughout the universe and shall be entitled to unrestricted use of the Submissions for any purpose whatsoever, commercial or otherwise, without compensation to the provider of the Submissions.
Links
The Zuvio Service may provide, or third parties may provide, links to other World Wide Web sites or resources. Because Zuvio has no control over such sites and resources, you acknowledge and agree that Zuvio is not responsible for the availability of such external sites or resources, and does not endorse and is not responsible or liable for any Content, advertising, products, or other materials on or available from such sites or resources. You further acknowledge and agree that Zuvio shall not be responsible or liable, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with use of or reliance on any such Content, goods or services available on or through any such site or resource.
DISCLAIMER
Zuvio uses diligent efforts to maintain the Zuvio Service, but Zuvio is not responsible for any defects or failures associated with the Zuvio Service or any damages (such as lost profits or other consequential damages) that may result from any such defects or failures. In addition, Zuvio makes no guarantees as to the sites and information located worldwide throughout the Internet to which you may access as a result of the use of the Zuvio Service, including as to: (i) the accuracy, currency, content, or quality of any such sites and information, or (ii) whether any search using the Zuvio Service may locate unintended and objectionable content.
PLEASE NOTE THE FOLLOWING IMPORTANT DISCLAIMERS OF WARRANTIES:
THE Zuvio SERVICE IS PROVIDED 'AS IS' AND YOU USE IT AT YOUR SOLE RISK Zuvio EXPRESSLY DISCLAIMS ALL WARRANTIES OF ANY KIND, WHETHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT.
WITHOUT LIMITATION, Zuvio MAKES NO WARRANTY THAT THE Zuvio SERVICE WILL MEET YOUR REQUIREMENTS, THAT IT WILL BE UNINTERRUPTED, TIMELY, SECURE, OR ERROR-FREE, THAT THE RESULTS OBTAINED FROM THE USE OF THE Zuvio SERVICE WILL BE ACCURATE OR RELIABLE, OR THAT THE QUALITY OF ANY PRODUCTS, SERVICES, INFORMATION, OR OTHER MATERIAL OBTAINED THROUGH THE Zuvio SERVICE WILL MEET YOUR EXPECTATIONS.
ANY MATERIAL DOWNLOADED OR OTHERWISE OBTAINED THROUGH THE USE OF THE Zuvio SERVICE IS DONE AT YOUR SOLE RISK AND YOU WILL BE SOLELY RESPONSIBLE FOR ANY DAMAGE TO YOUR COMPUTER SYSTEM OR LOSS OF DATA THAT RESULTS FROM THE DOWNLOAD OF ANY SUCH MATERIAL.
FURTHER, PLEASE NOTE THAT NO ADVICE OR INFORMATION, OBTAINED BY YOU FROM Zuvio PERSONNEL OR THROUGH THE Zuvio SERVICE SHALL CREATE ANY WARRANTY NOT EXPRESSLY PROVICED FOR IN THESE TERMS OF SERVICE.
Disclaimer Regarding Financial Information
The Zuvio Service allows you to obtain information on companies, stock prices, bonds, and other investments or financial matters. The Zuvio Service, including all such financial information, is provided for informational purposes only, and no information you may obtain is intended by Zuvio to be used for trading or investing purposes. Zuvio shall not be responsible for the accuracy, usefulness or availability of any information transmitted via the Zuvio Service, and shall not be liable for any trading or investment decisions made based on such information.
Disclaimer Regarding Shopping Retailers
The Zuvio Service provides shopping services to help you locate and potentially purchase products from online and offline retailers. Zuvio does not, however, control these independent retailers and Zuvio does not provide any assurance, warranty or guarantee of any kind that you will be satisfied with their products or services. When shopping by means of services provided by Zuvio you acknowledge and agree that: Zuvio does not endorse any of the products or services ("Merchandise") linked to from or through the Zuvio Service, nor has Zuvio taken any steps to confirm the accuracy or reliability of any of the information provided by third parties through Zuvio or their own web sites. Zuvio expressly disclaims any and all representations or warranties as to the security of any information (including, without limitation, credit card and other personal information) you might be requested to give any third party. We advise you to exercise your own judgment and investigate as you deem necessary before proceeding with any online or offline transaction with any of these third parties.
Limitation of Liability
YOU EXPRESSLY UNDERSTAND AND AGREE THAT Zuvio SHALL NOT BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, CONSEQUENTIAL OR EXEMPLARY DAMAGES, INCLUDING BUT NOT LIMITED TO, DAMAGES FOR LOSS OF PROFITS, GOODWILL, USE, DATA OR OTHER INTANGIBLE LOSSES (EVEN IF Zuvio HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES), RESULTING FROM: (i) THE USE OR THE INABILITY TO USE THE Zuvio SERVICE AND/OR PARTICIPATE IN ANY SWEEPSTAKES ; (ii) THE COST OF PROCUREMENT OF SUBSTITUTE GOODS AND SERVICES RESULTING FROM ANY GOODS, DATA, INFORMATION OR SERVICES PURCHASED OR OBTAINED OR MESSAGES RECEIVED OR TRANSACTIONS ENTERED INTO THROUGH OR FROM THE Zuvio SERVICE; (iii) UNAUTHORIZED ACCESS TO OR ALTERATION OF YOUR TRANSMISSIONS OR DATA; (iv) STATEMENTS OR CONDUCT OF ANY THIRD PARTY ON THE Zuvio SERVICE; OR (v) ANY OTHER MATTER RELATING TO THE Zuvio SERVICE OR OPERATION OF THE Zuvio SWEEPSTAKES. IN NO EVENT SHALL Zuvio.S TOTAL LIABILITY TO YOU FOR ALL DAMAGES, LOSSES, AND CAUSES OF ACTION (WHETHER IN CONTRACT, TORT (INCLUDING, BUT NOT LIMITED TO, NEGLIGENCE), OR OTHERWISE EXCEED THE AMOUNT PAID BY YOU, IF ANY, FOR ACCESSING THIS SITE.
SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF CERTAIN WARRANTIES OR THE LIMITATION OR EXCLUSION OF LIABILITY FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES. ACCORDINGLY, SOME OF THE ABOVE LIMITATIONS MAY NOT APPLY TO YOU.
Indemnification
YOU ARE ENTIRELY RESPONSIBLE FOR MAINTAINING THE CONFIDENTIALITY OF YOUR PASSWORD AND ACCOUNT. FURTHERMORE, YOU ARE ENTIRELY RESPONSIBLE FOR ANY AND ALL ACTIVITIES WHICH OCCUR UNDER YOUR ACCOUNT. YOU AGREE TO INDEMNIFY, DEFEND AND HOLD HARMLESS Zuvio INC., CBS CORPORATION, THEIR PARENTS, AFFILIATES AND SUBSIDIARY COMPANIES, OFFICERS, DIRECTORS, EMPLOYEES, CONSULTANTS AND AGENTS FROM ANY AND ALL THIRD PARTY CLAIMS, LIABILITY, DAMAGES AND/OR COSTS (INCLUDING, BUT NOT LIMITED TO, ATTORNEYS FEES) ARISING FROM YOUR USE OF OUR SERVICES, YOUR VIOLATION OF THE TERMS OF SERVICE OR YOUR INFRINGEMENT, OR INFRINGEMENT BY ANY OTHER USER OF YOUR ACCOUNT, OF ANY INTELLECTUAL PROPERTY OR OTHER RIGHT OF ANY PERSON OR ENTITY. YOU AGREE TO IMMEDIATELY NOTIFY Zuvio OF ANY UNAUTHORIZED USE OF YOUR ACCOUNT OR ANY OTHER BREACH OF SECURITY KNOWN TO YOU.
Termination and modification
You agree that Zuvio, in its sole discretion, may terminate your password, account (or any part thereof) or use of the Zuvio Service, and remove and discard any Content within the Zuvio Service, for any reason, including, without limitation, for lack of use or if Zuvio believes that you have violated or acted inconsistently with the letter or spirit of the Terms of Service. Zuvio may also in its sole discretion and at any time discontinue providing the Zuvio Service, or any part thereof, with or without notice. You agree that any termination of your access to the Zuvio Service under any provision of this Terms of Service may be effected without prior notice, and acknowledge and agree that Zuvio may immediately deactivate or delete your account and all related information and files in your account and/or bar any further access to such files or the Zuvio Service. Further, you agree that Zuvio shall not be liable to you or any third-party for any termination of your access to the Zuvio Service.
Governing Law and Other Miscellaneous Terms
These terms shall be governed by and construed in accordance with the laws of the State of California, without giving effect to any principles of conflicts of law. You agree that any action at law or in equity arising out of or relating to these terms shall be filed only in the state or federal courts located in Los Angeles County in the State of California and you hereby consent and submit to the personal jurisdiction of such courts for the purposes of litigating any such action. If any provision of these terms shall be unlawful, void, or for any reason unenforceable, then that provision shall be deemed severable from these terms and shall not affect the validity and enforceability of any remaining provisions. This is the entire agreement between you and Zuvio relating to the subject matter herein and shall not be modified by you except in writing, signed by both parties. The Terms of Service will inure to the benefit of Zuvio's successors, assigns and licensees.
COPYRIGHT AND COPYRIGHT NOTICES
Zuvio respects the intellectual property of others, and we ask our users to do the same. Zuvio may, in appropriate circumstances and at its discretion, terminate the accounts of users who infringe the intellectual property rights of others. If you believe that your work has been copied in a way that constitutes copyright infringement, please provide Zuvio's Copyright Agent the following information:
an electronic or physical signature of the person authorized to act on behalf of the owner of the copyright interest;
a description of the copyrighted work that you claim has been infringed;
a description of where the material that you claim is infringing is located on the site;
your address, telephone number, and email address;
a statement by you that you have a good faith belief that the disputed use is not authorized by the copyright owner, its agent, or the law;
a statement by you, made under penalty of perjury, that the above information in your Notice is accurate and that you are the copyright owner or authorized to act on the copyright owner's behalf.
Please contact Zuvio's Copyright Agent for Notice of claims of copyright infringement on:
Zuvio.com
19360 Rinaldi St. #304
Granada Hills, CA 91344
[email protected]
June 02, 2004
Yahoo Spyware Toolbar
Yahoo recently unveiled a feature for its web browser toolbar aimed at making it easier for users to remove unwanted "spyware" programs that snoop on Web surfing habits and other activities.
But before you jump to the conclusion that commercial spyware products are doomed, consider this. Yahoo left out detection for adware, because its paid search division has a financial stake.
This strategy is reminiscent of other adware companies, like hotbar, who offer free software in exchange for some seemingly-innocuous feature. Often, you end up making a deal with the devil.
I'll stick to commercial spyware removers, thanks. At least you know what you're paying for.
Read more about issues in the software industry at StartupSkills.
Read more details about Yahoo's anti-spyware toolbar at Nathan's homepage.
June 01, 2004
ParetoLogic XoftSpy 3.2
Product: XoftSpy 3.2
Price: $39.95
Vendor: ParetoLogic
Editor Rating: 2 stars
Pros
+ Faster than other products we've tested
+ Simple, easy-to-use, and uncluttered interface
Cons
- Coverage not as effective as other products
- Light on additional features, such as ability to schedule scans during off hours.
Review
ParetoLogics spyware removal product, XoftSpy, provides moderate coverage at a higher price. The user interface is well laid-out, but a bit plain in appearance. The current version of XoftSpy lacks important functionality, such as the ability to schedule scans during off hours, and it couldnt detect a very wide range of spyware phenomena such as browser hijackings or spyware installations in progress.
Usability
XoftSpys user interface is basically well laid-out, although a bit plain and not particularly attractive.
On the plus side, it is simple and to-the-point; some of the other products we reviewed had cluttered or even incomprehensible user interfaces. XoftSpy has only four buttons: Stop, Backup, Remove, and Update. We felt this was appropriate as most people don't want to spend a lot of time tinkering with their spyware remover.
However, the interface has a couple of annoying quirks. First, the progress bar doesnt accurately indicate how much time remains during the scan. Instead, it cycles from 0 to 100 and starts over. Another thing we didnt like was that the primary window is non-resizable. We use a high-resolution monitor and we found that the columns in the scanning results grid were sized too small, causing the columns of text to mash into one another.
Removal
We performed a test scan on two heavily infected PCs (Windows XP and Windows 2000 Pro). XoftSpy was very fast, taking only 6 minutes, and unlike other products, did a full scan of the hard drive. However, we were unable to determine exactly how many spyware programs XoftSpy protects against, so it is unclear if the speed of the program was at the expense of coverage or due to superior scanning technology.
We are inclined to believe the former though. XoftSpy failed to fully detect and/or remove a number of common spyware programs. For instance, we installed hotbar while XoftSpy was loaded. It did not detect the installation in progress, nor did it detect it when running in memory (which was very annoying, as immediately upon installation, we were greeted with three unwanted popup ads).
After we ran a scan, it did detect hotbar but only partially. It found the registry keys as well as a hotbar log file, but it did not remove the program itself. The test PC continued to suffer from browser popups after we attempted to remove the offending spyware. In comparison, both of our top rated products (Aluria Spyware Eliminator and Webroots Spy Sweeper both successfully detected and completely removed hotbar, including all registry settings and associated .dll's).
Another feature we would like to see in XoftSpy is a full description of the spyware it finds. Although it lacks this functionality, it does at least give a relative indicator of danger (Annoying, Dangerous, etc)
Quarantine
XoftSpy offers a backup option. It was unique in that it allows you to compress all files removed into a zip file. This not only saves space, but also can prevent quarantined spyware from tripping up other spyware removal programs. It does this at the cost of an extra few clicks, something which can be annoying if you run spyware scans on a daily basis, as we do.
Other Options
XoftSpy offers only the most basic options, such as allowing you to select which drives to scan. It lacks a scheduler, which is a major strike against it. Also, updates of the spyware definition file must be performed manually, and the program will not alert you when a new update is available.
Summary
XoftSpy has been incorrectly labeled as rogue software. Our tests indicate that XoftSpy does not install spyware, adware, or other malware on your PC, nor does it appear that theyve appropriated freeware source code. However, it does not appear to offer comparable protection to other products weve tested and it has a higher price point.
Vendor: XoftSpy
Free Trial: No, but will perform a free scan.
Follow-up: XoftSpy - rogue or reputable?
This weekend we were contacted by the principals at ParetoLogic, makers of XoftSpy and asked to reconsider categorization of XoftSpy as a "rogue" product.
Essentially, ParetoLogic's side of the story is this:
1. They released the first version of their software earlier this year. The software had some bugs, as all new software does.
2. They partnered with ClickBank to handle their affiliate program. Soon after, thousands of websites began promoting XoftSpy, sometimes making outrageous claims about its efficacy.
3. The exploding popularity of the product outpaced their ability to correct the initial bugs, and as a consequence many internet reviewers bashed the software.
4. They have been hard at work fixing the bugs, and they are reviewing the quality of their affiliates to ensure that they are adhering to ethical business practices.
In their words,
We welcome all suggestions for improvement, and we will constantly work to make XoftSpy better, and ideally a product respected and recommended between programmers, developers, software companies and among other industry experts. If you think of something that we could improve, then please just send us an email. You will be impressed with the response, and if at all possible you will see the changes take form. Resorting to misinformed bashing is a tough way to appreciate life. Why not help us and others make a real difference for consumers instead. Send us your suggestions, send us your thoughts. We will make changes and improvements happen. Then decide for yourself if these Internet rants and accusations have substance.
We here at Adware Report agree with this sentiment. Because of ParetoLogic's attention and concern about this matter, we are removing them from our "rogue" list and will subject the software to a full review.
The full text of ParetoLogic's reply follows...
ParetoLogic was formed in early 2004 by several software development and marketing professionals. At the end of March our first product was launched. As of this writing, Our Trademarks are new. We will be aggressively defending all legal claims to our product and corporate identities.
Thank you for posting the URLs referencing our company. If deemed necessary, we will have our legal counsel investigate these sites and several others we have identified.
Thanks for your prompt reply to our concerns, as we also take these issues seriously. With regard to matters concerning trademarks, many companies pursue legal action first and let the courts determine the outcome. We however, prefer a more personal and hopefully amiable solution.
We do have an 'alternate resolution'. We do not fit your definition of rogue software, and we would simply like you to not list xoftspy in such a category. Its that simple.
Your website "adwarereport.com" looks great and is very professional. This is surely evidence of a talented and knowledgeable webmaster. ParetoLogic, as you know, has received web references that are not flattering. We have not addressed these accusations until now. :) Feel free to repost this email or any part thereof, on your internet properties as you see fit.
We would ask webmasters, to actually try out the software themselves. Few posters and webmasters have done this. The posts are simply an amalgamation of forum reposts. Those who have tested our initial release unfortunately have not likely followed up and tried any of the updated versions along the way. Ideally it would be nice if posters formed their own opinions rather than piggyback on the musings of another, and then jump to inaccurate and sometimes ridiculous conclusions. Certainly more convenient than standing apart from others. We have found a couple of posters that supported the product, and had good things to say about a new contender in a market amuck with pretenders. Then we read on and saw how these people themselves became the targets.
We would like our newly updated products identity to be recognized on various media by its effectiveness and overall performance, not by inaccurate assumptions, false assertions and replicated postings of many who have not even tried our constantly updated and improved software. We employ a skilled staff that takes pride in their work and marvels in the satisfaction of our customers. This contentment is dually shared by many of our customers themselves, as we are receiving much praise from registered users, a constant stream of referrals worldwide and a growing institutional client base.
ParetoLogic launched XoftSpy with a huge affiliate marketing effort right from day one. We now feel that this may have been an inappropriate venue for marketing a fresh new threat removal technology in such a high profile industry. Clickbank, an independent affiliate network, was used to enhance the marketing base for the product. Dozens of affiliates embraced XoftSpy and thousands of ads began to appear all over the Internet. It was in this process that XoftSpy was presented to the public as a quick cure-all for every conceivable computer malady. We are currently reviewing the XoftSpy affiliate marketing plan, and will be making a number of changes. This will include stringent guidelines and mandatory adherence to our code of ethical and acceptable practices. Early in the product marketing cycle of XoftSpy, a few undetected programming glitches were identified by our users. Our user base exploded quickly with the large affiliate exposure from Clickbank. These glitches were thereby amplified as compared to other products with a more modest sales cycle and a more moderate growth in number of users. The ParetoLogic support staff replied to these user concerns quickly and often in great detail, assuring XoftSpy users that our programmers were diligently searching for the most reliable and effective solution. The latest XoftSpy release is 3.2.08, and is available to users on the site at paretologic.com. Our definition reference file is currently #12. We have updated our definitions often since product release just a few months ago. We believe this new edition has addressed concerns mentioned on our support forum and on various websites. Here is a list of cited concerns and ParetoLogic Inc. comments:
ParetoLogic domain is registered to a Proxy Account
----------------------------------------------------
The founders of ParetoLogic desire to retain a degree of privacy for perfectly legitimate reasons. First of all, our directors, management, support staff and all employees are given the luxury of being able to work from home. This affords us the advantage of being able to hire exceptional people from any corner of the world, and gives us the ability to protect our families from any internet spawned imposition on our privacy. We are parents and grandparents, and we have children too! While we operate independently from our homes in various locales and countries, we dont wish to have our personal addresses posted across multiple sites for all to see.
Identifying non-existent items
----------------------------------------------------
Our users have informed us of threats identified that do not actually exist. Two such items were Coolwebsearch.svinit. and MSconnect dialer. The XoftSpy engine is more advanced than simply matching items in a definition file. We use a definition file system in conjunction with a more advanced detection system. XoftSpy is programmed with characteristics and traits that are typically associated with known specific threats and threat types. Using a programming algorithm of this type is advantageous because pests are able to be identified quickly before causing problems and without manual intervention. On the other hand, sometimes items are incorrectly categorized or identified. We are not sure if this is what is referred to as a 'false positive' however if this term describes the identification of an item incorrectly, as we've described, then this could be the case, and would also be the case in the development and marketing cycle of any other software product. We have responded to every single issue relayed to us by XoftSpy users and have diligently sought to quickly and effectively correct these errors. Sometimes this includes slight modification of the detection algorithm. Other times it includes a simple file modification. We have done this so that the items in doubt are correctly identified and in the case of non-existent items, are no longer identified at all. It is important to note that as purveyors of parasite applications continue their destructive plight, they will inevitably attempt to change their parasites structure to try to avoid detection. When this occurs we will make every possible effort to decipher their steps quickly and then code the appropriate removal sequence. Inaccurate identifications are inevitable as threats change their character. What we will do is ensure that our system adapts just as fast. All user reports are taken very seriously and we will always work around the clock to resolve customer questions and address each and every product concern.
Identification of items that keep coming back
----------------------------------------------------
We have fixed this. In most cases, there shouldnt be items detected and reappearing after removal. In isolated cases the parasite evil-doers have programmed pests that recreate under a new registry key or program name. There is a constant battle between Parasite removal companies and the unscrupulous pest makers. Often the hackers and parasite developers are well schooled but misguided and perhaps underemployed people looking for a venue to showcase their sometimes impressive skill set. Although we recognize their aptitude, we employ the very best to stay ahead of their tricks. One such trick is to generate an auto regenerating parasite that recreates itself under a new handle every time it is removed. Whenever such an item is identified, we will work with haste to outsmart this code and we will effectively update the product as soon as humanly possible.
Affiliate Domains are associated with Spyhunter/Enigma
------------------------------------------------------
ParetoLogic is not affiliated with Spyhunter, Noadware, Pal Remover Spyware Nuker or any other product. Our marketing efforts currently include advertising from independent affiliates. Affiliates are free to market whatever products they wish. We cannot control what competing products they do promote, but we can and will control the conduct associated with the ParetoLogic and XoftSpy brands. Our principals and ethical practises are under detailed revision and will be strictly adhered to. This includes a Zero spam tolerance and we will not tolerate blatant inaccuracies and claims about our product. We will not pass judgment on other products. We suggest that people download XoftSpy and see for themselves how well we perform. If you find another product that does something you like better, then perhaps that is the product for you, but please let us know what we can do better. We welcome all suggestions for improvement, and we will constantly work to make XoftSpy better, and ideally a product respected and recommended between programmers, developers, software companies and among other industry experts. If you think of something that we could improve, then please just send us an email. You will be impressed with the response, and if at all possible you will see the changes take form. Resorting to misinformed bashing is a tough way to appreciate life. Why not help us and others make a real difference for consumers instead. Send us your suggestions, send us your thoughts. We will make changes and improvements happen. Then decide for yourself if these Internet rants and accusations have substance.
The site is big on ad hype and getting affiliates to sell
------------------------------------------------------
As mentioned earlier, ParetoLogic currently uses Clickbank to process orders and to promote the product to various affiliates and resellers. The network of affiliates advertising XoftSpy expanded rapidly, and consumers learned very quickly of this new entry in the Privacy Software market. Over the last months we have learned of various techniques that affiliates use to increase their market share and to dominate available web advertising space. We are currently investigating these practises, some of which are noted as potentially misleading to the user. We will labor to correct any and all inaccuracies brought to our attention. One such issue cited is that some affiliates use domains containing the word spybot. We fully respect this company and their product name. XoftSpy detects and removes 52 known strings that contain the identifier spybot. This term defines a category, just like spyware, just like adware and just like trojan. However, We will warn and/or terminate the affiliate relationships with any who use the actual '4 word product name', developed by Mr. Kolla, to promote our product. Just let us know
How the reference file of definitions is updated
---------------------------------------------------------------
The XoftSpy Detection system has two components. First of all, a basic definition file. Secondly a threat characteristic analysis algorithm resident in the engine itself. In order to update the definition file, simply click the update button at the top of the XoftSpy product interface. The reference file present on your system is compared to the latest file on our servers. If a new update is available then the users edition is updated. ParetoLogic does not have access to any computer, at any time, unless the user chooses to update the software. We are currently designing a new update module and security features whereby the user is prompted to check for updates and update permissions whenever their system is rebooted or the software is loaded. Again, the program will not check for updates unless the user expressly asks it to. Then a check will be done for a newer file. If a newer file is available the user will be asked if they wish to download the update. The threat characteristic analysis components are part of the actual detection and removal modules and are updated only when the user chooses to download the latest release.
Is ParetoLogic a pyramid scheme?
-------------------------------------------
XoftSpy fixes a ton of malware related computer problems and is rapidly improving by constantly adding new protective features. Upgrades and product enhancements are completely free to registered users. Our product is used and loved by tens of thousands of users. Try XoftSpy yourself, if you dont love it too, let us know why and we will work tirelessly until you do :)
Does XoftSpy do a drive by hijack of the users PC?
---------------------------------------------------------------
No - An uninformed guess as to why a users PC is doing weird things. XoftSpy detects and eliminates such harmful applications. If a user cant find a solution to thwart a hijacker or eliminate an adware app, then we will update the software to protect from the problem. If any user has such an experience with a troublesome pest, then on the interface go to settings and then select show logfiles. This will display a history of the logfiles stored only on your PC. Select the recent file and send it to us on our support page located here http://paretologic.com/support/. We will then study the files, fully research the new parasite profile, find a solution and then update the definition and/or software as required.
An application that popped up out of nowhere and associated with questionable domains
------------------------------------------------------------
As we mentioned earlier the Fast exposure afforded XoftSpy via the Internet and affiliate marketing has been rather startling. We have addressed the concern about the domains earlier; these are operated by affiliates whose websites have promoted different products in the past. ParetoLogic has zero affiliation with any other product or company mentioned.
Automatic re-installation of software
-----------------------------------------------
We are not sure where this question came from. If a user wishes to remove XoftSpy, it is very simple to do. Just go to the start menu -> all programs -> xoftspy -> uninstall xoftspy. Alternatively, just go to Add/Remove programs in the control panel. Select Remove and in a few moments its done. The uninstall is as clean and simple as can be. The only way to reinstall is to manually download the software again. We would be very interested in learning the details of any users experience to the contrary.
How to get a refund
--------------------------------
There are few companies on the Internet that offer a simple no question asked, no hassle and no problem refund policy. We are such a company. If someone wants a refund and they send us an email asking for one, it is done. If they tell us why then we will make changes to improve our product experience. If we are not told why, that is fine too, remember... no question!
If there are any questions or issues not answered here then please feel free to contact us on the support page or through the appropriate email address on the contact page.
Wishing all a trouble free Computer experience Xoftspy is free to see if your PC is infected with known adware, hijackers and many other parasites. In order to remove infections, registration is required for $39.95. This includes Unlimited Lifetime support. Unlimited Lifetime Updates and a 100% Customer Satisfaction Guarantee.
ParetoLogic Inc. is the Developer of the XoftSpy Anti-Adware, Anti-Spyware & Parasite Removal Software.
May 31, 2004
Hotbar Spyware
Hotbar is a program that embeds a toolbar into your browser. It monitors every URL that you visit as well as phrases which you enter into search engines and sends this information back to a third party. The information is used to target ads on your computer, both in popups as well as directly embedded within web pages.
Hotbar consumes over 20MB of disk space on your hard drive. It will slow down your browser, make your PC boot slower, and may crash your computer altogether. Hotbar also disables certain popup blockers.
Hotbar can be forcibly installed when you visit certain websites, whether or not you agree to the download.
Related Links
'Hotbar' spyware program bedevils Windows and should be removed
Hotbar description from Howard University
From the Hotbar terms of use:
"Hotbar works with third party advertising companies to serve ads when you visit our web sites and use the Service, including the toolbars. Two of these third parties are DoubleClick and Engage. Such companies may use information (not including your name, address, email address or telephone number) about your visits to our and other web sites and use of the Service, including the toolbars, in combination with non-personally identifiable information about your purchases and interests from other online and offline sources, in order to provide advertisements about goods and services of interest to you. In addition, we share web site usage information about visitors to our web sites and users of the Service, including the toolbars, with such companies for the purpose of managing and targeting advertisements and for market research analysis on our web sites and the Service, including the toolbars. For these purposes, we and our third-party advertising companies may note some of the pages you visit on our web sites, and through use of the Service, including the toolbars, through the use of pixel tags (also called clear gifs). In the course of serving advertisements, our third-party advertisers may place or recognize a unique "cookie" on your computer and, in some cases, collect data through the use of cookies. To find out more about DoubleClick's information practices and to know your choices about not having this information used by this company, please go to www.doubleclick.net/us/corporate/privacy. To find out more about Engage's information practices and to know your choices about not having this information used by this company, please go to http://www.engage.com/privacy/.
"Hotbar, from time to time, may work with email direct marketers such as Netcreations to offer users the opportunity to subscribe to various email newsletters subscriptions. Please read such marketers' privacy statements before entering your email address or any other information into their subscription window."
May 24, 2004
Claria
Claria is currently the top Adware pest found on the internet. Claria either injects ads into your browser or displays them on their own popup windows.
This spyware program consumes over 13Mb of disk space on average.
Interestingly, Claria is a re-brand of what was formally known as "Gator".
May 14, 2004
Rogue Products: Read Before You Buy
At last count, there are over 345 anti-spyware programs on the market. You will see on our review page that we recommend only two (Webroot's Spy Sweeper and Aluria's Spyware Eliminator).
So why don't we cover the rest? Aside from the sheer volume of copycat software products that offer little or no additional value over these two products, the vast majority of the products on the market are considered "rogues".
Update: XoftSpy was on the rogue list, but we are currently reconsidering this.
Rogues fall into two categories:
1. They claim to remove spyware, but actually install it (and sometimes charge you for their product!)
2. They've stolen their code from another vendor (most notably, from Spybot S&D. This is somewhat funny, as Spybot S&D is not in our opinion a very effective product ... but they are a legitimate software company).
Here's a very good article about one person's experience with rogue products.
Here is a partial list of rogue products. You should NOT purchase any of these products. Buyer beware!
Spy Wiper
AdWare Remover Gold
BPS Spyware Remover
Online PC-Fix SpyFerret
SpyBan
SpyBlast
SpyFerret
SpyGone
SpyHunter
SpyKiller (read review)
SpyKiller Pro
SpywareNuker
TZ Spyware-Adware Remover
SpyAssault
InternetAntiSpy
Virtual Bouncer
AdProtector
SpyFerret
SpyGone
SpyAssault
Pal Spyware Remover
May 13, 2004
What is Spyware?
Spyware has eclipsed viruses as the fastest growing online threat, infecting nearly 90% of Internet connected PCs. If you are like most internet users, chances are you are infected with not just one, but many, of these programs. Simply surfing the internet, reading email, downloading music or other files can infect your PC without you knowing it.
What is spyware?
The term "spyware" generically refers to software programs made by unscrupulous marketing companies that allow them to snoop on your browsing activity, see what you purchase, and cause pop-up ads to appear on your computer.
More specifically, Adware is any software program that causes advertising banners to be displayed to the user. Spyware is any software program that sends data back to a third party without asking you for permission.
Why are these programs a problem?
Spyware causes lots of problems on your PC without you ever suspecting it's there. Have you ever noticed that your computer runs a lot better when you first purchase it than it does months later? The most likely culprit is spyware.
Why should I care?
Spyware ...
* Consumes resources on your PC
* Slows it down
* Causes it to crash
* Interferes with your web browser, slowing it down or causing downloads to fail. It can even hijack your browser, redirecting you and your children to sites with objectionable material
* Slows down your internet connection because while you are surfing, it is sending information about your surfing habits to ad companies, who then target you with popup ads that fit your preferences
* Costs you money - If you are paying for dialup internet access, spyware is literally costing you money.
In short, while spyware is typically not hazardous to your PC, it is annoying and unnecessary. It's the next generation of spam.
How did I get it?
Spyware can infect your system in many different ways: visiting a spy-spreading web site, opening a spy-carrying email attachment, downloading a spy as part of another (often "free") software program, etc. Your privacy, and even your identity, is at high risk if you surf the Internet more than one hour a week, share your computer or use file-sharing programs like KaZaa. Traditional anti-virus programs and firewalls don't offer protection from invasive and harmful spyware programs that can manifest themselves in many ways on your PC.
What can I do?
If you're in a hurry, visit our review page to discover reputable products that will completely protect you against this threat.
Be careful! There are programs out there that claim to stop spyware, but will actually install it on your PC and prevent anti-spyware programs from operating correctly in the future.
Want to know more? Visit our resources page to learn about other sites that will teach you about spyware and keep you informed.